1. Overview
In this tutorial, we’ll discuss piggybacking in networking.
We’ll present the working procedure, variants, and importance of piggybacking technique.
2. Piggybacking in Networking
In networking, piggybacking refers to exploiting existing channels or connections for additional benefits. Piggybacking occurs when a host device or network uses another device’s connection to transfer data. In other words, a user device, such as a laptop or a computer, can access the Internet by using another device, such as a smartphone. In this case, the smartphone has an existing Internet connection.
We can implement piggybacking in wired as well as wireless networks. In wired networks, computers or servers are connected using cables. In wireless networks, we can connect computers or servers using radio waves.
Using the piggybacking technique, a computer with no Internet connection uses the connection of another computer that does have an Internet connection. It doesn’t come under malicious hacking. Instead, it’s a legal activity that allows devices to share the same connection.
We generally utilize piggybacking when the device has no Internet connection. For example, a person traveling with a laptop connected to the hotel’s WiFi network could use piggybacking to share the WiFi connection with personal networking gadgets like smartphones.
3. Working Procedure
In a wired network, a device that wants to piggyback connects to the device with an Internet connection. In a wireless network, we need to set up a device with an Internet connection in order to share that connection with other devices.
The devices with Internet connection create a temporary network between themselves. This network allows the piggybacking device to send and receive data. A device with an Internet connection forwards data to the piggybacking device.
In order to start the data transfer, a piggybacking device on one end sends the data to the network created by the devices with an Internet connection. The piggybacking device without an Internet connection on the other end receives data from devices with Internet connections.
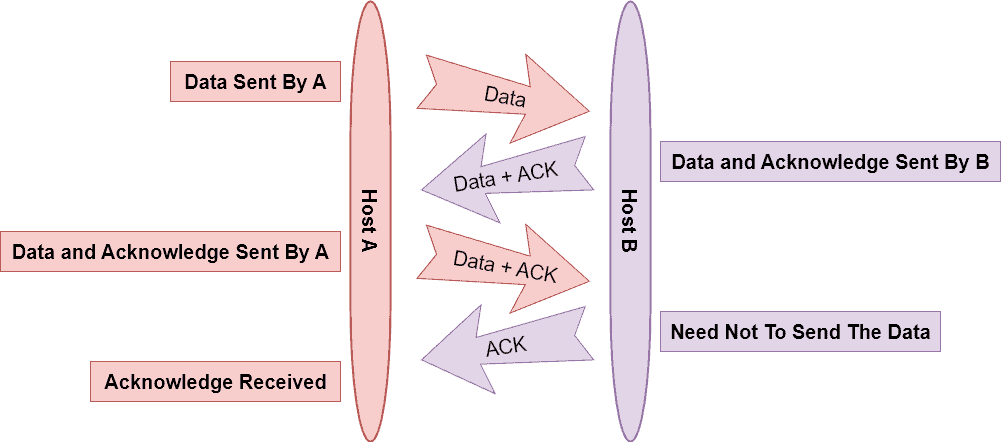
Let’s look at an example. In this example, Host A and Host B want to send data but are not connected to the Internet. Additionally, both devices are connected to a device with an Internet connection. Now using the piggybacking technique, Host A and Host B can communicate with each other:
4. Types of Piggybacking
We can divide piggybacking into three categories: bandwidth, transport, and discovery piggybacking. Let’s discuss each type one by one.
Bandwidth refers to the capacity of a connection while transferring data. In bandwidth piggybacking, a user device can use the bandwidth of an existing connection. This method is beneficial when we want to send data over an existing connection but are not sending enough data to justify the connection to a network.
Transport refers to how two devices are connected. If we connect two devices over a network, we can piggyback the connection between the devices and add a third device. Transport piggybacking is beneficial when the two devices are on different networks.
Finally, in discovery piggybacking, one device uses an existing connection to find another device. For example, a server in a data center may not have direct access to the Internet. However, it may be able to reach a device connected to the Internet, such as a firewall, and use that connection to send data to the outside world.
5. Importance of Piggybacking
We use piggybacking in data networks to reduce the cost of equipment. Additionally, it reduces the time it takes to set up a network. Furthermore, we can use the piggybacking technique to increase the use of network assets, such as bandwidth and servers. Since it allows a device to use another device’s connection, it provides redundancy, which is beneficial in the event of a network outage. Piggybacking is common in data networks that share connections.
Examples of networks where we can implement piggybacking are telephone systems, computer networks, and the Internet. Telecommunication systems use piggybacking when they can’t use a dedicated channel. Computer networks use piggybacking to reduce the need for new equipment. The Internet uses piggybacking so that computers can communicate when they don’t have a dedicated channel.
The primary benefit of using piggybacking is the reduced cost. Data centers rely on high-capacity connections to transfer data to each other. However, these connections are expensive to install and maintain. Piggybacking can extend the reach of these connections without the high cost of installing and managing new links.
Piggybacking reduces costs for both the organizations that own the connections and the organization that is piggybacking on them. The downside to piggybacking is that the other organizations’ connections limit us. It can lead to slower response times and increased latency. We may also risk overloading the other organizations’ connections.
6. Conclusion
In this tutorial, we discussed piggybacking technique which allows data centers to connect with each other by using the existing connections of other organizations.
Additionally, we presented the complete working procedure along with the variants and importance of piggybacking in networking.