Learn through the super-clean Baeldung Pro experience:
>> Membership and Baeldung Pro.
No ads, dark-mode and 6 months free of IntelliJ Idea Ultimate to start with.
Last updated: March 18, 2024
SSL certificates are essential components for guaranteeing secure web browsing. In particular, an SSL certificate allows the client to verify the identity of the website owner.
Therefore, each web server is first expected to have its own SSL certificate for each website (or domain). Nevertheless, we can indeed use a single SSL certificate on multiple servers simultaneously. In this tutorial, we’ll learn how to do this.
First, let’s recall a few points about SSL certificates that will be relevant to understanding the rest of the article. Next, we’ll examine how a single SSL certificate can be used in different scenarios involving multiple servers. Then, we’ll describe the main benefits of using a single SSL certificate. Finally, let’s briefly discuss some of the challenges involved and important considerations to make.
An SSL certificate is a data file that’s stored on the server hosting a website. It allows websites to use the HTTPS protocol, which is more secure than HTTP. Specifically, SSL certificates enable SSL/TLS encryption.
SSL certificates are registered for a domain name. Thus, they contain the identity of the domain owner. In addition, each SSL certificate has a key pair consisting of a public key and a private key.
When a client accesses a domain, for instance, www.domain.example, a DNS server resolves it to the IP address of the server hosting the website. Then, using the SSL certificate that the server provides, the client can check its authenticity. From there, the client and server can establish a secure (trusted and encrypted) connection.
It’s common practice for administrators of large websites to distribute the load of requests across multiple servers. This approach tends to increase the scalability, performance, and resilience of web servers. However, to ensure secure connections, website administrators need to use some strategy to manage SSL certificates.
As holding multiple SSL certificates requires greater capital investment and management effort, keeping using just one can be a good option. So, instead of issuing an SSL certificate for each server, we can use a single one on multiple servers by employing some technique.
There are different ways to do it. To better clarify, let’s look at some concrete scenarios in which we can use a single SSL certificate on multiple servers.
As a first scenario (illustrated in the figure below), we can consider multiple servers distributed along a region or even worldwide. In this scenario, we have www.domain.example associated with the public IP addresses of the involved servers. So, every time a client accesses www.domain.example, the DNS server resolves it to the IP address of one of the servers:
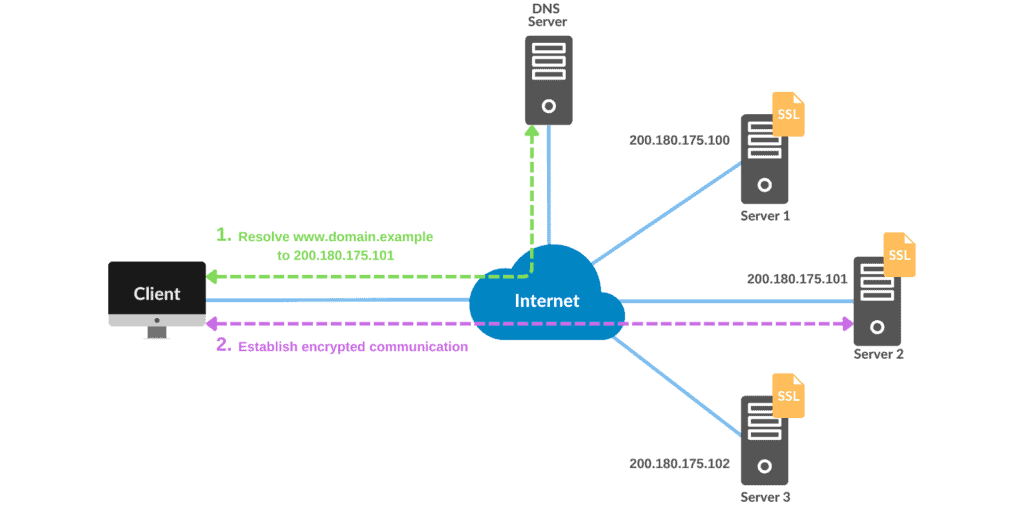
So, considering we’ve only one SSL certificate, we need to copy it to all servers. This also includes copying both the public and private keys to the servers. Hence, as each server holds the certificate, they’ll be able to confirm their identity and establish encrypted communication.
Nowadays, a common scenario is to create a cluster of servers and use a load balancer to distribute traffic between them. The figure below illustrates this scenario:
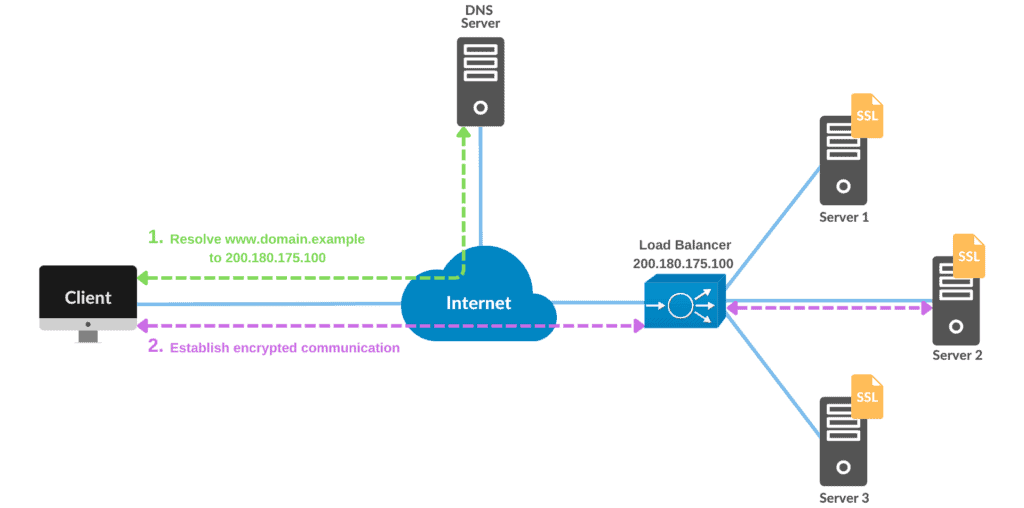
In this case, we have www.domain.example resolving to an IP address of a load-balancer. Thus, when clients access www.domain.example, they reach the load-balancer, which in turn distributes the traffic across the cluster of servers.
Therefore, we only need an SSL certificate for www.domain.example that we copy to all servers in the cluster. But we need to remember that this means we must copy both the public and private keys to every server in the cluster.
In a case similar to the one where we use a load balancer, we can employ a reverse proxy to handle the incoming traffic. We can see a reverse proxy as a special load balancer, as they both sit in front of servers to distribute traffic.
However, load balancers and reverse proxies operate at different network stack layers. Also, reverse proxies can provide additional features for web applications, such as caching and SSL termination (the key point in this scenario).
The figure below exemplifies the use of a reverse proxy. In this scenario, we keep the SSL certificate on the reverse proxy instead of copying it to the servers. Then, we just need to configure the reverse proxy to handle the SSL connection when distributing traffic between the servers:
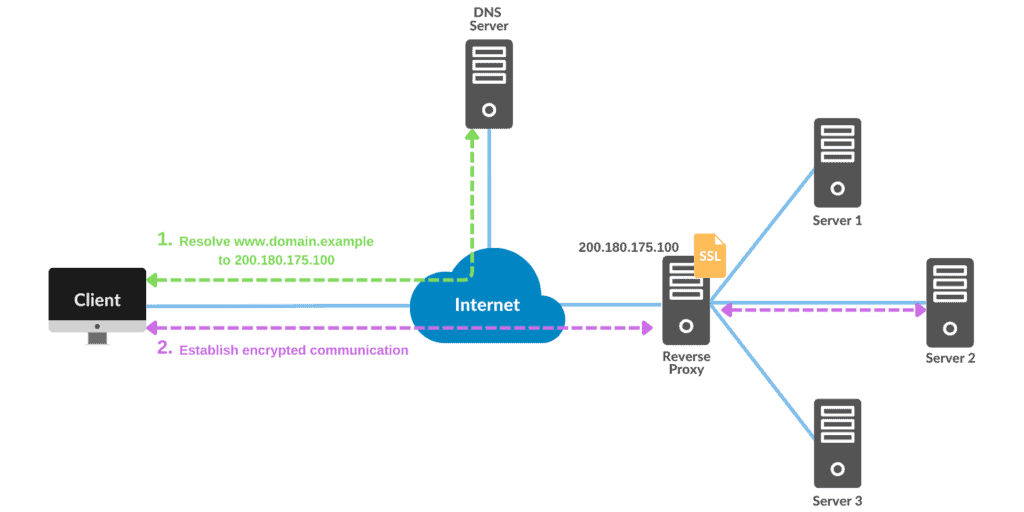
Using one SSL certificate on multiple servers gives us some benefits. Let’s look at some of them.
SSL certificates, especially those with advanced features, can be costly. So, we can save on certificate capital expenditures by using a single certificate even when we’ve multiple servers.
Another key benefit is simplified certificate management. Instead of issuing a new SSL certificate for each server that we need to add, we can centrally manage and renew a single certificate. This tends to reduce administrative bureaucracy and, consequently, management overhead considerably.
It also makes it easier to scale the infrastructure as deploying additional servers becomes more straightforward. We can quickly set up new servers with the existing certificate, which streamlines the process of expanding the web application.
While using a single SSL certificate on multiple servers offers benefits, there are important considerations to keep in mind. Let’s examine some of them next.
As mentioned earlier, there’s no technical impediment to using a single SSL certificate on multiple servers. And we can do this in different ways. However, there may be legal restrictions in some cases.
Some CAs put limitations on the usage of certificates that they provide. This includes the case where the SSL certificate is licensed per server. Therefore, if we used the certificates licensed in this way on multiple servers, we’d be violating the rules of the contract. This could lead to the loss of the certificate or other implications, according to the contract.
So, we should carefully read the certificate provider’s Terms & Conditions before using the certificate on multiple servers.
Private keys are sensitive components of SSL certificates. Indeed, when we use a certificate on multiple servers, at some point, the private key must be transferred between the servers.
Therefore, such key travel is sensitive and dangerous, especially in cases involving servers in different locations. Then, we should do this with great care.
The best way is to transfer the private key as few times as possible and always use some additional security mechanism. This includes the use of tools such as SSH tunneling, VPN, or another tunneling.
When we use only one SSL certificate, the expiration of this certificate will affect the entire set of servers. Therefore, we need to pay extra attention to this.
One issue this approach creates is the possibility of inconsistencies between server certificates. As a whole set of servers need to maintain the same certificate (including the respective keys), eventually, one of them may have incorrect or outdated certificate data. Hence, we need to conduct regular audits of the SSL certificate deployment to ensure that configurations remain consistent and up-to-date across all servers.
In this article, we studied the use of a single SSL certificate on multiple servers.
We’ve seen scenarios with servers behind a load balancer or even in different locations. In such cases, we just need to copy the SSL certificate and the key pair to all servers.
But there’s also the option of using a reverse proxy that intermediates communication between the clients and the servers. In this case, we still use only one certificate, but only in the reverse proxy.