Yes, we're now running our Black Friday Sale. All Access and Pro are 33% off until 2nd December, 2025:
What Is Identity and Access Management?
Last updated: April 22, 2024
1. Introduction
Modern information security relies heavily on identity and access management (IAM). IAM ensures that only authorized users can access IT assets at the right time and for the right reasons.
In this tutorial, we’ll discuss why IAM is important, its basic types, advantages, and difficulties, as well as recommendations regarding its use.
2. Why Do We Need IAM?
Due to the increasing use of work-from-home and cloud-based security, maintaining identities and role-based privileges has become increasingly important to improve security. Among other things, we need to:
- streamline the authentication and authorization process
- allow only authorized users to access sensitive data and infrastructure
- meet legal requirements on data and privacy using a clear audit trail
IAM does precisely that. It provides an extensive framework that includes rules, methods, and technology for managing user identities and controlling user access inside an organization:
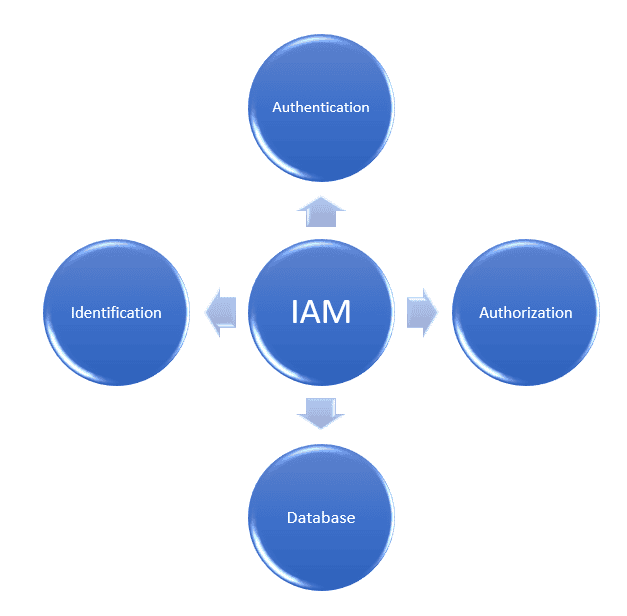
The IAM framework manages all aspects of one’s identity and stores all user-specific information in a central database. Authentication verifies a user is who they claim to be, whereas authorization grants access rights to a specific person or kind of user.
As a result, IAM prevents information breaches through robust authentication systems and tracking user activities to detect and respond to abnormal behavior.
3. What Are the Core Components of an IAM Framework?
Let’s check the basic flow of IAM:
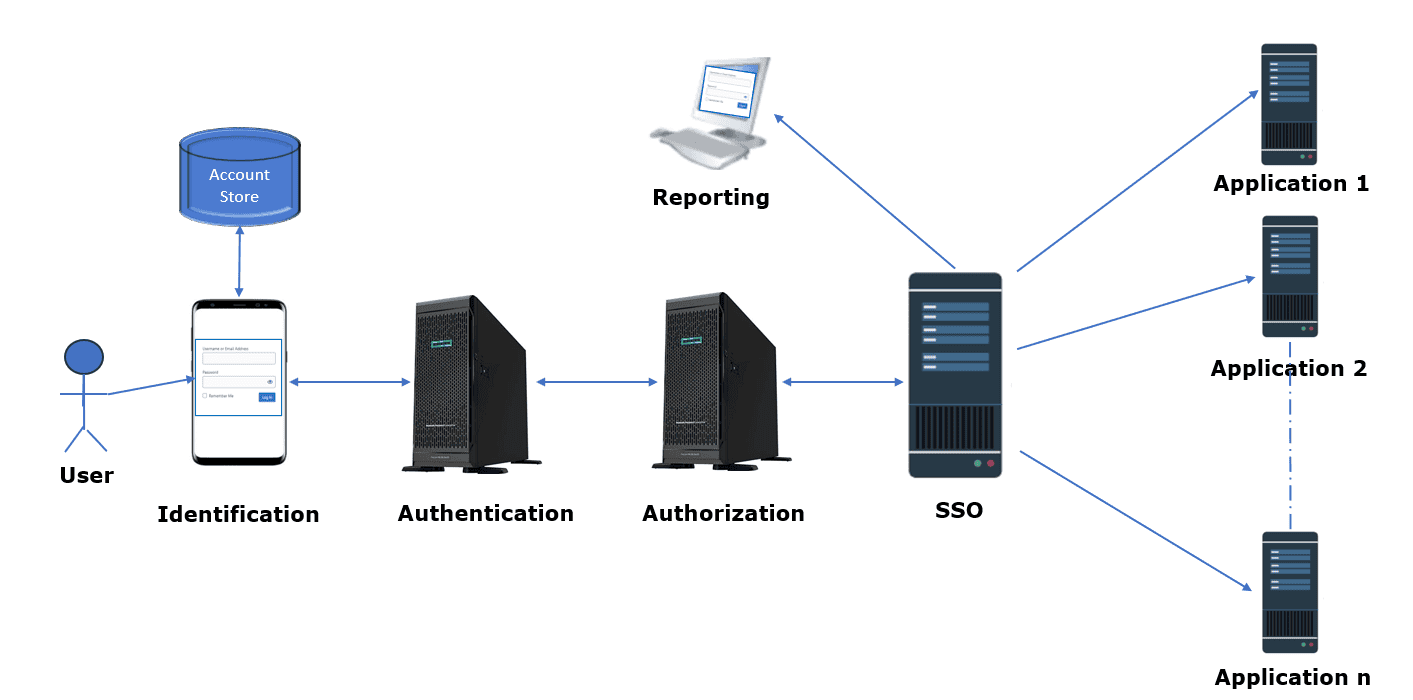
In addition to authentication and authorization, IAM provides identification, reporting, and single sign-on (SSO) to help with effective monitoring and usability.
3.1. Identification
Identification means that a user presents a digital identity to an IAM system by logging in. Every user or entity in an organization has a distinct digital identity. We create an identity when onboarding a new employee or a partner, which is called provisioning. Similarly, deleting someone’s account is called deprovisioning.
Identification establishes a user’s identity and is the foundation for subsequent IAM operations such as authentication and authorization.
3.2. Authentication
After identification, IAM checks the user’s credentials to verify that the user presented their own identity rather than someone else’s:
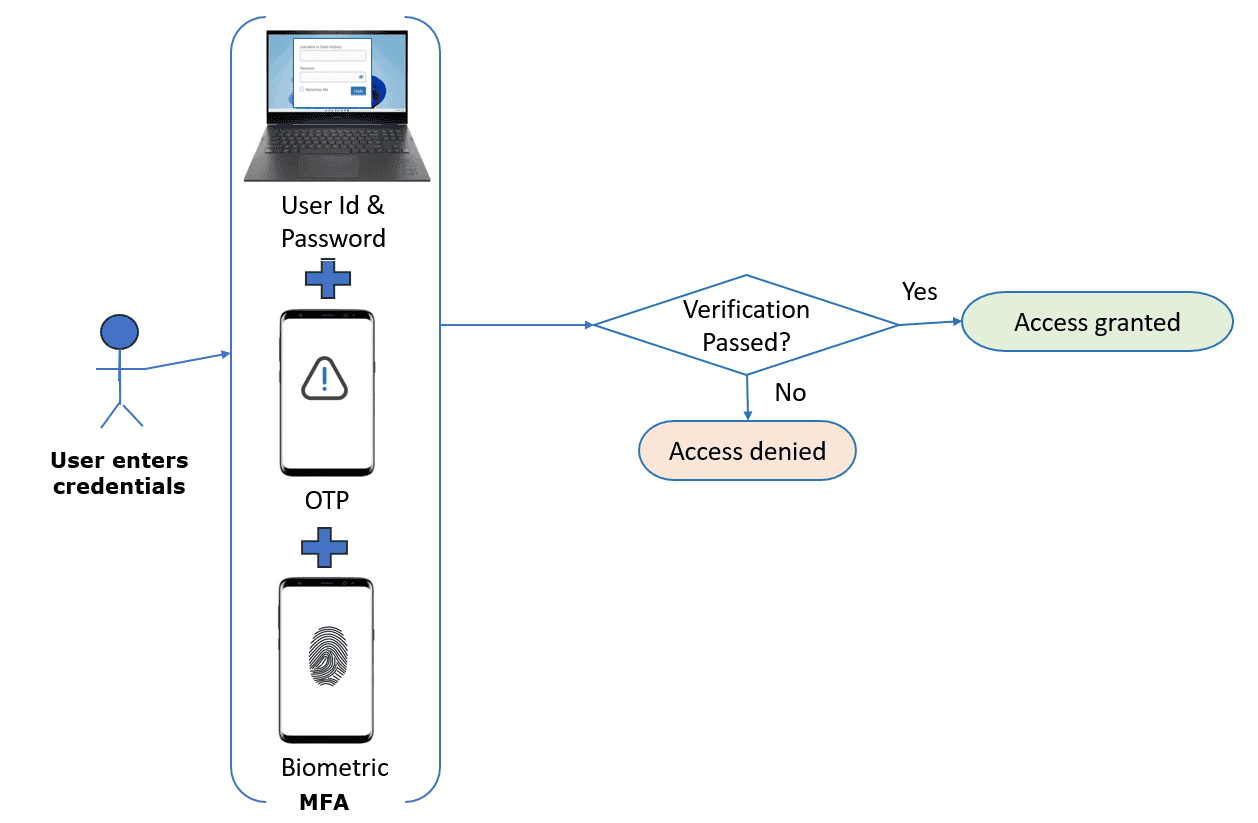
Several technologies, including directory services, single sign-on, and multi-factor authentication (MFA), are integrated with IAM systems to simplify the authentication process. MFA also includes a one-time password (OTP) and the biometric verification process.
3.3. Authorization
After the authentication steps, users get permissions based on their roles within an organization:
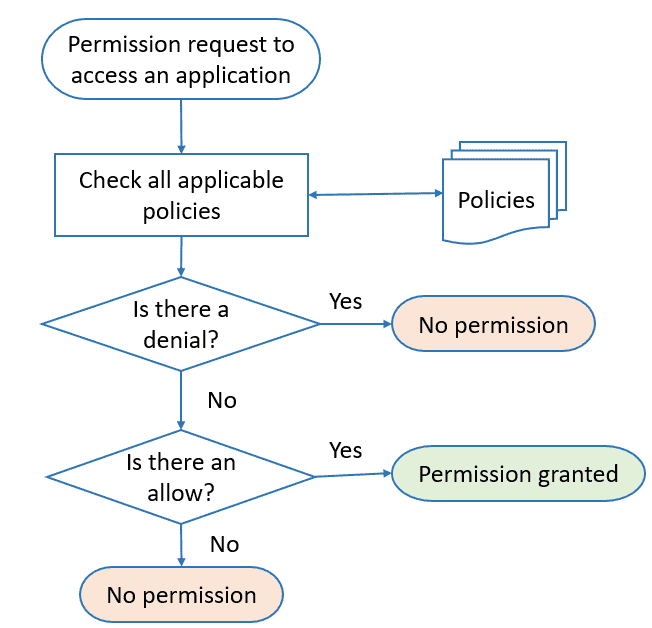
Let’s first clarify the policies in the above figure. They are rules for accessing a digital asset based on user role, department, region, and time. For example, a policy can be “Allow users to manage their credentials on their profile page.”
The flow is like this. A user requests permission to access an application. IAM refuses permission if a policy prevents the user from accessing the system. It returns a denial decision, and the authorization procedure stops. For example, the system will deny access if a user wants to edit another user’s profile.
If no policy results in a denial of the request, IAM checks if the user’s roles specify the user is allowed to do what they asked. So, if the system identifies an appropriate permission, it gives an “access granted” decision, and the authorization process terminates. In the above example, the system will provide access if users want to edit their profile page.
If no permission is found, the system produces a denial decision, and the authorization process stops.
How is this different from authentication? The difference is that authentication determines who a user is, while authorization determines what the user can do.
3.4. Reporting
Reporting is about documenting and recording users’ actions and auditing and monitoring them.
Reports help organizations comply with regulatory requirements, identify and address possible risks to security, and continuously improve their operations.
There are several report types:
| Report Type | Description |
| Identity verification | This report shows authentication methods such as passwords, fingerprints, or MFA. |
| Access privileges | A comprehensive document listing all the permissions granted to users in IAM. IAM administrators can review and verify all users’ access rights with it. |
| Activity monitoring | Here, we track user actions in real time to ensure compliance with security guidelines. This includes monitoring login times, session durations, and the precise resources accessed. |
| Audit Trails | IAM keeps detailed records documenting activities that lead to a particular state or event within the system. This is critical for detecting unauthorized access and conducting forensic investigations in the case of a security breach. |
| Compliance reporting | IAM systems assist organizations in meeting regulatory requirements by creating reports detailing who accessed what information, when, and from where. |
| Automatic notifications | In the event of an anomaly or unauthorized access attempt, IAM can automatically notify managers, allowing them to take prompt action to prevent danger. |
| Provisioning and deprovisioning | This report provides insight into the effectiveness of the user creation and deletion processes, highlights potential security risks, and ensures regulatory compliance. |
3.5. SSO
Single Sign-On (SSO) is a technique for authenticating and authorizing users across numerous apps using a single password.
Using SSO eliminates the need for users to remember multiple passwords. Properly deployed, SSO increases security and eliminates risks associated with inadequate, repeated, or stolen credentials.
IAM systems can assist organizations in implementing SSO across numerous apps. Open standards such as OAuth 2.0 and OIDC enable users to authenticate for apps using an identity provider, including those outside the organization.
SSO relies on social login, which allows users to access applications using their current identities for sites such as Google, Facebook, and X.
4. Key Drivers of IAM Technologies and Solutions
Let’s now discuss the key drivers of IAM.
4.1. Security
One of the primary reasons for implementing IAM is to manage access, which prevents fraud and unauthorized access to critical information.
It can prevent unauthorized logins and defend against phishing attempts (among other cyber threats). It also includes correct reporting, irrespective of the use, system, or decision, allowing for greater location flexibility.
4.2. Adherence to Standards and Compliance
Keeping assets safe is only one goal of IAM; adhering to regional legislation is also crucial.
By establishing strict protocols for controlling what and how users can access networks and resources, IAM ensures compliance with HIPAA, PCI, GDPR, and other regulations.
4.3. Cost Reduction
If the organization-wide accepted policy, such as the “password policy,” is modified, it can be done in one step using IAM.
As a result, IAM can reduce the IT team’s workload. Furthermore, it can decrease administrative burdens related to onboarding, offboarding, and creating policies and processes.
4.4. Better User Experience
IAM assists with implementing the SSO function, which has become quite popular among corporations. SSO eliminates the need for users to type passwords while accessing various systems.
5. What Are Common Challenges in IAM Deployment?
Common challenges in IAM deployment include:
| Challenges | Reason |
| The ever-changing number of users | New hiring, role shifts, and layoffs affect access rights and privileges |
| Role-based access control (RBAC) | Defining roles and changing access privileges when job responsibilities change is a complex process that requires a streamlined approach |
| Lack of proper planning | Without a clear plan, IAM deployment can encounter severe roadblocks that prevent successful implementation. |
| Cloud considerations | With the growing use of cloud-based services, controlling access in the cloud offers new issues. |
| Future-proofing | IAM solutions must be developed for the future, taking into account anticipated technological and business process changes |
| Regulatory compliance | Compliance with rules such as GDPR and CPRA is a regular concern, particularly when handling data in the cloud. |
| Data encryption and security | Ensuring data security in transit and at rest within cloud settings is a vital component of IAM. |
| Legacy application integration | Working with several old identity and data storage deployments might result in redundant tools and inconsistent user experiences. |
A multifaceted approach is necessary to overcome IAM implementation challenges. This involves strategic thinking, stakeholder involvement, and implementing IAM solutions flexible enough to adapt to changing digital environments.
6. Advantages vs. Disadvantages
Let’s now discuss a few advantages and disadvantages of IAM deployment:
| Advantages | Disadvantages |
| Enhanced security – IAM offers strong security safeguards to defend against hacking | Complexity – IAM requires significant investment in technology and qualified individuals |
| Supports collaboration – It is simple to collaborate with other businesses and individuals. | Working in silos – IAM creates divisions, resulting in unequal IT policy compliance and vulnerabilities. |
| Compliance – IAM meets compliance standards by applying the least privilege rule | Operation hurdle – IT teams can experience operational problems due to the changing nature of IAM |
| Improved user experience – IAM makes it easier to obtain the permissions to execute tasks | Resource Intensive – Implementation is time-consuming and requires ongoing monitoring to stay up with threats. |
IAM systems provide various benefits, including improved data security, collaboration and productivity, compliance, user experience, and centralized control. These advantages are critical in a digital workforce, especially given the expansion of remote working roles, which raises the risk of data breaches.
While implementing an IAM system requires significant investment and work, the benefits often outweigh the dangers.
7. Conclusion
In this article, we discussed IAM, which stands for identity and access management. IAM is about ensuring users access only those assets they can use.
Implementing an efficient IAM approach may increase productivity, lower IT expenses, and strengthen security postures, but it comes with challenges.