Learn through the super-clean Baeldung Pro experience:
>> Membership and Baeldung Pro.
No ads, dark-mode and 6 months free of IntelliJ Idea Ultimate to start with.
Last updated: March 18, 2024
Since its emergence, the Internet moved several activities intrinsically related to the physical world to the digital world. Examples of these activities are from chatting with friends to the commerce of several products.
However, this transition brought different security challenges. Sensitive information is no longer reported with whispers in a locked room, and money is not only paper kept in a safe box. It is all about bits encoded in computer machines transferred through networks.
Multiple security methods have been proposed to deal with the described scenario. These methods, in turn, employ heterogeneous resources to keep data secured from malicious actions. Particular examples of these resources are keys, initialization vectors, and nonces working with cryptography algorithms.
In this tutorial, we’ll study the particular characteristics of these security resources. Our objective is to understand how and where we can employ these resources. Thus, we’ll first have a brief review of general cryptography concepts. Next, we’ll investigate keys, Initialization Vectors (IV), and nonces. Finally, we’ll review and compare the studied resources in a systematic summary.
In short, cryptography consists of methods for securing communications. So, cryptography enables senders and the intended recipients to believe and understand the content of exchanged data.
Typically, we aim to assure the properties of confidentiality, authentication, integrity, and non-repudiation with cryptography. Let’s see a little bit about each one of them:
Cryptography methods got proposed to assure security properties. These methods employ different resources considering various strategies, more or less complex.
In such a way, a simple symmetric encryption method may be enough for given purposes. In other scenarios, however, we must ensure some properties more carefully. So, we can use more complex strategies, such as multi-step and multi-factor authentication methods.
In cybersecurity, a key is a sequence of bytes employed by cryptography algorithms to modify data. Moreover, it is relevant to highlight that cryptography algorithms use keys to encode plain data and decode encrypted data.
In particular, we can point out two scenarios where different keys assume a crucial role: symmetric and asymmetric cryptography.
Considering symmetric cryptography, we have a single key to encrypt and decrypt data. So, keys are secret resources. It means that only authorized people and systems should access them.
The image next exemplifies a generic symmetric cryptography workflow:
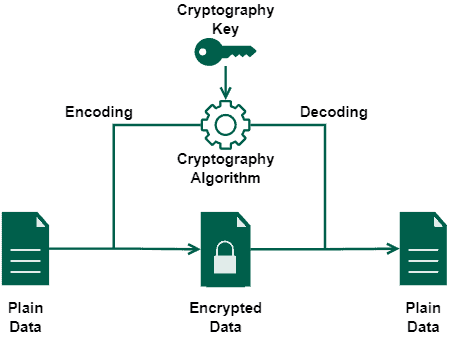
Specific examples of cryptography algorithms that employ symmetric keys are the Data Encryption Standard (DES), Advanced Encryption Standard (AES), and Blowfish.
In the context of asymmetric cryptography, however, we have a pair of keys: one to encrypt data and another to decrypt data. We call these keys of private and public keys:
The private key decrypts data encrypted with the public key of the same pair and vice versa. So, we can assume that only those who have the private key will access the data encrypted with a public key.
The following image shows a simple asymmetric cryptography workflow:
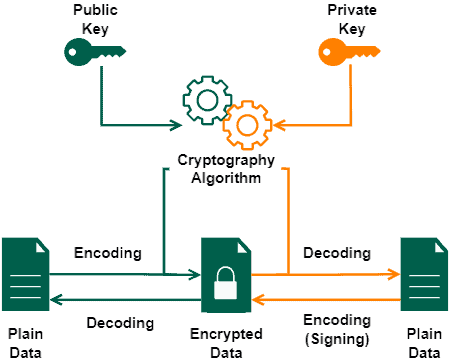
Furthermore, we can also use asymmetric cryptography to sign data. In this case, we use the private key to encrypt the data, allowing everyone with the public key to decrypt it.
We can cite as examples of cryptography algorithms using public/private keys the Digital Signature Algorithm (DSA), Elliptic Curve Cryptography (ECC), and Rivest–Shamir–Adleman (RSA).
In summary, an initialization vector (or starting variable) is a value that provides the initial state of an algorithm. Commonly, this value is random. However, there are scenarios where a unique and unpredictable IV is sufficient.
Cybersecurity has two important use cases of initialization vectors: cryptography hashing and block ciphering.
We have a constant initialization vector defined in the hash function specification of cryptography hashing algorithms. In such a scenario, the IV works as an arbitrary constant indicating the initial hash value (i.e., the initial state).
The following image depicts the use of initialization vectors in cryptography hashing algorithms:
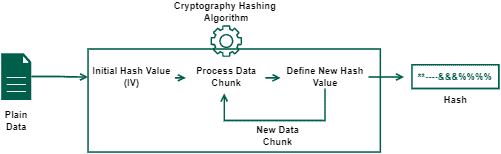
A practical example of a hashing algorithm that uses an IV is the message-digest algorithm (MD5).
Block ciphering algorithms, however, employ initialization vectors to make a single encryption key encode data differently each time it is used. Generally, the IV is random, but sometimes it is okay to have just a unique but not random IV for each message encrypted with a key.
Thus, the initialization vector enables the same key to generate different ciphertexts even when the same plain data is processed multiple times, providing a semantic secure cryptosystem.
The image next exemplifies the described process of block ciphering algorithms:
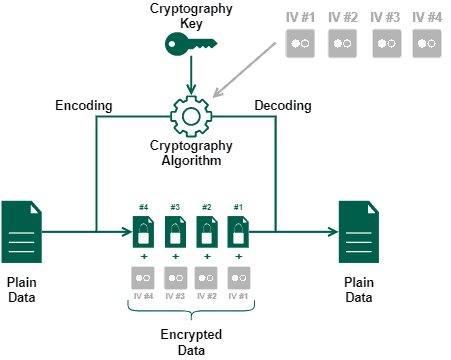
Regardless of the use case, initialization vectors are not a secret resource. As we saw in the previous examples, there are scenarios where providing the IV together with the encrypted data is crucial for executing a later decryption process.
In cybersecurity, nonce means data used only once. Thus, the only property that we should assure when working with nonces is that, after using them, they become unavailable resources, not working a second time for the same purpose.
In this way, we can also call, by definition, the unique initialization vectors used for block ciphering a nonce.
Moreover, it is possible to employ nonces in cryptographic communications. In such a case, the main purpose of a nonce is to avoid the execution of replay attacks.
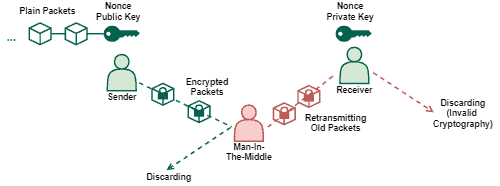
A replay attack interferes in communications between legit entities to maliciously retransmit valid but old messages. In most cases, executing a replay attack demands a previous execution of a man-in-the-middle attack.
However, if there is a nonce validating the communication, or if the cryptography key itself works as a nonce, replay attacks will not work since the retransmitted messages will be outdated.
The following image depicts the previously presented scenario of replay attacks:
The popularization of the Internet progressively moves several activities to the digital world. Working, communicating, and shopping are examples of everyday life activities that, now, are frequently done through a networked environment.
This scenario changed how we face the relationships between, for example, customers/salespeople and employees/employers. Furthermore, it also brought concerns on how to guarantee authenticity and security for the people interacting in the digital world.
In this way, researchers proposed security-related strategies to solve the previously cited concerns. One of the most useful proposed strategies is employing cryptography in communications.
Cryptography algorithms, however, may require different resources to work properly or improve security levels. Relevant resources are keys, initialization vectors, and nonces.
Keys are essential resources to enable the execution of cryptography algorithms, making them able to transform data.
Initialization vectors, in turn, play a relevant role in determining the initial state of algorithms and improving the variability of results obtained with a single cryptography key.
Finally, nonces usually tackle the recency of a request or communication since this resource is used only once before becoming outdated.
The following table compares some characteristics of keys, initialization vectors, and nonces:
| Key | Initialization Vector | Nonce | |
|---|---|---|---|
| Brief Definition | Sequence of bytes employed by cryptography algorithms to modify data. | Value that provides the initial state of an algorithm. | Data used only once. |
| Secret Resource | Public Key: No Private Key: Yes | No | No |
| Application Examples | Cryptography Algorithms (AES, DES, ECC, RSA, …) | Cryptography Hashing (MD5, …) Block Ciphering | Authentication of Communications |
In this tutorial, we studied keys, initialization vectors, and nonces resources. First, we briefly reviewed cryptography, the most popular application scenario of the resources investigated. So, we specifically explored the concepts and applications of these resources. Finally, we compared keys, initialization vectors, and nonces in a systematic summary.
We can conclude that the studied resources play a crucial role in modern computing, allowing the secure execution of sensitive operations in networked systems.