1. Introduction
In this tutorial, we’ll study the differences between FTPS, SFTP, and SCP. All these three terms refer to protocols that we can use to transfer files over the network. However, they work in different ways.
To allow a better understanding of the differences, we’ll first look at when we need to use these protocols. Next, we’ll learn how they work. Finally, we’ll systematically compare the three protocols.
2. When Do We Need to Use These Protocols?
We need to use one of these protocols when we’ve to transfer files over a network securely. Today, several software programs support the use of these protocols. We can, for example, use SCP or SFTP through WinSCP software, or we can use software like FileZilla that supports all three protocols.
However, note that the security mechanisms of these protocols bring additional overhead when transferring files. Therefore, if the files we have to transfer aren’t sensitive and security isn’t a requirement, we can use simpler alternatives.
3. How Do These Protocols Work?
Let’s look at an overview of the three protocols.
3.1. FTPS
Before we study FTPS, let’s take a brief look at FTP (File Transfer Protocol). FTP is a communication protocol that allows us to transfer files between computers on a network. This protocol works under a client-server model. So, we can transfer files from an FTP client to/from an FTP server.
However, when we use FTP, all authentication data and file contents are transmitted over the network as plaintext. Thus, we’ve no security guarantees in this case.
Security in FTP can be provided by employing SSL/TLS protocol for secure authentication and channel encryption. We often call this approach to secure file transfer via FTPS (also known as FTP-SSL or FTP Secure).
For more detailed information about FTPS, please see RFC 4217.
3.2. SCP
The term SCP commonly refers to both the Secure Copy Protocol and the OpenSSH secure file copy program. Although it’s considered a protocol, there’s no RFC or any other specification of SCP.
Basically, SCP also allows us to securely transfer files between remote hosts. However, SCP relies on SSH (Secure Shell) tunnels for secure file transfer. Thus, the SSH protocol provides the entire host authentication and communication encryption process.
The operation of SCP is relatively simple. Once the SSH establishes the connection between the client and the remote server, SCP uses commands similar to the traditional Unix “cp” (copy) command to copy files.
3.3. SFTP
SFTP (SSH File Transfer Protocol) is a secure protocol that allows us to transfer and manage files between remote hosts via an SSH connection. Thus, SFTP is an extension of SSH and therefore doesn’t use FTP as a basis.
Although at first SFTP looks very similar to SCP because both are based on SSH, it’s considered to be much more powerful. In the next section, we’ll clarify the main differences.
For further detailed information about SFTP, please refer to RFC 4253.
4. Comparison
Let’s examine some key points of these three protocols.
4.1. Communication Channels
FTPS (like FTP) uses two communication channels: control and data channels. The client and server use the control channel to send commands that control the communication. The data channel is responsible for transferring the contents of the files. The figure below illustrates an FTPS communication:
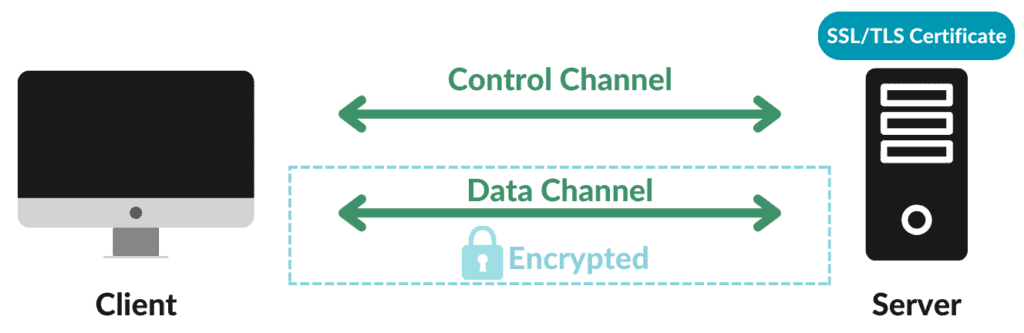
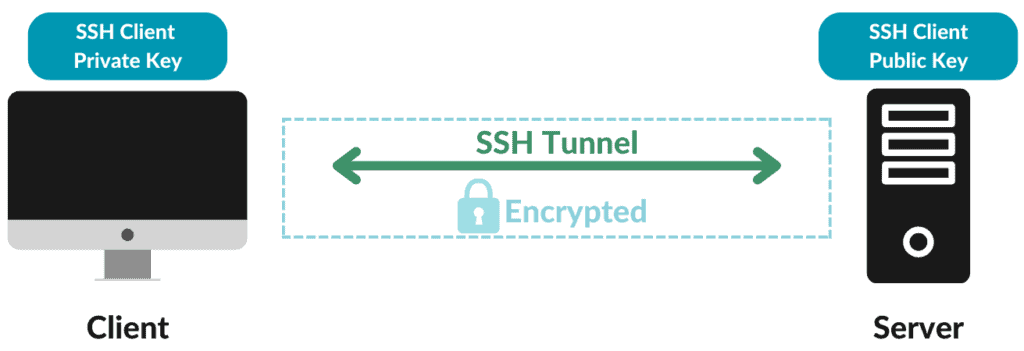
In the case of the SCP and SFTP protocols, only one communication channel is used:
4.2. Encryption
The initialization of an FTPS session isn’t secure. After starting a session, the FTPS client can request the server to make the session secure. Actually, we can choose to encrypt both the control and data channels or only the data channel. If the server accepts the client’s request for security, it’ll initiate an SSL/TLS negotiation. Upon successful completion of the negotiation, the session becomes secure.
Both the SCP and SFTP protocols use an SSH connection. For this reason, we can say that SSH encrypts the sessions of these two protocols from the beginning.
4.3. Use of Connection Ports
FTPS uses multiple ports for file transfers. Every time we request a file transfer or a directory listing, another port must be opened for the data channel. In contrast, SCP and SFTP use only one port for all communications.
Using fewer ports exposes fewer vulnerability points. Also, using fewer ports enables us to easily check for anomalies, suspicious signs, and other threat indicators.
Thus, we can say that SCP and SFTP are preferable for use alongside firewalls compared to FTPS.
4.4. Authentication Mode
The authentication process over a network connection allows both parties involved to confirm their identities.
To do this with FTPS, we need to use digital objects called SSL/TLS certificates. We can create these certificates by using tools such as OpenSSL. However, for an FTPS server to provide assurance that the certificate is indeed its own. A trusted certificate authority must sign its certificate. Otherwise, the FTPS client displays an alert stating that the certificate isn’t valid. The connection can be accepted or denied by us (users).
On the other hand, with the SFTP and SCP protocols, we can authenticate using a username and password or SSH keys. SSH keys are more recommended and we can generate them using software like ssh-keygen and others. Also, SSH keys don’t require a signature from a trusted certificate authority.
4.5. Transfer Speed
FTPS file transfer is usually faster than SCP or SFTP. The main reason for this is that both SCP and SFTP are based on SSH tunnels. We must remember that SSH was designed to replace Telnet and other insecure remote shells, not for very high-speed communications.
4.6. Encoding
FTPS (like FTP) can transfer data encoded in ASCII or binary format. Usually, FTPS client software allows us to choose between one of two encoding types. They can also offer an automatic mode of selection between the two encoding types, according to the most appropriate encoding for each file type.
By contrast, the SCP and SFTP protocols send all data in binary format. This is also inherited from the SSH protocol.
4.7. File Management Features
SCP allows us to transfer files from a client to a server and vice versa. Also, we can transfer files between two SCP servers. But that’s all in terms of remote file management.
When working with FTPS, we can use additional features. This includes downloading, uploading, deleting, and listing files via FTPS.
However, the SFTP protocol offers the most comprehensive set of features. SFTP includes all the features mentioned for FTPS. In addition, we can alter ownership information of files, modify file permissions, rename files, create symbolic links, and more.
Finally, in case the files get interrupted while transferring, SFTP allows us to resume the interrupted files, whereas SCP and FTPS don’t support this feature. The only thing we can do with SCP and FTPS is overwrite the partially transferred file.
4.8. Adoption Nowadays
FTPS is a long-standing and widely adopted protocol. It’s one of the most widely used protocols for large-scale file transfer over the Internet.
However, because of its fairly limited functionality, FTPS is slowly losing ground to other protocols, such as SFTP.
The SCP protocol has presented some drawbacks over time. Recent examples of this are the vulnerabilities reported in CVE-2019-6111 and CVE-2020-15778. For this and other reasons, the SCP protocol has been deprecated and replaced by SFTP.
Despite this, we can still use the SCP tool. Currently, the SCP program for Linux environments uses the SFTP protocol by default. To force the use of SCP, we need to enter the parameter “-O” on the command line.
SFTP is seen as a promising candidate to become the most widely used protocol for secure file transfer. The main reasons for this are its large number of features and flexibility.
4.9. Summary
In the table below we summarize the main differences between FTPS, SCP, and SFTP.
5. Conclusion
In this article, we studied the differences between the FTPS, SCP, and SFTP protocols.
We can conclude that SFTP offers more features, but FTPS is faster and even more widely used today. The SCP protocol has been deprecated, although the SCP tool is still widely used, running the SFTP protocol instead.
