Learn through the super-clean Baeldung Pro experience:
>> Membership and Baeldung Pro.
No ads, dark-mode and 6 months free of IntelliJ Idea Ultimate to start with.
Last updated: March 14, 2024
In the realm of cybersecurity, SSH (Secure Shell) keys serve as a cornerstone for secure communication between computers. However, managing SSH keys, especially when they are passphrase-protected, can be a cumbersome task.
In this tutorial, we’ll explore how to utilize graphical prompts effectively for SSH key passphrase entry, accompanied by practical illustrations.
Mastering SSH key passphrases is essential for ensuring secure authentication and access to remote servers. In this section, we’ll explore the role of SSH key passphrases and the challenges associated with manual passphrase entry.
First, let’s recap the role of SSH key passphrases. SSH keys consist of a public key, a private key, and a passphrase that protects the private key. This passphrase acts as an additional layer of security. This, in turn, ensures that only authorized users can access the private key and subsequently authenticate with remote servers.
Typing in passphrases manually in the terminal can be cumbersome, especially if the passphrase is long and complex. Moreover, manual entry poses security risks, as passphrases may be susceptible to keyloggers or other forms of malicious software.
Graphical prompts provide an intuitive and secure alternative to alleviate these challenges. Tools like ssh-askpass provide a graphical prompt that appears on the screen at the time of passphrase authentication. So, instead of typing the passphrase, users interact with a graphical interface to input the passphrase securely. This reduces the risk of interception by keyloggers.
By leveraging graphical prompts like ssh-askpass, users can overcome the challenges of manual passphrase entry in the terminal. Unlike manual passphrase entry, graphical prompts provide a secure interface for passphrase entry. Authenticating via SSH thus improves the overall user experience.
In this section, we’ll dive deep into using the ssh-askpass utility to enable a graphical point for SSH key passphrase. But first, let’s discuss the role of the DISPLAY environment variable and how to set it up.
The DISPLAY environment variable specifies the X11 display server that graphical applications use to render the user interface. For graphical prompts like ssh-askpass to function properly, we must correctly set the DISPLAY variable to point to the user’s display environment. Typically, we must set the DISPLAY variable to :0.0 for the default local display. But, it may vary depending on the user’s system configuration.
Enabling X11 forwarding is another important condition for setting up a graphical prompt for the SSH key passphrase. If we enable the DISPLAY variable correctly but don’t enable X11 forwarding, the graphical prompt may fail to appear. Therefore, we must set X11Forwarding to yes in the SSH server configuration file (/etc/ssh/sshd_config):
X11Forwarding yesWe can also enable X11 forwarding by using the -X or -Y option with the ssh command:
$ ssh -X user@hostname
$ ssh -Y user@hostnameOne common tool for implementing graphical prompts is the ssh-askpass utility. We can typically find ssh-askpass in Linux distribution’s package repositories and install it using the Linux package manager.
Let’s take a look at a command that updates the package lists to make sure that we get the latest version of ssh-askpass:
$ sudo apt updateOnce the package lists are updated, we may use the following command to install ssh-askpass:
$ sudo apt install ssh-askpassAfter installation, we can verify the ssh-askpass installation by simply running the ssh-askpass command:
$ ssh-askpassThis should launch the ssh-askpass graphical prompt. Once installed, ssh-askpass will be available system-wide. Thereafter, SSH clients will automatically use it when a graphical passphrase prompt appears during SSH key authentication.
Now, to initiate an SSH connection, we specify remote server details with the ssh command:
$ ssh user@skinnerThis way, when SSH encounters the passphrase-protected key, it triggers the graphical prompt provided by ssh-askpass. A dialog box appears, prompting us to enter the passphrase:
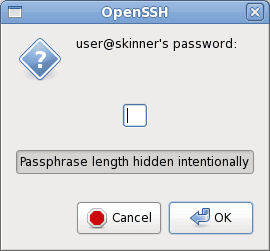
By clicking on the dialog box, we input the passphrase securely without worrying about keyloggers capturing the keystrokes.
Once we’ve entered the passphrase, SSH proceeds with the authentication process as usual, using the provided passphrase to unlock the private key.
An important comment on the SSH manual page states that if SSH lacks a terminal association but has DISPLAY and SSH_ASKPASS configured, it will execute the program specified by SSH_ASKPASS. This action will open an X11 window to input the passphrase.
The crucial point to grasp here is that SSH must lack a terminal association when DISPLAY and SSH_ASKPASS are set for SSH_ASKPASS to be utilized. Thus, we must detach SSH from our terminal. It means that SSH should not have STDIN and STDOUT attached to it.
One approach to accomplish this is by utilizing the setsid command, which runs a program in a new session:
$ setsid ssh user@remotehostWhen we run the ssh “program” with setsid, we detach SSH from our terminal, meeting the criteria specified on the SSH manual page. Additionally, we must ensure that DISPLAY and SSH_ASKPASS are properly configured. So, although setsid might be unfamiliar, it serves our purpose well.
Bugzilla Bug 69 is a reported issue highlighting a vulnerability in the way ssh-askpass handles passphrase prompts. It exhibits so, particularly when used in conjunction with X11 forwarding.
The vulnerability stems from the fact that ssh-askpass does not verify the origin of the X11 forwarding connection. Therefore, it allows an attacker with control over the X11 server to intercept passphrase prompts. This poses a security risk as it enables potential passphrase interception, especially in shared or untrusted X11 server environments.
The bug report suggests that ssh-askpass should implement additional security measures. This includes validating the X11 forwarding connection and ensuring that passphrase prompts are displayed securely. This may further involve verifying the authenticity of the X11 server or implementing stronger authentication mechanisms for passphrase entry.
Overall, Bugzilla Bug 69 underscores the importance of addressing security vulnerabilities in graphical passphrase prompt utilities like ssh-askpass. The bug fix thus safeguards SSH authentication processes and mitigates the risk of passphrase interception in X11 forwarding environments.
In this article, we not only discussed tools like ssh-askpass but also explored the significance of it in conjunction with the DISPLAY configuration.
In a quest to further optimize SSH authentication, we discussed utilizing tools like setsid. We also addressed vulnerabilities like Bugzilla Bug 69 in graphical passphrase prompt utilities such as ssh-askpass. Therefore, we understood how critical it is to safeguard SSH authentication processes. Not only because it prevents potential passphrase interception but it also enhances overall security in X11 forwarding environments.
As demonstrated throughout the article, we learned how graphical prompts offer a practical and user-friendly method to enter SSH key passphrases. Later, in another section, we discussed how a paradox disproves the same. Therefore, we conclude that while graphical prompts enhance usability, they also necessitate careful consideration of security trade-offs to ensure robust SSH authentication processes.