Learn through the super-clean Baeldung Pro experience:
>> Membership and Baeldung Pro.
No ads, dark-mode and 6 months free of IntelliJ Idea Ultimate to start with.
Last updated: March 18, 2024
In the world of cybersecurity, the term “zero-day” refers to a vulnerability or exploit in software or a system that is unknown to the developer or vendor.
This means that attackers can use it to gain unauthorized access to a system, steal data, or cause other forms of damage without being detected by existing security measures. Therefore, this attack exploits a zero-day vulnerability.
In this tutorial, we’ll explore the term “burn a zero-day” and its implications in the realm of cybersecurity.
Burning it means using it for an attack. When a vulnerability or exploit is used in an attack, it becomes known to the security community, and developers can start working on a patch to fix it.
This is because the attack will leave traces that can be analyzed by security experts, who can then reverse-engineer the exploit and create a patch.
The term “burning” is used because once it’s used in an attack, it loses its effectiveness as a secret weapon for the attacker.
The following figure shows the life cycle of a zero-day:
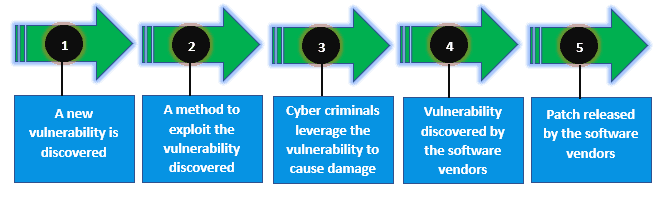
To better understand how this type of attack occurs, we’ll examine the different stages involved in its attack, including identification, creation, intelligence gathering, planning, and execution.
Attackers burn zero days because they are valuable resources. Their exploits are rare, and they can fetch a high price on the black market, where they are sold to other attackers or nation-states for use in cyber espionage or sabotage.
Burning a zero-day is, therefore, a strategic decision, often made in the context of a larger attack campaign. Using it means attackers can cause significant damage and increase their chances of success.
Once it is used in an attack, the vulnerability becomes known to the public, and it can be used by other attackers to launch similar attacks on other systems that haven’t yet been patched.
Therefore, the security community needs to balance the need to develop and use their exploits for defensive purposes with the ethical implications of using them for offensive purposes.
In recent years, there has been a growing trend of security researchers and organizations who develop and sell their exploits to governments and law enforcement agencies, who use them for surveillance and law enforcement purposes. This has sparked debates about the ethics of selling and using their exploits, mainly when they can be used to violate the privacy and security of innocent users.
As zero-day exploits continue to grow, the security community needs to consider the ethical implications and take steps to minimize the harm to innocent users and prevent the exploits from falling into the wrong hands.
Defending against these attacks is challenging but not impossible. One approach is to use security measures that can detect and prevent attacks based on behavior or anomalies rather than relying solely on signature-based detection.
Another approach is to use a layered defense strategy, which involves using multiple security measures, such as firewalls, intrusion detection systems, and antivirus software, to create multiple barriers that attackers must overcome.
Organizations should also keep their software and systems up-to-date with the latest security patches and updates, as these often contain fixes for known vulnerabilities.
In conclusion, burning a zero-day refers to using a valuable and exploitable vulnerability in an attack, often for profit, on the black market.
While defending against these attacks is difficult, organizations can mitigate the risk by using behavior-based security measures, implementing a layered defense strategy, and keeping their software and systems updated with the latest security patches and updates.