1. Overview
In this tutorial, we’ll discuss three memory-related concepts in the operating system: private bytes, virtual bytes, and working sets.
Finally, we’ll discuss the core differences between them.
2. Private Bytes
Private bytes are the reasonable approximation of the amount of memory an application requests during or before execution. Specifically, when a process completely exhausts its private memory, private bytes indicate the amount of RAM allocated to a process by the operating system. However, an important aspect of the private byte set is that it always indicates the memory allocated, not the memory used by the process.
A process utilizes the private byte set in order to request RAM from the OS. Although, the process may or may not use the whole allocated memory. We don’t include memory-mapped files in the private bytes set. It can consist of physical as well as disk memory.
We can use a private byte set to monitor and analyze any continuous increase in private memory. For instance, an allocation request in an unwanted infinite loop of an application may lead to a memory leak in the system. We can identify a memory leak by monitoring the continuous increase in the application’s private byte set.
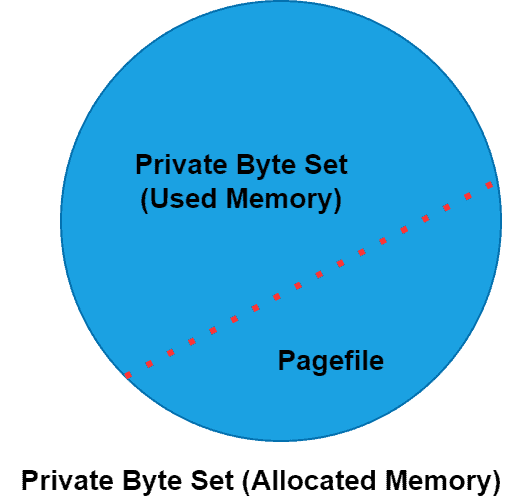
In a private byte set, processes don’t share the requested memory with other processes. Additionally, processes don’t use the whole requested memory during execution. Moreover, a process’s private bytes include its pagefile usage. A pagefile is a reserved portion of hard disk memory that the OS has not used for a long time.
Therefore, the actual allocated memory of the private set is the sum of the memory used for the private byte set and pagefile memory:
3. Working Set
During the execution of an application, we can view the working byte set as the pages of a process currently present in physical memory. A working set contains the most recent pages in RAM that have been allocated by a specific process.
However, if a process requests a page that has not previously been loaded in physical memory, an error occurs. The error leads to a page fault in the system. Additionally, we can explore the missing pages using the page fault handler. Nevertheless, after finding the missing page, we can include it in the working set. Therefore, in such a case, the total size of the working set will be increased by the amount of the newly added page’s size. We can divide page faults into two categories: hard and soft page faults.
We can resolve hard page faults by reading the paging file or memory-mapped file created by the process that requested the faulty page. The system reads the content of the backing store files to retrieve the desired page’s content. After the retrieval, we add the page to the working set.
Soft page faults don’t require reading backline store files. It can occur in a variety of situations. Let’s discuss some of them. Let’s assume a page is being executed within another working set of another process. In such a case, soft page fault can occur. Additionally, a page that is in transition after leaving a working set of a process can also lead to soft page fault.
If a process is completed using one of the working set pages, the page will be removed from the set without affecting the remaining processes. If a page is not a part of any working set, it’s referred to as a transition page until it is requested or modified for another purpose.
Unlike the private byte set, the working set can include both non-paged private bytes as well as memory-mapped files.
4. Virtual Bytes
Virtual byte set refers to the virtual memory address space allotted to a process. It facilitates the freedom of usage where a unique process accesses every space of addresses. The virtual addresses don’t represent the current physical memory position. However, every process is accompanied by a page table that helps in the translation of virtual addresses into their corresponding physical addresses. When a process requests an address, the system responds with a physical address based on the page table.
We can extend the physical RAM using secondary storage and virtual spacing. This virtual memory exceeds the capacity of RAM to get more address spacing and referencing addresses than the actual real memory. Let’s take an example. In 32-bit Windows user mode, a process can use a maximum of 2GB. However, we can expand the allocated memory to 3GB by modifying the Boot.ini file.
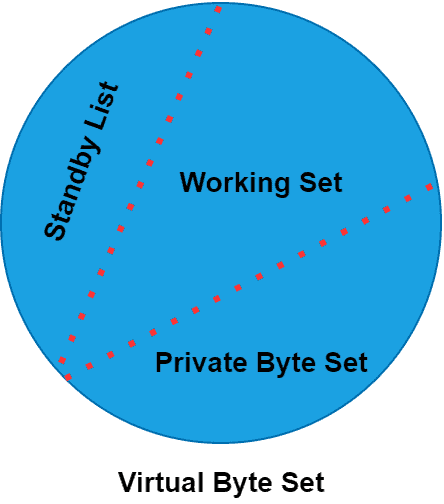
Virtual byte sets can include non-paged private bytes, memory-mapped files, and the data on a disk. Finally, the virtual byte set is a combination of the working set, private bytes, and a standby list:
5. Differences
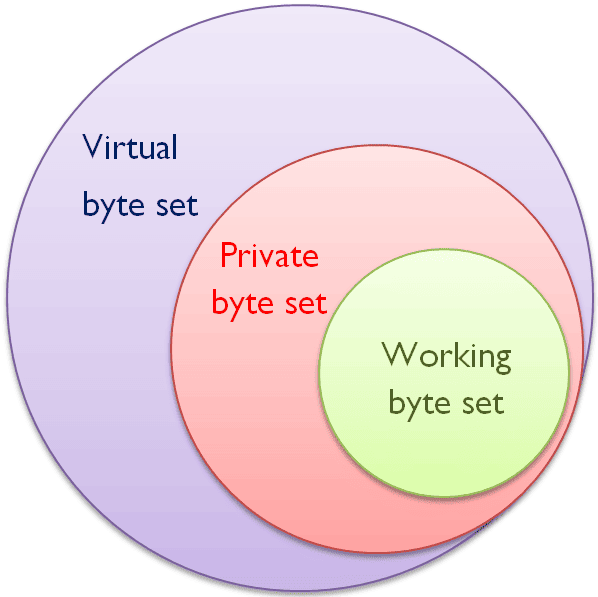
We can define the virtual byte set as the sum of the working set and private bytes. Additionally, the private bytes set is the sum of allocated memory and page usage memory of a process. Therefore, the private byte set is the superset of the working set. Furthermore, the virtual byte set is the superset of private byte and working sets:
Now let’s take a look at the comparisons between the three sets:
6. Conclusion
In this tutorial, we explored some memory-related concepts in the operating system: private bytes, virtual bytes, and working sets.
Finally, we presented the core differences between them.