Learn through the super-clean Baeldung Pro experience:
>> Membership and Baeldung Pro.
No ads, dark-mode and 6 months free of IntelliJ Idea Ultimate to start with.
Last updated: March 18, 2024
In this tutorial, we’ll cover deauthentication attacks over networks. We’ll see what exactly a deauthentication attack is, what it consists of, how it’s performed, and how to keep our systems and data safe from it.
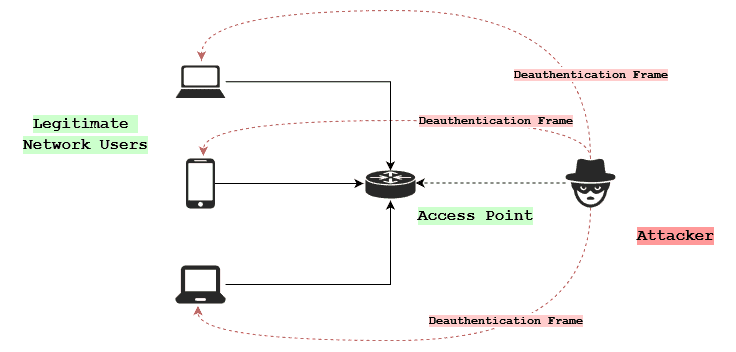
A deauthentication attack is a type of Denial of Service (DoS) attack and refers to an unauthorized disruption of the connection between a wireless device and its access point.
By sending forged deauthentication or disassociation frames, an attacker can force devices to disconnect from the network, leading to a temporary loss of connectivity. These frames are part of the IEEE 802.11 Wi-Fi standard. We use them to terminate a connection or signal that a user wants to voluntarily disconnect.
The 802.11 protocol, used mainly in network communications, considers deauthentication packets as legitimate. Such packets may be actually needed when the system needs to disconnect a device from the network for a legitimate reason, such as system failure or detecting a compromised device.
Deauthentication attacks exploit vulnerabilities in the authentication and handshake process of wireless protocols, allowing attackers to bypass security mechanisms and disrupt network communications. These attacks can have serious implications, including unauthorized access to the network, interception of sensitive information, and the potential for further malicious activities.
The attack involves sending deauthentication frames to target devices, causing them to disconnect from the network and temporarily denying them access.
Then, the attacker’s device, which monitors the wireless network traffic, tries to capture the MAC addresses of the target devices. MAC addresses are unique identifiers assigned to each network interface on a device and can therefore be used to identify devices.
After crafting the frames for a specific device on the network, the attacker sends a flood of deauthentication frames to the target devices. The frames are typically sent at a high rate, overwhelming the network and forcing devices to disconnect.
When a target device receives a deauthentication frame, it interprets that as a legitimate disconnection request from the access point it’s connected to. As a result, the device disconnects and usually attempts to reconnect to the network. Attackers want to exploit this automatic reconnection attempt step.
Depending on the motivations behind the attack, the attacker may continue sending deauthentication frames periodically to maintain the disruption, preventing the devices from successfully reconnecting to the network.
Let’s take a closer look at the flow of such an attack. First, the intruder identifies and connects to a network:
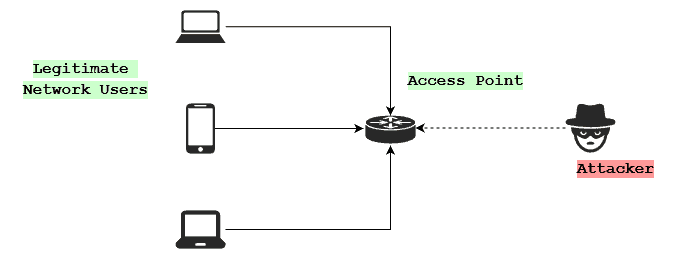
After connecting, the attacker identifies the target device on the network. That’s the device they’ll try to disconnect. They send it a deauthentication frame spoofed to appear like a legitimate request from the network:
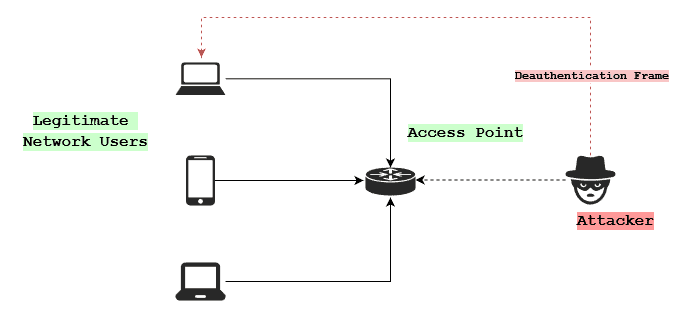
The device disconnects from the network after getting the request. In most cases, due to device and network configurations, it will immediately try to reconnect. The reconnection initiates a handshake between the device and the access point:
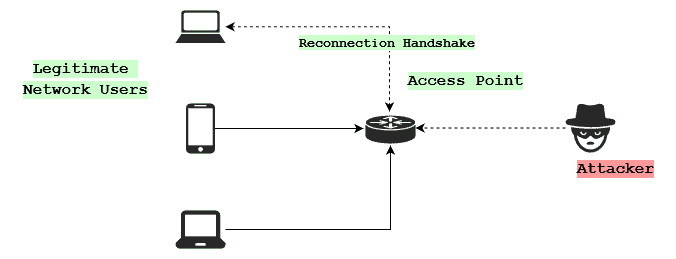
The reconnection handshake contains sensitive data that can be useful to an attacker. Depending on encryption protocols, this data could be read by anyone or easily cracked. This handshake is usually the piece of data that attackers are after. Attackers store a number of those handshakes and try to crack them offline, even if the data is encrypted:
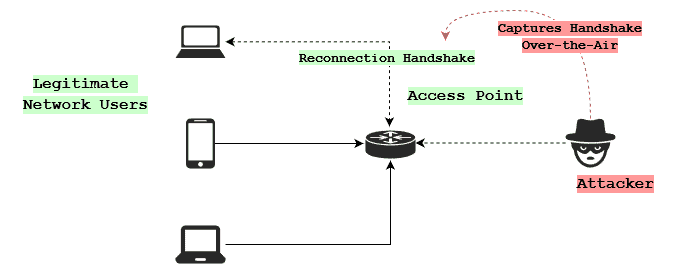
There’s also the possibility an attacker wants to wreak havoc on the network. In that case, they flood the network with deauthentication frames:
Almost every deauthentication attack that happens out in the wild roughly follows these steps. There are, however, deviations depending on the device and network specifics, as well as the attack’s motives.
In a typical use case, an attacker disrupts a device and captures data transmitted during the device’s reconnection to the network. An attacker may capture the handshake and try to crack it offline to get the Wi-Fi password and other transmitted information.
Another example is using a deauthentication attack to make a device disconnect and try to connect a malicious device in its place. This would, in turn, open up possibilities for further tampering with the network.
Deauthentication attacks can also be used to disturb the network quality as a Denial of Service (DoS) attack. By not letting devices smoothly connect and operate a network, an attacker can greatly affect the utility of wireless networks and decrease their service quality. Public access points are particularly lucrative as a target for these attacks due to their easy accessibility and large audiences.
We can categorize the measures as those regular users can take and those we can take as network administrators and designers.
Unfortunately, there aren’t a lot of things we can do as users during such attacks taking place against us, so the key is to be careful and try to prevent them before happening.
We should use strong security protocols and regularly update our firmware and software. This includes our routers and home network equipment. As always, strong protocols and up-to-date software can save us a lot of headaches. Additionally, we should be extremely cautious when using public Wi-Fi.
However, for extra security, we can disable automatic network connections. As a result, our devices won’t automatically generate the handshake information with the network. This demotivates some attackers from attacking us.
We may also pick up hints for attempted attacks on our network by monitoring our devices.
Finally, we should be using a VPN (Virtual Private Network) over our connection to make it even more difficult for malicious attackers to interfere with our now-encrypted packets and data.
Network administrators have many countermeasures at their disposal. The main thing a network admin should look for when setting up a network is setting up strong authentication mechanisms, as these are the first line of defense against deauthentication attacks. WPA3 is a great example of such a strong protocol and can make it much more difficult and time-consuming for attackers to capture and crack any kind of data.
Admins should also look to employ some IDS (Intrusion Detection System). IDS software alerts admins to any suspicious activity on the network. Deauthentication attacks usually generate a large amount of traffic on a network, and IDS software is more than capable of detecting that.
Generally, admins should always keep all software and firmware up-to-date. Firmware that runs on crucial network infrastructure, like central routers and access points, is especially important. Admins must also take care of software updates regularly coming out and keep all devices on the network updated.
Finally, we can employ three more advanced methods. Those are rate limits, RF frequency monitoring and client isolation. These methods are more advanced and aren’t used specifically against deauthentication attacks, but for broader network monitoring and security.
Rate limiting puts a limit on the number of deauthentication frames that can be sent per second network-wide. RF monitoring checks the packets sent over the air for suspicious activity. Finally, client isolation uses software techniques (sometimes with hardware support) to ensure the isolation of data between devices on the network, as with the common usage of VLANs (Virtual LANs).
In this article, we talked about deauthentication attacks.
Deauthentication attacks are a type of denial-of-service attacks that disconnect devices from a network. The motive is either capturing reconnection handshakes or diminishing the network’s quality of service. These attacks use deauthentication frames to execute. The most important countermeasures are using strong protocols and authentication mechanisms and keeping all our software up-to-date.