Yes, we're now running our Black Friday Sale. All Access and Pro are 33% off until 2nd December, 2025:
Detecting Who Pings My Computer
Last updated: March 18, 2024
1. Overview
Sometimes, we need to know who pinged our host. For example, we may want to find the pinging host while trying to solve a network problem.
In this tutorial, we’ll discuss several tools for detecting who pings our host.
2. Using Wireshark
Wireshark is a popular graphical user interface (GUI) tool for analyzing network packets. It captures packets, filters them, and allows us to visualize the network traffic.
We can start it using the wireshark command. It needs root privileges.
Let’s start it from the command line using wireshark:
$ wiresharkHere is the interface of Wireshark on RHEL 9:
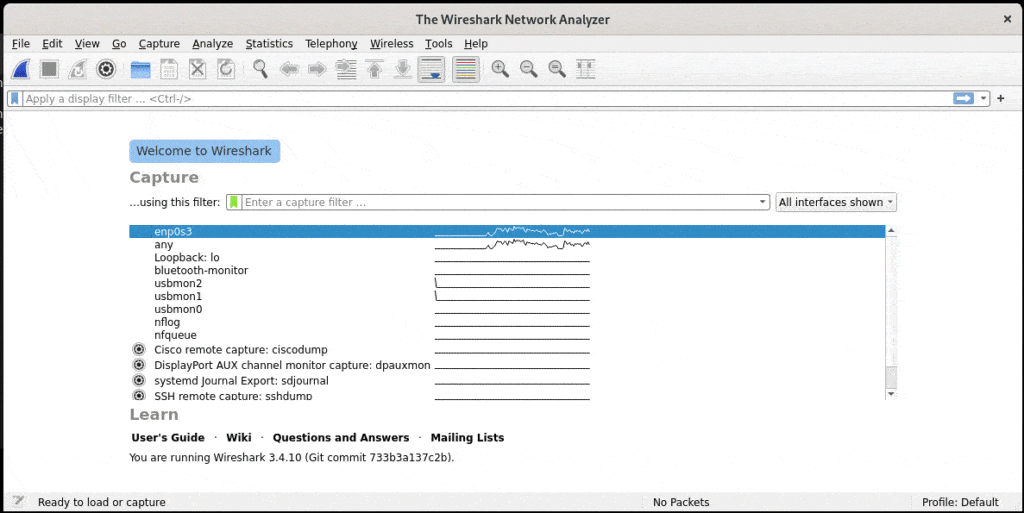
It displays the available network interfaces on our host. There is also a field for entering an expression for specifying the capture filter we want to apply.
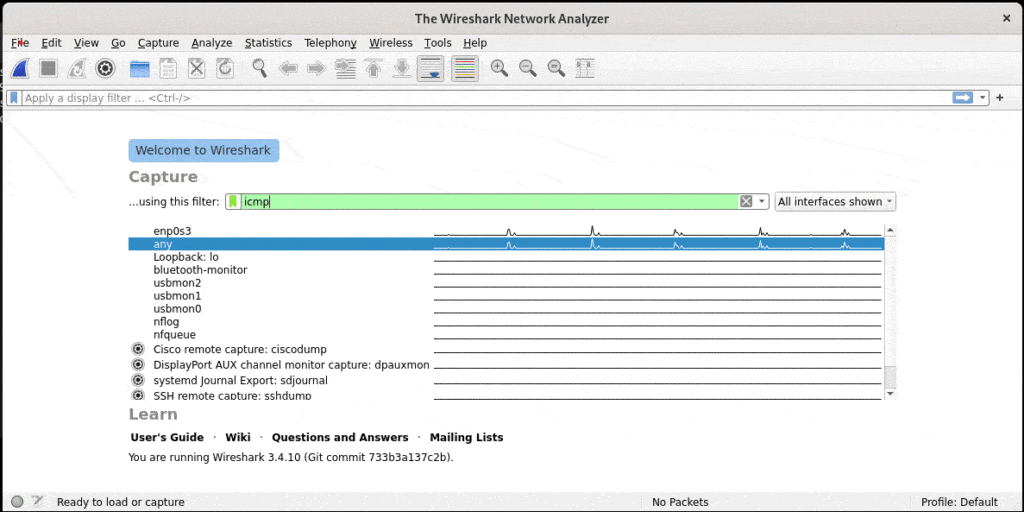
We’ll ping our own host in our examples. The IP address of the host is 10.0.2.15. We’ll select any in the available network interfaces to wait for network packets on all interfaces. Additionally, we’ll specify icmp as the filter because the ping command uses ICMP as the underlying protocol:
Now, we can begin capturing packets by selecting the Start menu item in the Capture menu. First, Wireshark waits for ICMP packets:
Now, let’s ping our host from the command line:
$ ping –c 1 10.0.2.15
PING 10.0.2.15 (10.0.2.15) 56(84) bytes of data.
64 bytes from 10.0.2.15: icmp_seq=1 ttl=64 time=0.047 ms
--- 10.0.2.15 ping statistics ---
1 packets transmitted, 1 received, 0% packet loss, time 0ms
rtt min/avg/max/mdev = 0.047/0.047/0.047/0.000 msWe sent only one ICMP Echo Request to 10.0.2.15 by passing 1 to the -c option of ping. Now, let’s check the GUI of Wireshark:
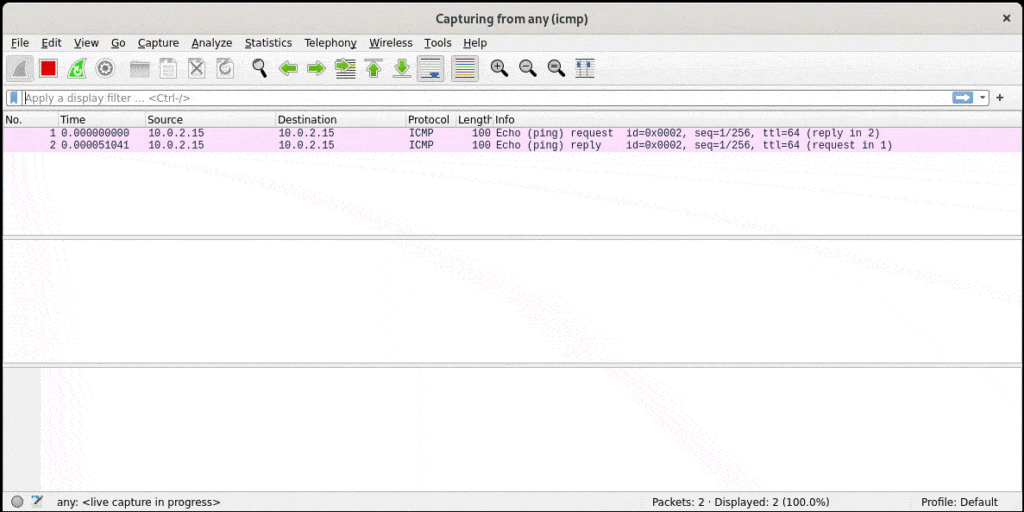
As it’s apparent from the output, we see both the incoming ICMP Echo Request and the outgoing ICMP Echo Reply. The source IP address in the first packet is 10.0.2.15. Therefore, the IP address of the host that pings our host is 10.0.2.15, as expected. So, we were successful in detecting the host that pinged our host.
If we want to display only ICMP Echo Requests, we can use the icmp.type==8 statement in the display filter.
3. Using tshark
Wireshark also provides a command line tool, namely tshark. It’s especially useful when we can’t use a GUI, for example, in connecting to remote hosts using ssh. We can also use tshark in shell scripts. We need root privileges to use it.
Let’s start listening to ICMP packets using tshark:
$ sudo tshark -i any icmp
Running as user "root" and group "root". This could be dangerous.
Capturing on 'any'tshark begins waiting to capture ICMP packets. Now, let’s ping our host from another terminal:
$ ping –c 1 10.0.2.15
PING 10.0.2.15 (10.0.2.15) 56(84) bytes of data.
64 bytes from 10.0.2.15: icmp_seq=1 ttl=64 time=0.035 ms
--- 10.0.2.15 ping statistics ---
1 packets transmitted, 1 received, 0% packet loss, time 0ms
rtt min/avg/max/mdev = 0.035/0.035/0.035/0.000 msLet’s check the output of tshark:
$ sudo tshark -i any icmp
Running as user "root" and group "root". This could be dangerous.
Capturing on ‘any’
1 0.000000000 10.0.2.15 -> 10.0.2.15 ICMP 100 Echo (ping) request id=0x002c, seq=1/256, ttl=64
2 0.000011557 10.0.2.15 -> 10.0.2.15 ICMP 100 Echo (ping) reply id=0x002c, seq=1/256, ttl=64 (request in 1)
The -i option of tshark specifies the network interface to listen to. any is for listening to all interfaces. icmp is the capture filter. The first packet captured is the ICMP Echo Request we sent from the other terminal. As it’s apparent from the output, 10.0.2.15 -> 10.0.2.15 shows that this is a packet sent from 10.0.2.15 to 10.0.2.15. Therefore, we successfully used tshark to detect who pinged our host.
We can use the -Y option of tshark to specify a display filter. We specify the capture filter using the -f option in this case:
$ sudo tshark -i any -f icmp -Y icmp.type==8
Running as user "root" and group "root". This could be dangerous.
Capturing on 'any'
1 0.000000000 10.0.2.15 -> 10.0.2.15 ICMP 100 Echo (ping) request id=0x002c, seq=1/256, ttl=64Now, there is only the ICMP Echo Request in the output.
4. Using tcpdump
tcpdump is another commonly used command line tool for capturing, filtering, and analyzing network traffic. It has a rich set of options and filters.
Similar to tshark, it can be used in cases where we can’t use a GUI tool. It’s suitable for use in shell scripts. We need root privileges to use it.
Its usage is similar to tshark:
$ tcpdump -n -i any icmp
tcpdump: data link type LINUX_SLL2
dropped privs to tcpdump
tcpdump: verbose output suppressed, use -v[v]… for full protocol decode
listening on any, link-type LINUX_SLL2 (Linux cooked v2), snapshot length 262144 bytestcpdump begins waiting for capturing ping packets. The -n option is for displaying IP addresses instead of hostnames. The -i option of tcpdump specifies the network interface to listen to. icmp is the capture filter.
Now, let’s ping the local host once more from another terminal:
$ ping –c 1 10.0.2.15
PING 10.0.2.15 (10.0.2.15) 56(84) bytes of data.
64 bytes from 10.0.2.15: icmp_seq=1 ttl=64 time=0.037 ms
--- 10.0.2.15 ping statistics ---
1 packets transmitted, 1 received, 0% packet loss, time 0ms
rtt min/avg/max/mdev = 0.037/0.037/0.037/0.000 msLet’s check the output of tcpdump:
$ tcpdump -n -i any icmp
tcpdump: data link type LINUX_SLL2
dropped privs to tcpdump
tcpdump: verbose output suppressed, use -v[v]… for full protocol decode
listening on any, link-type LINUX_SLL2 (Linux cooked v2), snapshot length 262144 bytes
11:05:16.241162 lo In IP 10.0.2.15 -> 10.0.2.15: ICMP echo request, id 54, seq 1, length 64
11:05:16.241175 lo In IP 10.0.2.15 -> 10.0.2.15: ICMP echo reply, id 54, seq 1, length 64
According to the output, 10.0.2.15 pinged 10.0.2.15, as expected.
We can also display only ICMP Echo Requests using icmp[icmptype]=icmp-echo as the filter expression:
$ tcpdump -n -i any icmp[icmptype]=icmp-echo
tcpdump: data link type LINUX_SLL2
dropped privs to tcpdump
tcpdump: verbose output suppressed, use -v[v]… for full protocol decode
listening on any, link-type LINUX_SLL2 (Linux cooked v2), snapshot length 262144 bytes
11:05:16.241162 lo In IP 10.0.2.15 -> 10.0.2.15: ICMP echo request, id 54, seq 1, length 64
Now, we see only the ICMP Echo Request in the output.
5. Conclusion
In this article, we discussed three different tools for detecting who pings our host.
Firstly, we used Wireshark. Then, we saw that tshark is another alternative, which is also provided by Wireshark. Finally, we discussed tcpdump.