Yes, we're now running our Black Friday Sale. All Access and Pro are 33% off until 2nd December, 2025:
Differences Between Role and Permission-based Access Control
Last updated: March 18, 2024
1. Introduction
In this tutorial, we’ll explore both role-based and permission-based access control, comparing and establishing relations between them.
We’ll have a brief contextualization about access control, understanding its importance nowadays. Thus, we’ll investigate role-based and permission-based access control techniques. Finally, we’ll review and compare the presented concepts in a systematic summary.
2. Access Control
As time passes, the Internet becomes more and more popular. With this continuous popularization, accessing the World Wide Web is no longer only for searching for information but also for working, shopping, and communicating.
So, with several applications, securely exchanging data turned into a challenge. Many methods and techniques to tackle this challenge have been proposed. Some aim to protect systems, such as installing antivirus and deploying DDoS mitigation solutions.
Other methods, in turn, focus on checking if a user accessing a system is who he claims to be. These methods are encompassed by access control techniques.
Access control regulates who can access what in a digital system. In this context, we have heterogeneous techniques to define and enforce these regulations. Among these techniques, we can highlight the role and permission-based ones.
In short, permission-based access control defines permissions to each system’s user. On the other hand, role-based access control specifies permissions to a set of roles of a system, roles assigned to each user.
Both role and permission-based techniques are supported by other security methods. The majority of these other methods aim to authenticate the user somehow. Examples of them are password-based, biometric-based, and physical token-based authentication.
In the following sections, we’ll investigate, in detail, the concepts and properties of permission and role-based access control techniques.
3. Permission-based Access Control
Before specifically discussing permission-based access control, we can explore what permission really means. Conceptually, providing permission to a user means allowing him to access a resource or execute a specific operation in a system.
Usual permissions relate to reading, editing, and deleting operations of a given digital resource. So, getting permission to access a resource means that at least the entity can read its content.
In such a scenario, full access to a resource consists of having three different permissions: one for each operation (read, edit, and delete).
So, we can understand permission-based access control as the technique that defines specific permissions for every entity using a system. As previously stated, each permission typically is a tuple indicating both a resource and an operation.
The image next shows an example scenario where three entities have different permissions related to the same resources:
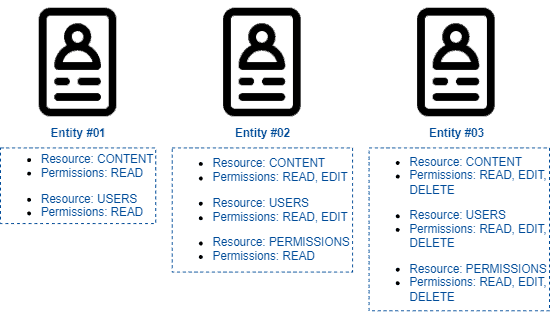
The main benefit of adopting permission-based techniques is attributing permission to the entities using a system with a fine granularity control.
However, this fine-grained permission control can also be understood as a problem. It occurs since we need personal management of the permissions of each entity. In this context, permission-based access control is impractical for systems with lots of users due to the manageability challenges it imposes.
4. Role-based Access Control
Taking a similar approach from the last section, we may first see what a role is before studying the role-based access control technique.
Actually, we are already familiar with the concept of role in our everyday lives. For instance, we can have one or many roles in our jobs: a frontend developer, a system engineer, a technical writer, and so on.
Thus, each role we assume presumes a series of particular responsibilities and duties that will guide our work.
In role-based access control, we have a similar scenario to the presented example: each entity using a given system has a role that defines the resources it can access and the operations it can execute.
In a technical view, we can say that a role-based system determines sets of permissions enforced to entities acting with similar objectives and privileges in a system.
Probably the most typical role categorization in computing systems is user and administrator. In this case, users are typically limited entities in the system: they can not access all the resources nor execute all the operations for those resources they access.
An administrator, in turn, has several permissions that a user does not have: they can access almost resources available in the system and freely read, edit, and delete them. Furthermore, we also have the figure of the system owner that has all possible system permissions.
In the following figure, we have an example scenario where the three previously presented roles are assigned to five different entities using a system:
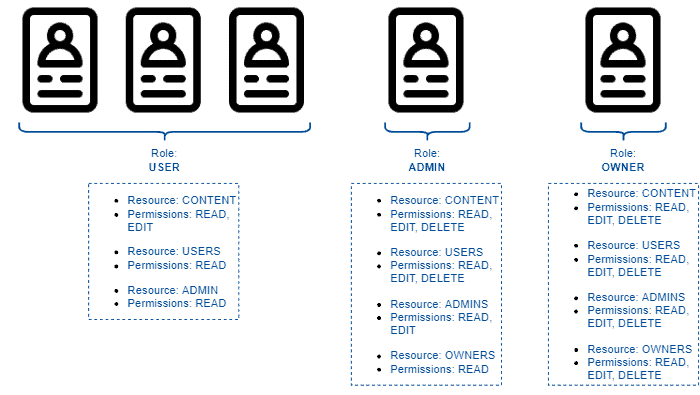
It is relevant to highlight that, although user, administrator, and owner are frequent, we can have many other roles. So, for example, in a people management system, we can have roles of assistants, technical people, managers, and directors.
The principal benefit of using the role-based access control technique is easing the management of entities that access the system. It occurs because changes in permissions of a role are automatically applied to every entity with this role.
However, using roles reduces the possibility of customizing the permissions set for a single entity. Thus, to assign a completely customized set of permissions to an entity, we’ll need to create a new role only for it.
5. Systematic Summary
Securing resources and restricting the execution of operations to authorized entities is crucial for the current digital systems.
The popularization of networking shifted the way how we communicate and work. However, it also brought challenges, for example, how to avoid both sensitive data from being accessed and sensitive operations from being executed by unauthorized entities.
Adopting access control systems is one of the solutions to the previously presented challenges. We have two big categories of access control systems: permission-based and role-based.
Each one of these access control categories has specific characteristics. Let’s see and compare some of these characteristics in the following table:
| Permission-based Access Control | Role-based Access Control | |
|---|---|---|
| Brief Definition | Technique that defines specific permissions for every entity using a system | Technique that determines common sets of permissions enforced to entities acting with similar objectives and privileges in a system |
| Customization of Permissions | Entity-based (each entity has specific permissions) | Role-based (each role has specific permissions) |
| Updating Permissions | An update in a permission set of an entity applies only to the entity | An update in the permissions of a role applies to each entity with the same role |
| In Practice | Assigns reading, editing, deleting, and executing permissions directly to each entity | Assigns reading, editing, deleting, and executing permissions to each role, and each entity have a role |
6. Conclusion
In this tutorial, we explored permission and role-based access control mechanisms. First, we reviewed concepts about access control systems in general. Next, we studied techniques to implement access control: permission-based and role-based. At last, we outlined the characteristics of these techniques in a systematic summary.
We can conclude that access control is essential for the current digital world. However, using permission or role-based technique to implement access control depends on the system and scenario where it will operate since these techniques have different characteristics.