1. Introduction
In this tutorial, we’ll discuss software piracy and various technical measures to prevent software piracy.
We’ll provide helpful tips and share best practices.
2. What Is Software Piracy?
Software piracy is the unauthorized use, distribution, or reproduction of software without permission from the copyright holder or developer. It happens when individuals or organizations copy, share, sell, or use the software, violating its creator’s licensing terms and conditions.
In most countries, it’s illegal and viewed as a violation of intellectual property rights. It deprives software developers of rightful revenue and can adversely affect the industry, discouraging innovation and investment in new technologies. Additionally, pirated software often lacks essential updates, security patches, and support, which can lead to technical issues and expose users to potential security risks.
3. Types of Software Piracy
There are several types of software piracy. We’ll focus on counterfeiting, cracking, and keygens:

3.1. Counterfeiting
Counterfeiting software piracy, also known as software counterfeiting, refers to the unauthorized replication and distribution of copyrighted software with the intent to deceive consumers into believing they are purchasing genuine, legitimate products.
Producers often create counterfeit software to resemble the original, including packaging, labels, and sometimes even holograms, making it challenging for consumers to differentiate between genuine and counterfeit versions.
3.2. Cracking
Cracking software piracy, commonly known as “cracking,” refers to the unauthorized modification or manipulation of software to remove copy protection mechanisms, such as license checks or serial number verifications, allowing users to use the software without purchasing a legitimate license or paying for it.
Crackers are individuals or groups that specialize in reverse engineering software code to create and distribute these modified versions of software.
3.3. Keygens
Keygens (key generators) exploit vulnerabilities or weaknesses in the software’s license validation process. Keygens are tools or programs that generate fake license keys or serial numbers for software products.
Users use these generated keys to unlock the full functionality of the software without needing to purchase a legitimate license from the software developer or copyright holder.
It’s common for users to share keygens through multiple online channels, such as websites, forums, file-sharing platforms, and torrent sites. They often package them with instructions on how to apply the generated key to the software.
Crackers or software pirates commonly associate keygens with software piracy, and they often create and distribute them.
4. Piracy Networks
Pirates often use BitTorrent and other peer-to-peer (P2P) file-sharing networks to distribute large quantities of pirated software. Downloading software from these sites using torrent clients makes it challenging to trace the original source.
Some pirates operate websites that offer direct download links for pirated software. These websites may disguise the illegal nature of their content or operate under different names to avoid detection.
The dark web, a part of the internet accessible through specialized browsers, is known for hosting illegal activities, including the distribution of pirated software.
5. Technical Measures to Prevent Software Piracy
No anti-piracy measure is entirely foolproof, and determined attackers may find ways to circumvent these protections. However, implementing a combination of technical measures can significantly increase our level of protection and deter casual software pirates from engaging in illegal activities.
Incorporating online verification mechanisms that periodically check the validity of the software license with a central server is essential. If the license is found to be invalid, the software may limit its functionality or deny access. Cloud-based licensing systems tie the software’s functionality to an authenticated cloud account. This enables remote license management and better control over authorized users.
We should also implement Digital Rights Management (DRM) technologies to protect digital content and prevent unauthorized copying or distribution. DRM can include encryption, access controls, and watermarks.
We can use code obfuscation techniques to make the software’s source code more challenging to reverse engineer, reducing the likelihood of crackers creating unauthorized versions.
Finally, we can require users to activate the software online or over the phone after installation. Activation typically involves sending encrypted information to a central server, which verifies the legitimacy of the software and grants permission for its use.
6. Handling Piracy Incidents
We have several options at our table:
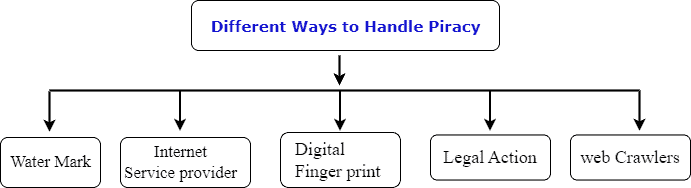
Some software developers embed digital watermarks within their software. These watermarks are hidden identifiers that can help trace the source of pirated copies when people discover them online.
Anti-piracy organizations and software developers use web crawlers and specialized search algorithms to scan the internet for websites and forums distributing pirated software. They can identify and monitor sites that offer downloads or links to cracked software.
Anti-piracy organizations may collaborate with ISPs to identify and block websites distributing pirated software or to take down infringing content. Digital fingerprinting involves creating unique signatures or hashes of the software’s files. People can compare these fingerprints against known databases to detect unauthorized copies.
Some anti-piracy organizations or software developers conduct undercover operations to gather evidence against large-scale piracy operations. When required, copyright holders may take legal action against individuals or organizations found distributing pirated software to deter future piracy.
7. Legal Protection Against Software Piracy
Copyright laws grant exclusive rights to the creators of original works, including software. These laws prohibit the unauthorized reproduction, distribution, and use of copyrighted software without the permission of the copyright holder.
The DMCA is a U.S. law that criminalizes the circumvention of digital copy protection measures and the distribution of tools or services that enable piracy. It also provides a mechanism for copyright holders to request the removal of infringing content from online platforms.
Software developers often include end-user license agreements (EULAs) or terms of service (ToS) that outline the permitted uses of the software and prohibit unauthorized distribution or copying. Copyright holders have the option to file civil lawsuits against individuals or organizations engaged in software piracy. Civil lawsuits can result in monetary damages and injunctions against further piracy.
In some cases, software piracy can lead to criminal charges. Law enforcement agencies may investigate and prosecute cases of large-scale piracy, which can result in fines, penalties, and potential imprisonment for offenders.
8. The Future of Software Protection
The future of software protection from piracy will likely involve a combination of evolving technologies and legal measures to address the challenges posed by increasingly sophisticated software pirates.
Software developers will continue to enhance advanced encryption and code obfuscation techniques to make reverse engineering and cracking more difficult. Using hardware-based security features and blockchain technology may also play a role in improving software protection.
Software developers can employ hardware-based security modules (HSMs) and trusted execution environments (TEEs) to protect software at the hardware level, making it more resistant to tampering and unauthorized access. Regular software updates and patches will continue to be crucial in addressing newly discovered vulnerabilities and closing potential piracy loopholes.
Artificial intelligence and machine learning algorithms can use to analyze usage patterns and identify potential instances of piracy. These technologies can help detect unauthorized use and distribution of software more effectively.
9. Security Measures
Preventing software piracy involves implementing measures to discourage and prevent these illegal activities:
10. Conclusion
In this article, we discussed software piracy with its type. No method alone can provide foolproof protection against piracy. The collaboration between software developers, legal entities, and cybersecurity experts is crucial in this endeavor which includes adding a watermark, digital fingerprints, a web crawler, and legal actions.
Additionally, fostering awareness among end users about the ethical and legal implications of using pirated software can help in reducing the demand for unauthorized copies.