Yes, we're now running our Black Friday Sale. All Access and Pro are 33% off until 2nd December, 2025:
What Is a Dmz in Networking?
Last updated: September 10, 2020
1. Overview
In this tutorial, we’ll study the concept of demilitarized zones in cybersecurity and networking.
We’ll first learn about their origin, and then see why do we implement them in a secure network.
At the end of this tutorial, we’ll understand the reason for the choice of network architectures that include DMZs in adversarial settings.
2. What Is a Demilitarized Zone?
2.1. The Etymology of the Term
The term demilitarized zone (DMZ) we use commonly in cybersecurity and networking isn’t native to computer science. Instead, the term originates from the vocabulary of international law and, more specifically, from the jus in bello.
In that context, a DMZ identifies a special or protected area in an otherwise warring zone. The idea behind a DMZ is that it may be important to prevent a certain area from being subject to military actions. This is done by establishing a special border between opposing factions, and by signing an agreement that prevents either faction from deploying troops or weapons:
2.2. Relationship Between Interstate War and Cybersecurity
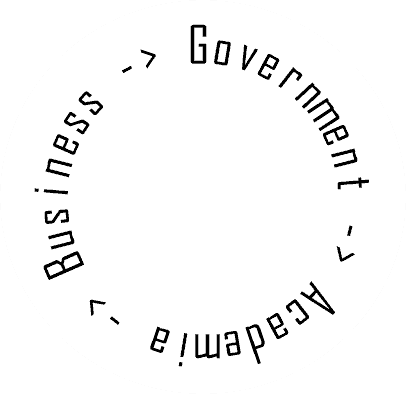
It’s not surprising that the term originates from interstate warfare because cybersecurity itself develops primarily through research in the defense sector. The general rule for technology development in cybersecurity is that the research initially occurs in the government and academic sectors, and then the innovation becomes redistributed to private business:
The same happened for the adoption of DMZs as components of network architectures. In the 1980s, as the Cold War approached its end, the two superpowers realized the potential for exchanges in the sector of software engineering and innovation. They wanted, but couldn’t, connect the two respective research networks:
This is because, while the desire for cooperation was strong, the suspicion of the other’s intention was even greater. The solution was then found by establishing dedicated intermediate nodes between the two networks, which were authorized to carry all the cooperative interactions between the adversarial factions.
2.3. Institutionalized Distrust
The adoption of the first DMZ in networking derived, on one hand, from the benefits expected from cooperation. On the other, it was based upon the need to control access to a network by mutually distrusting parties. The solution to these contradictory tendencies implied the identification of a formal system that allowed mutually beneficial exchanges to take place while simultaneously preventing harmful actions.
This is a situation that, in the literature on knowledge management, takes the name of institutionalized trust and distrust. In relation to this institutionalized distrust, we can now give a definition of DMZ for cybersecurity. A DMZ is a system that, in an adversarial setting between mutually distrusting parties, allows cooperation to take place regardless of the parties’ incentives to defect.
In this sense, a DMZ formalizes the systemic distrust into a set of rules and architectural solutions, which, while preventing adversaries from damaging one another, still allows communication and interaction to safely take place.
3. DMZs and Adversarial Settings
3.1. What Are Adversarial Settings?
We understand now that a DMZ can exist only if a particular group splits into friends and foes, or more accurately, into adversaries. When the DMZs entered the legal discussion, the adversaries were states with standing armies and flags, and the identification of factions on a battlefield was relatively simple. When the DMZ started being used in networking and concerned the interaction between the American and the Soviet communication networks, the identification of adversaries was still sufficiently simple.
DMZs are however used today in a variety of contexts, including corporate security and domestic LANs. Who is, in these comparatively simpler contexts, the adversary? A DMZ is needed only if there’s an adversary whose aggressive actions we fear, but at the same time, we want to be able to communicate with them.
3.2. The Invisible Enemy
The adversary for a business or domestic local network is the generalized malicious attacker, whose outline we leave necessarily fuzzy. It can include a person or organization with properly criminal intent. But also, a nosy employee who wants to know if we’re paying them enough.
In this sense, a DMZ in the business context is a system that allows communication between a trusted network, ours, that we can aprioristically identify in detail, and a generalized or ideal adversary, who may want to want to access the trusted network without authorization.
4. DMZs and Firewalls
4.1. Letting Friends Through, Keeping Foes Out
Technically, the DMZ is a node or a subnetwork in a local network. It’s a special node though, that’s directly accessible by nodes external to the local network:
If the local network uses a firewall, then the DMZ is normally outside of it. In practice, though, the administrator may also choose to adopt a second firewall, with softer rules, to protect the DMZ alone.
4.2. Applications of DMZs
The DMZ serves many purposes for the security of a local network. If our network implements an IP-based system for blocking brute-force attacks, a malicious user may spoof one of the IP addresses of our network to circumvent this measure.
In that case, a DMZ may temporarily interdict access to the network for the suspected devices. In the meanwhile, a trusted service can try to connect to the suspect IP address, to verify whether the request originated from it or from a spoofed IP instead.
The DMZ can also prevent an attacker from learning about the network’s structure. This is an application of the principle of security through obfuscation. Because all connections to and from the trusted network pass through the DMZ, it’s the DMZ alone that’s visible to an outsider.
Further, in case the DMZ becomes compromised, its separation from the trusted network still allows the latter to remain protected. This means that a malicious user would need to gain control of the DMZ first, and could access the trusted network only later. In turn, this gives time to the cybersecurity team to investigate and identify the breach.
4.3. Peel of the Onion and Resiliency
If we want to use the typical metaphor of security as an onion, we can say that a DMZ is the peel of the onion:
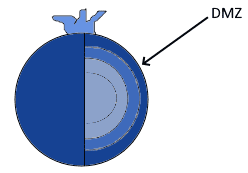
Because it’s visible to all, it can’t host sensitive information belonging to the network’s owner. For this reason, we can never host corporate or personal databases on it.
In terms of resiliency, the DMZ is also the weakest node in a network. This means that, if the network will be compromised, this normally starts with an attack on the DMZ.
To counter this, the DMZ is frequently constituted in the gateway for the internet traffic of a local area network. In that manner, we can analyze internet traffic before it reaches the trusted network. This is done by using services located in the DMZ itself, and not in the network.
Finally, the DMZ is also the location for services provided to users external to the trusted network, such as email servers. We can also use it to grant the user access to the trusted network from the outside. In that case, we can decide to simply set specific permission in the firewall rules.
5. Conclusion
In this article, we studied the concept of demilitarized zones for cybersecurity and networking.