Learn through the super-clean Baeldung Pro experience:
>> Membership and Baeldung Pro.
No ads, dark-mode and 6 months free of IntelliJ Idea Ultimate to start with.
Last updated: March 18, 2024
Viruses have been a persistent threat to the cybersecurity community since their inception. Over the years, viruses have evolved in various ways to evade detection and infect more computers.
Viruses have evolved through the development of different types of viruses. Three types of viruses that have emerged in the last few decades are oligomorphic, polymorphic, and metamorphic.
In this tutorial, we’ll explore these types of viruses in detail, discuss their differences, and investigate how to detect and prevent them.
This virus can change its code every time it infects a new system. The changes in the code are limited to a few instructions, making it difficult for antivirus software to detect the virus.
Moreover, oligomorphic viruses are created by hackers who have knowledge of programming languages and can write code in different formats. This virus type can be challenging to detect because it only changes a few instructions each time it infects a new system.
These types of viruses modify a larger portion of their code than oligomorphic viruses, increasing antivirus software’s difficulty in detecting them.
Polymorphic viruses are developed using a technique known as code obfuscation, which makes it difficult for antivirus software to recognize the virus. Moreover, they can be dangerous because they can spread rapidly, and their code can change so quickly that antivirus software can’t keep up.
In this type of virus, the changes are so significant that the virus appears as an entirely new virus to antivirus software.
Metamorphic viruses are created using complex algorithms that generate new code that is functionally equivalent to the original code. This type of virus can be very difficult to detect and remove because its code is gradually changing.
The following radar chart shows the differences between oligomorphic, polymorphic, and metamorphic viruses in terms of the degree of code change and difficulty in detecting:
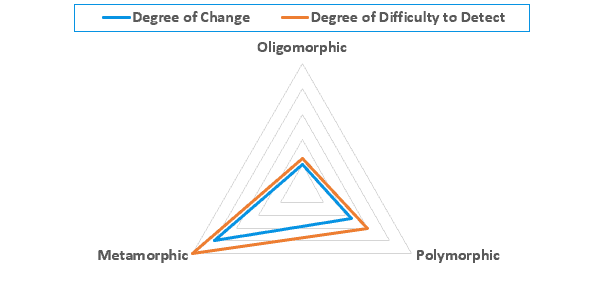
The following table summarizes the differences between oligomorphic, polymorphic, and metamorphic viruses.
| Virus Type | Code Changes | Difficulty of Detection |
|---|---|---|
| Oligomorphic | Changes a few instructions each time it infects a new system | Challenging because it only changes a few instructions |
| Polymorphic | Changes a significant portion of code each time it infects a new system using code obfuscation | More difficult due to the use of code obfuscation and rapid code changes |
| Metamorphic | Changes its code entirely using complex algorithms to generate new functionally equivalent code | Very difficult because the virus appears as an entirely new virus |
Detecting and preventing these types of viruses can be difficult due to their ability to evade antivirus software. However, there are several strategies that can be used to mitigate the risk of infection by these viruses.
One strategy is to regularly update antivirus software to ensure that it can detect the latest virus signatures. It is also essential to be cautious when downloading or opening files from unknown sources and to avoid clicking on suspicious links or attachments in emails.
Another effective strategy is to use multiple layers of security, such as firewalls and intrusion detection systems, to detect and prevent malware from entering the network.
Additionally, organizations can implement security awareness training for their employees to educate them about the risks of malware and how to avoid infection. This training can help employees promptly identify suspicious emails or files and report them to the IT department.
In conclusion, the threat of viruses has continued to evolve and become more sophisticated over time. Oligomorphic, polymorphic, and metamorphic viruses are three types of viruses that have emerged as a result of this evolution. The challenge with these viruses is that they can evade antivirus software, making them difficult to detect and remove.
However, organizations can implement various strategies, such as regularly updating antivirus software, using multiple layers of security, and providing security awareness training, to mitigate the risk of infection.
By staying vigilant and implementing these strategies, we can stay one step ahead of these evolving threats and protect ourselves and our organizations from the harm caused by viruses.