1. Introduction
Modern computer systems rely heavily on operating systems (OS) since they manage hardware and software resources aiming to enhance the user experience, making them the backbone of the entire system.
As computer systems become more complex, it is becoming increasingly important to protect them from malicious attacks and software failures.
In this tutorial, we’ll explore three crucial protection domains in operating systems: memory protection, process isolation, and privilege levels. Furthermore, we’ll provide examples of their usage in modern operating systems and discuss the challenges they pose.
2. Domains of Protection
Domains of protection are boundaries that can be used to separate different parts of an operating system or user process. Since it allows each domain to operate independently without affecting others, it provides isolation and protection.
Protection domains are typically implemented using hardware and software mechanisms, including memory protection, process isolation, and privilege levels.
2.1. Memory Protection
Memory protection is a hardware mechanism that separates different parts of memory and ensures that each process can only access its own memory space. This prevents one process from accessing or modifying the memory of another process, thereby protecting the system from malware and other malicious attacks.
Moreover, the CPU’s memory management unit (MMU) enforces memory protection by mapping virtual addresses to physical addresses and ensuring that only authorized processes may access the memory.
The following figure shows the memory protection mechanism:

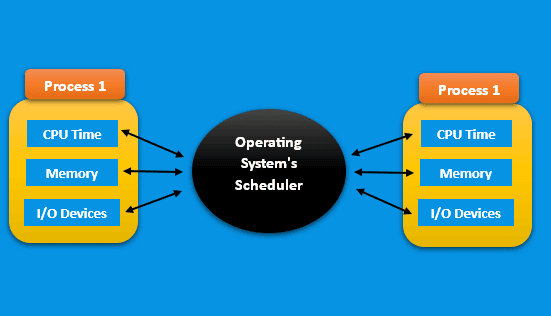
2.2. Process Isolation
Process isolation refers to a software mechanism that separates user processes, ensuring that each process can only access its allocated resources, such as CPU time, memory, and input/output (I/O) devices, without interfering with other processes. Moreover, it is a critical process in ensuring the reliability and stability of the system, as a failure in one process doesn’t affect others.
In addition, the operating system’s scheduler enforces process isolation by assigning CPU time to each process and ensuring that processes can’t interfere with each other’s resources.
The following figure shows the process isolation mechanism:
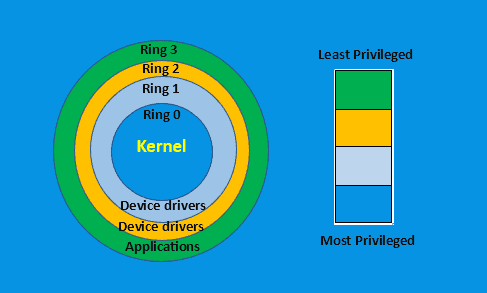
2.3. Privilege Levels Design
Privilege levels are some mechanisms that are hardware-based and designed to establish distinct levels of access to system resources. For example, in modern operating systems, two common privilege levels exist: user mode and kernel mode.
User mode is where user applications run, and they have limited access to system resources. On the other hand, kernel mode is where the operating system runs and has full access to system resources.
Additionally, the CPU enforces the privilege level, facilitating the seamless transition between user mode and kernel mode. This essential mechanism prevents user applications from directly accessing system resources and guarantees that the operating system retains full control over the system.
The following figure shows the mechanism for determining the privilege levels:
3. Examples of Domains of Protection in Operating Systems
We may use extensively the domains of protection in modern operating systems to provide isolation and protection. Here are a few examples of domains of protection in operating systems.
3.1. Virtual Memory
Virtual memory is a memory management technique that allows a computer to use more memory than it physically has by temporarily transferring pages of data from the main memory to the hard disk. In addition, each process isolates its own virtual memory space from other processes.
This ensures that a process can’t access the memory of another process, providing memory protection.
3.2. Sandboxing
Sandboxing is a technique used to isolate and execute untrusted software in a controlled environment. Typically, this involves running the software in a restricted environment with limited access to system resources. Moreover, the operating system creates a separate process for the sandboxed application, ensuring process isolation.
Sandboxing is commonly used to run web browsers and email clients, which are vulnerable to malware and other malicious attacks.
3.3. Containerization
Containerization is a virtualization technique that allows multiple applications to run on a single operating system without interfering with each other. Mainly, each container has its own file system, network stack, and process space, providing process isolation.
Containerization is widely utilized in cloud computing because it enables the concurrent execution of multiple applications on a single server.
3.4. User Accounts
We can use the user accounts to provide access control and protect system resources from unauthorized access. To ensure user data privacy and security, the operating system isolates each user account within its own home directory, separate from other users. Furthermore, the operating system enforces distinct privilege levels for each user account, delineating their access privileges and permissions.
The administrator-guest account is a common example. In which the administrator account has full access to the system while a guest account has limited access.
4. Challenges of Protection in Operating Systems
There are several challenges in implementing protection mechanisms that can effectively prevent unauthorized access and misuse of system resources. Here are some of these challenges:
4.1. Complexity of Modern Operating Systems
One of the main challenges is the complexity of modern operating systems, making it difficult to identify and properly secure all potential vulnerabilities. As operating systems become more complex, there are more potential attack vectors for hackers and other malicious actors to exploit.
Moreover, this requires operating system designers to continuously monitor and update security measures to stay ahead of emerging threats.
4.2. Trade-off Between Security and Usability
Another challenge is the trade-off between security and usability. Protection mechanisms such as user account controls, access permissions, and process isolation can be effective at preventing unauthorized access, but they can also make it more difficult for users to access the resources they need to perform their tasks.
Furthermore, striking a balance between security and usability can be challenging, particularly in systems requiring a high degree of flexibility and customization.
4.3. Potential Security Issues
Different types of protection mechanisms can conflict with one another, leading to potential security issues. For example, a system with strict access controls might be vulnerable to privilege escalation attacks if the controls aren’t properly designed and implemented.
Similarly, a system that relies heavily on process isolation might experience performance issues if too many processes are running concurrently.
4.3. Overhead and Complexity
Protection mechanisms can also introduce additional overhead and complexity to the operating system. This can impact system performance and resource utilization, particularly in systems with limited resources.
As such, operating system designers need to carefully consider the impact of protection mechanisms on system performance and make trade-offs accordingly.
5. Conclusion
In conclusion, domains of protection are essential in modern operating systems to ensure the security and reliability of computer systems.
Memory protection, process isolation, and privilege levels are the key mechanisms that provide isolation and protection between different parts of the operating system or user processes.