Learn through the super-clean Baeldung Pro experience:
>> Membership and Baeldung Pro.
No ads, dark-mode and 6 months free of IntelliJ Idea Ultimate to start with.
Last updated: March 18, 2024
In this tutorial, we’ll discuss the meet-in-the-middle attack (MITM) with a practical example. Furthermore, we’ll present the possible impacts of such an attack.
Finally, we’ll highlight some prevention mechanisms to minimize the impact of the MITM attack.
The meet-in-the-middle attack is a type of cryptanalytic attack commonly used against encryption algorithms that use symmetric keys. Furthermore, the attack takes advantage of the fact that the encryption and decryption processes are inverse operations of each other. Therefore, an attacker follows a brute-force approach to find the secret key we use in the encryption process.
The attack works by dividing the key space into two parts. First, it encrypts the plaintext using all possible keys from one-half of the key space. Additionally, an attacker decrypts the resulting ciphertext using all possible keys from the other half of the key space. Finally, the attacker checks for a match between intermediate values obtained from the encryption and decryption steps.
If a match is found, the key used in the encryption and decryption is in the middle of the key space. By repeating the process with smaller key spaces on either side of the matched key, the attacker can eventually find the secret key used in the encryption. The meet-in-the-middle attack is particularly effective against encryption algorithms with a relatively small key space and vulnerable to exhaustive key search.
Let’s take a look at an example:
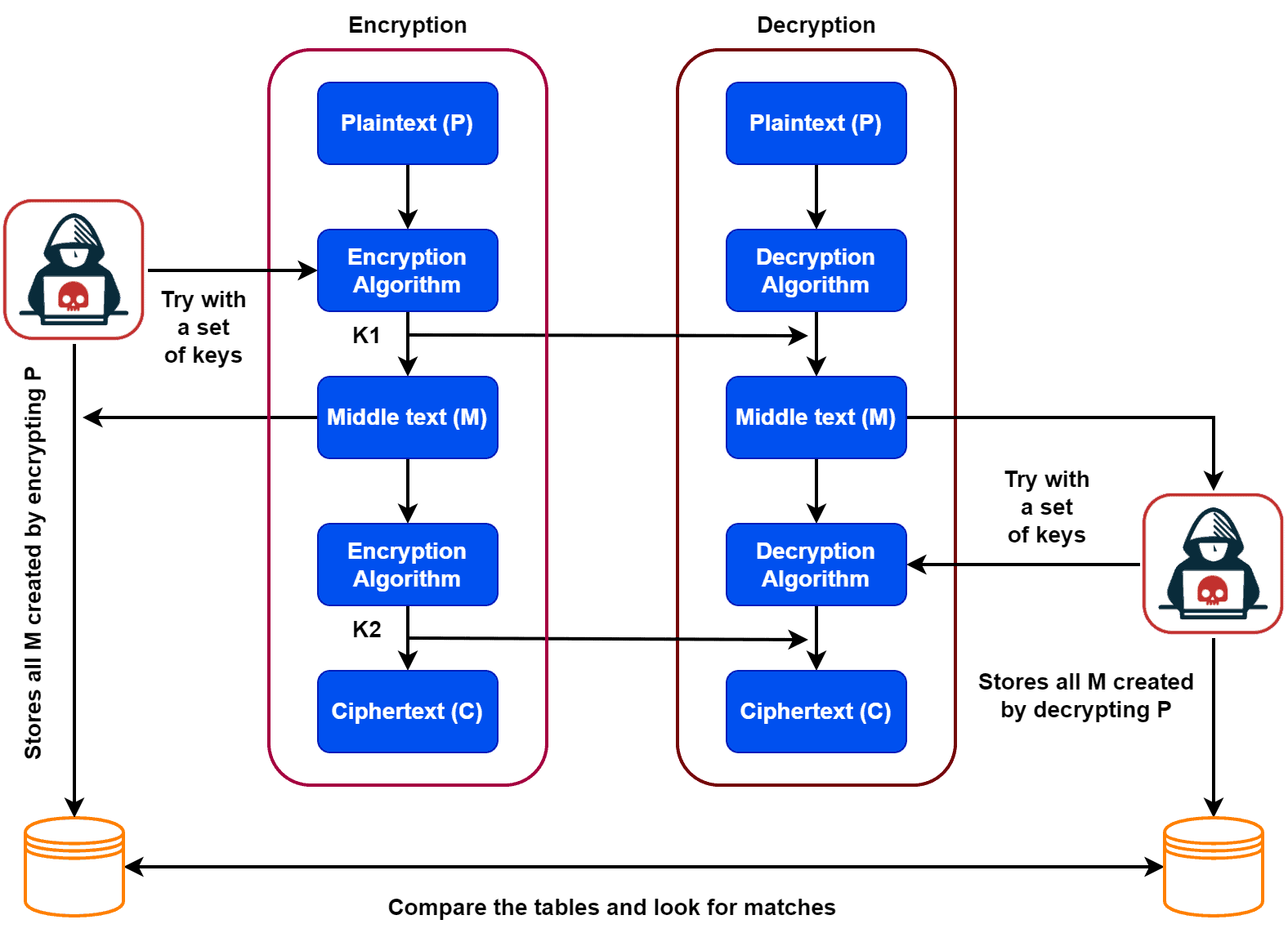
In this example, we use a two-stage encryption and decryption approach. A MITM attacker first tries with a set of possible keys to encrypt the plaintext and stores all the encryption results as middle text messages in a table.
Additionally, in the decryption process, the attacker takes the decrypted middle text messages and applies a set of decryption keys. The resultant messages are stored in a table. Finally, the attacker compares both tables in search of a possible match. In this way, the attacker can generate the secret key used for the encryption and decryption process.
An attacker typically follows five steps in order to implement or launch the meet-in-the-middle attack:
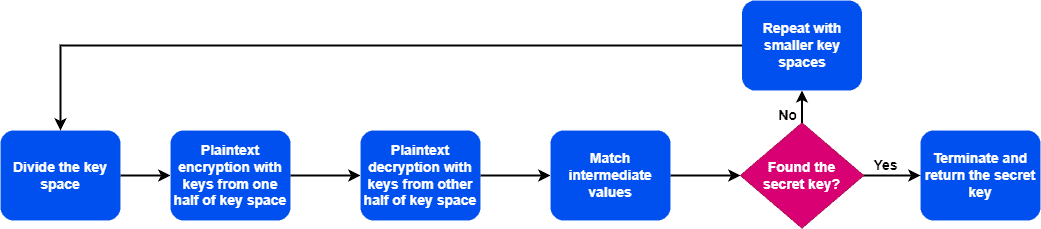
The first step is to divide the key space. The attacker divides the key space into two parts, each containing half of the possible keys. Additionally, the division of the key space is crucial for the attack’s success. The probability of successfully implementing a MITM attack is high if the keyspace is small.
Next, the attacker encrypts the plaintext using all possible keys from one-half of the key space. Furthermore, he stores the resulting intermediate values in a table.
Moving forward, the attacker decrypts the ciphertext using all possible keys from the other half of the key space and stores the resulting intermediate values in a separate table.
The next step is to match intermediate values from two tables. The attacker compares the intermediate values from the encryption and decryption steps to see if there’s a match. If we find a match, the corresponding key is in the middle of the key space.
Finally, the attacker repeats the process with smaller key spaces on either side of the matched key until the secret key used is found.
It’s important to note that the meet-in-the-middle attack requires significant computational power and memory. Therefore, it may not be feasible for encryption algorithms with large key spaces or other strong security measures.
MITM attacks are generally only applicable to block ciphers and may not be effective against stream ciphers. Therefore, MITM attacks can be effective in certain situations, but they’re not a foolproof method of breaking encryption.
The impact of a meet-in-the-middle attack can be significant. Let’s discuss some of the consequences.
The attacker can obtain the secret key to encrypt as well as decrypt messages by launching a MITM attack. This can allow the attacker to decrypt other messages encrypted with the same key.
Furthermore, such an attack can lead to sensitive information being leaked, which can have a range of negative consequences, depending on the nature of the information and who has access to it.
Using a MITM attack, the attacker may compromise the system being used to encrypt and decrypt messages. This can allow the attacker to access the network as well as the systems connected to the network. Furthermore, the attacker can install backdoors to perform malicious actions.
Finally, a MITM attack can damage the reputation of the system or organization. This can lead to losing the trust of users, customers, and partners.
We can use several prevention mechanisms to mitigate the risk of a meet-in-the-middle (MITM) attack. Let’s discuss some essential techniques.
One of the key weaknesses of a MITM attack is that it requires a large amount of computational power to search through a large number of possible keys. By using longer keys, the number of possible keys increases exponentially, making a brute-force search more difficult.
Additionally, some ciphers are more vulnerable to MITM attacks. By using ciphers resistant to MITM attacks, we can effectively reduce the risk of the attack.
In a MITM attack, the attacker seeks a key that decrypts the ciphertext to the plaintext. Therefore, we can use random keys to reduce the probability of the attacker guessing the correct key.
Furthermore, key exchange protocols such as Diffie-Hellman allow two parties to securely agree on a shared secret key without transmitting it. This can make it more difficult for an attacker to intercept the key and launch a MITM attack.
Finally, we can implement message authentication. Message authentication ensures that the message has not been tampered with during transmission. This can make it more difficult for an attacker to modify the message and launch a MITM attack.
In this tutorial, we discussed the meet-in-the-middle attack (MITM) with a practical example. We also presented the possible impacts of such an attack. Finally, we highlighted some prevention mechanisms to minimize the effect of the MITM attack.