1. Introduction
In this tutorial, we’ll discuss image-based viruses, how they work, and the methods to detect them.
We’ll provide helpful tips and share best practices.
2. Understand Image-Based Viruses
Image-based viruses are hidden in an image without significantly altering its visual appearance.
Images themselves are typically not capable of carrying executable code or malware. However, almost any image format (JPEG, PNG, GIF) can be edited to conceal malware. One of the reasons these assaults are so successful is that an image file seems to be much more innocent than an executable file.
While many websites filter out executables and scripts, they may inadvertently allow users to upload images. If so, attackers might package malicious code in an image and send it to a vulnerable web server, which then executes its content.
2.1. Why Do Hackers Hide Viruses in Images?
People share and distribute images across various platforms, including social media, emails, and messaging apps. This increases the chances of users downloading or opening an infected image file.
Additionally, various software applications process image files. If there are vulnerabilities in the image-processing software, attackers can exploit them to execute malicious code on the victim’s system.
Embedding viruses in images allows attackers to circumvent any security measures directed at other types of data. The hidden malicious code within an image file grants attackers the power to make it more challenging for security solutions to identify and stop the threat.
3. How Do Image-Based Viruses Work?
Steganography is a technique of hiding data within an image without altering its appearance. It replaces unused and redundant bits of a carrier image with secret data (a virus in this case). When users open or process the infected image using specific tools or software, the system extracts and executes the virus on the victim’s system:
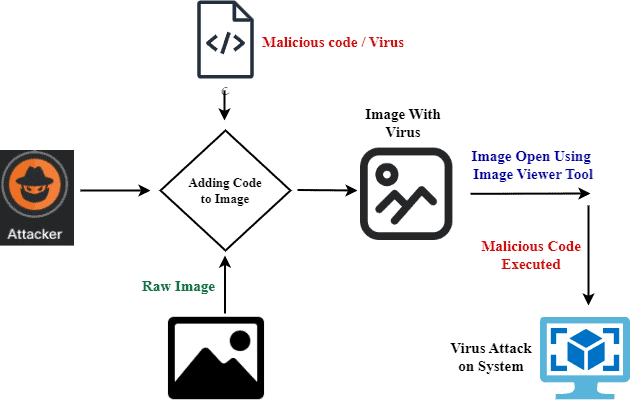
We’ll talk about hiding a virus using the least significant bit substitution and spread-spectrum techniques.
3.1. The Least Significant Bit Substitution
This is one of the simplest and most common steganography techniques.
The least significant bit (LSB) substation distributes the binary equivalent of the hidden message among the least significant bits of each pixel. Those bits are used because they have less impact on the overall image appearance.
For example, let’s say we want to hide the character ‘A’ in eight consecutive pixels of an 8-bit color image:
Then, we copy the bits of the binary representation of ‘A’ (01100101) into the pixel’s LSBs:
The attacker selects a digital image file to act as the carrier for the virus. Next, they will use LSB substitution to embed the virus payload into the selected carrier file by replacing the least significant bits of the pixels’ color values in the image with bits from the virus payload. The attackers need to know the vulnerabilities of the image-processing software to hide the viruses in specific pixels that will exploit those vulnerabilities.
When a user opens an infected image, the viewer executes the hidden virus.
3.2. Spread-Spectrum Techniques
Spread-spectrum techniques add the secret data/text to a cover image in a spread-out manner, making it less detectable. The secret data can be extracted by the receiver by applying a specific decoding process:
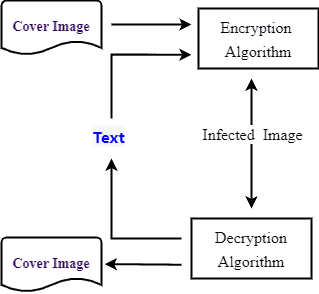
Polyglot files are single files that different applications can interpret differently. The encryption and decryption processes depend on the vulnerabilities of the image-processing application the attackers are targeting. When executed by an application as an image, the virus exploits vulnerabilities in the application to execute the embedded malicious code.
4. The Risks and Vulnerabilities
Image-based viruses exploit the vulnerabilities in image processing libraries or image viewer software to execute malicious code on a user’s device. For example, when a user opens an infected image file, the virus can trigger a buffer overflow or other exploit to gain control of the system.
Using steganography, attackers can embed malware or sensitive information inside images, making it difficult for traditional security measures to detect the hidden content.
Attackers exploit browser and plugin vulnerabilities with malicious image files in online ads, leading to potential attacks.
Image-based viruses could also target vulnerabilities in embedded systems or IoT devices that handle image processing.
5. How to Detect Image-Based Viruses?
Steganalysis is the procedure used to find the hidden data contained within a cover image.
Steganalysis models use specific statistical or structural features to detect hidden data in cover images. For example, features might include statistical measures of pixel values, image color histograms, or wavelet coefficients.
To compile a virus detector, we train a model on a diverse dataset of infected and harmless images. We can use various machine learning algorithms like SVM, random forests, or deep neural networks.
6. Mitigation and Security Measures
We have several options at our disposal:
7. Future Challenges
Malicious actors may use advanced steganography with encryption and dynamic hiding, evading detection and analysis.
As VR/AR technology becomes more integrated into our daily lives, there could be new cybersecurity threats related to viruses specifically targeting AR/VR devices, software, and networks. Hackers might exploit vulnerabilities in AR/VR systems, leading to privacy breaches.
8. Conclusion
In this article, we discussed image-based viruses. They hide in images, making it difficult for users to detect their presence.