1. Introduction
In Linux, one of the most essential parts of using the system is checking for security updates regularly. As security threats continue to evolve and become more sophisticated, it’s important to keep the Linux system up-to-date with the latest security updates.
However, sometimes we may not want to update the entire system, especially if we have any customization on the environment and we want to avoid breaking anything.
In this tutorial, we’ll look at installing security updates on Linux using the apt package manager. Before we start, it’s important to note that different Linux distros have different ways of managing software updates. We’ll focus on Ubuntu, which is one of the most popular Linux distros.
2. Installing Security Updates via the Command Line
To install security updates in Ubuntu via the terminal, we need to use the update and upgrade commands of apt.
The update command fetches the latest version of the package list from the distro’s software repository and any third-party repositories we have configured. The upgrade command downloads and installs an update for all outdated packages and dependencies on the system. However, the process isn’t automatic as we have a chance to review all the incoming changes and approve the upgrades.
Updating Ubuntu using the command line offers us more clarity and authority over the whole process.
Let’s issue the update command to fetch the latest package list from the package manager:
$ sudo apt update
Hit:1 http://ke.archive.ubuntu.com/ubuntu focal InRelease
Get:2 http://ke.archive.ubuntu.com/ubuntu focal-updates InRelease [114 kB]
Get:3 http://ke.archive.ubuntu.com/ubuntu focal-backports InRelease [108 kB]
Get:4 http://ke.archive.ubuntu.com/ubuntu focal-updates/main i386 Packages [817 kB]
..... truncated .....
Hit:30 http://hp.archive.canonical.com focal InRelease
Reading package lists... DoneWe can also issue a command to get a list of all packages that are due for an upgrade:
$ sudo apt list --upgradable
Listing... Done
apache2-bin/focal-updates,focal-security 2.4.41-4ubuntu3.14 amd64 [upgradable from: 2.4.41-4ubuntu3.13]
apache2-data/focal-updates,focal-updates,focal-security,focal-security 2.4.41-4ubuntu3.14 all [upgradable from: 2.4.41-4ubuntu3.13]
apache2-utils/focal-updates,focal-security 2.4.41-4ubuntu3.14 amd64 [upgradable from: 2.4.41-4ubuntu3.13]
.... truncated ....Now, we can install all the packages using the upgrade command:
$ sudo apt upgrade
Reading package lists... Done
Building dependency tree
Reading state information... Done
....truncated....
The following packages will be upgraded:
apache2 apache2-bin apache2-data apache2-utils apparmor apport apport-gtk base-files bind9-dnsutils bind9-host bind9-libs bolt distro-info-data
dnsmasq dnsmasq-base firefox firefox-locale-en fonts-opensymbol forticlient ghostscript ghostscript-x git git-all git-cvs git-daemon-run git-doc
170 upgraded, 5 newly installed, 0 to remove and 0 not upgraded.
114 standard LTS security updates
Need to get 830 MB of archives.
After this operation, 623 MB of additional disk space will be used.
Do you want to continue? [Y/n]Here, we see all existing packages that were automatically installed and are no longer required. We also see all new packages pending installation and the packages that will be upgraded. Moreover, we get to see a summary of all the security updates. Once we confirm the incoming changes, Linux proceeds to install the updates.
We should always expect to have some software packages in the system that depend on one another for proper functioning.
We can perform those updates using the dist-upgrade command:
$ sudo apt dist-upgrade
Reading package lists... Done
Building dependency tree
Reading state information... Done
Calculating upgrade... Done
.... truncated ....This installs any dependent packages.
Finally, we can uninstall any unused packages with autoremove:
$ sudo apt autoremove
Reading package lists... Done
Building dependency tree
Reading state information... Done
The following packages will be REMOVED:
linux-headers-5.14.0-1058-oem linux-headers-5.15.0-60-generic linux-headers-oem-20.04 linux-hwe-5.15-headers-5.15.0-60 linux-image-5.14.0-1058-oem
linux-image-5.15.0-60-generic linux-image-oem-20.04 linux-modules-5.14.0-1058-oem linux-modules-5.15.0-60-generic
.... truncated ....We’ll get a confirmation to approve the removal of all unnecessary packages.
3. Installing Specific Security Updates
Sometimes, we want to avoid doing upgrades for all security packages. This helps us avoid breaking anything, especially in custom environments.
To install a single package, we can specify it:
$ sudo apt install --only-upgrade apache2Here, we’re only installing updates for the Apache package. We’re using the –only-upgrade option to only update packages that are already on the system and ignore requests to install any new packages.
Alternatively, we can use grep to filter security updates alone:
$ sudo apt -s dist-upgrade | grep "^Inst" | grep -i security
Inst xserver-common [2:1.20.13-1ubuntu1.1] (2:1.20.13-1ubuntu1.2 ke.archive.ubuntu.com, security.ubuntu.com [all]) []
Inst xserver-xorg-legacy [2:1.20.13-1ubuntu1.1] (2:1.20.13-1ubuntu1.2 ke.archive.ubuntu.com, security.ubuntu.com [amd64]) []
Inst xserver-xorg-core [2:1.20.13-1ubuntu1.1] (2:1.20.13-1ubuntu1.2 ke.archive.ubuntu.com, security.ubuntu.com [amd64]) [systemd:amd64 ]
Inst gpg-wks-client [2.2.20-1ubuntu4] (2.2.20-1ubuntu4.1 ke.archive.ubuntu.com, security.ubuntu.com [amd64]) [gnupg:amd64 ]
Inst dirmngr [2.2.20-1ubuntu4] (2.2.20-1ubuntu4.1 ke.archive.ubuntu.com, security.ubuntu.com [amd64]) [gnupg:amd64 ]
.... truncated ....Here, we fetch all upgradable packages, then filter the results with grep to only show packages that match the pattern security.
We can install the packages using this command:
$ sudo apt -s dist-upgrade | grep "^Inst" | grep -i securi | awk -F " " {'print $2'} | xargs apt install
We’re piping the earlier output to the awk command that uses the -F option as a field separator to cut out only the package names. They are then passed to the xargs command that installs each security package.
4. Automatically Install All the Latest Security Updates
We can use the unattended-upgrades package to automatically keep the system up to date with all the latest stable security and software updates. It’s available by default on most Ubuntu versions.
Let’s issue the which command to check if it’s available:
$ which unattended-upgrades
/usr/bin/unattended-upgradesIn case it’s not available, we can install the unattended-upgrades package using apt:
$ sudo apt-get install unattended-upgrades
After installation, let’s use the unattended-upgrades command to enable automatic updates:
$ sudo dpkg-reconfigure unattended-upgradesWe should get a dialogue box that prompts us to accept automatic download and installation of stable updates:
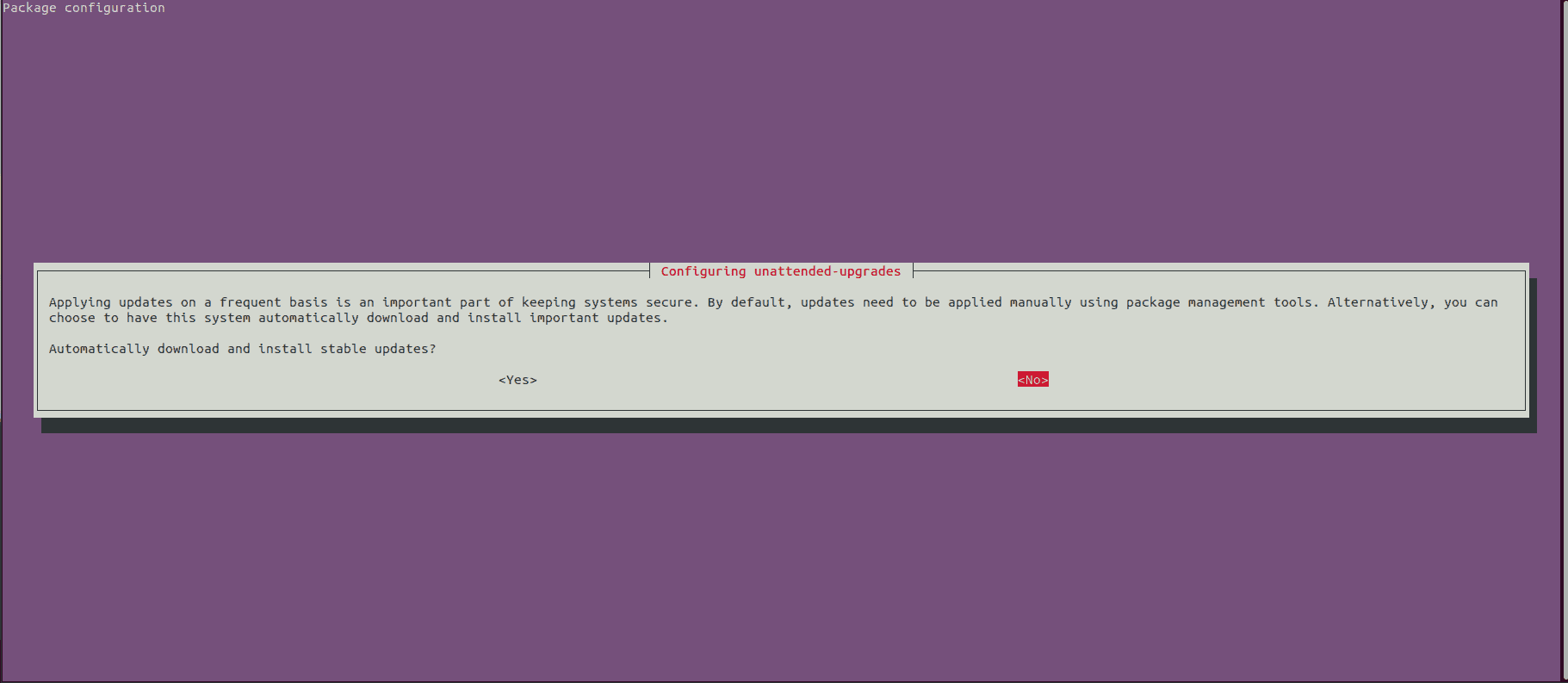
Notably, automated updates may need to restart services. Automatic restarts might not be appropriate for all environments, especially servers.
5. Installing Security Updates via GUI
Another approach we can take is installing the security updates through the Ubuntu Software Center. It includes the list of all installed applications on the system.
To start updating the system through the GUI, let’s search for Ubuntu Software after clicking the super or windows buttons which are used for application launching:

Once open, we click on the Updates tab to see the available software updates:
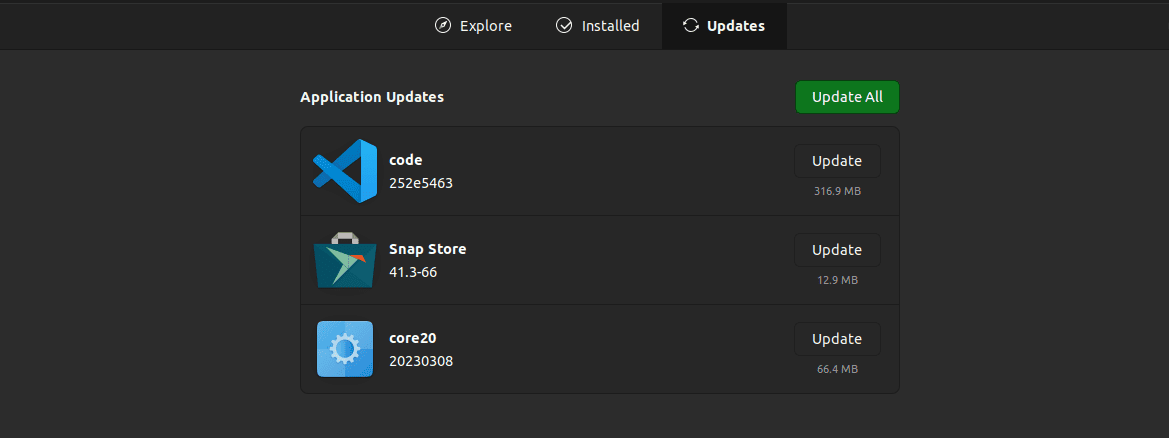
Here, we can choose the software updates to perform on the system.
Alternatively, we can search and open the Software Updater app to check for pending updates. Once open, it starts searching for any available software updates:
Once it’s done scanning, it presents us with a list of all pending software updates and their download sizes:
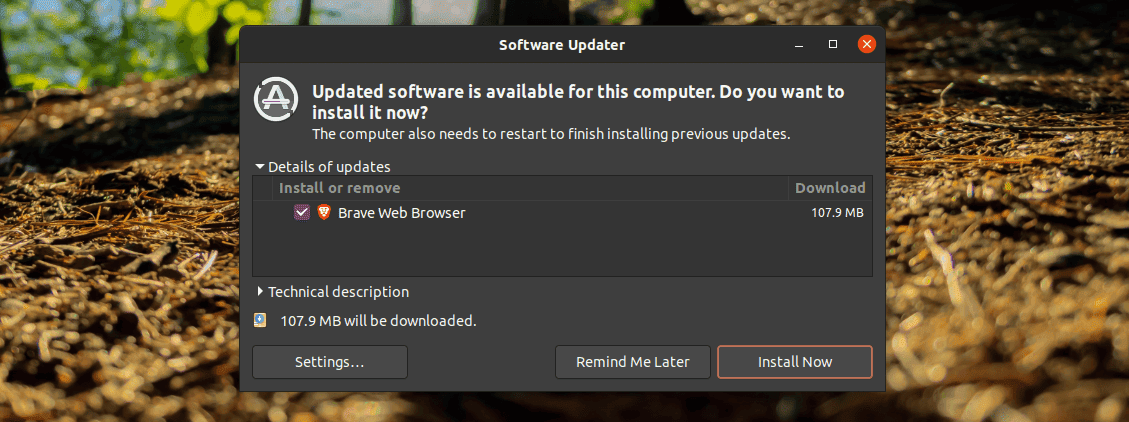
We can check for the software updates we want to download and install or schedule a reminder by clicking the Remind Me Later button. Once the process is done, we may get a window asking us to restart the system to take the changes into effect.
6. Conclusion
In this article, we’ve looked at how to install security updates on Linux.
The first method involves installing updates through the terminal, where we can also configure automatic updates. The second method is about installing updates through the GUI, which might be more appropriate for users who don’t have a lot of experience using the terminal.
Regularly checking for security updates is essential in ensuring we keep our system secure from threats that evolve every day.