Let's get started with a Microservice Architecture with Spring Cloud:
Vigenère Cipher in Java
Last updated: March 24, 2024
1. Introduction
In this article, we’re going to look at the Vigenère cipher. We’ll see how the cipher works, and then, we’ll learn how to implement and reverse it in Java.
2. What Is the Vigenère Cipher?
The Vigenère cipher is a variation on the classic Caeser cipher, only shifting each letter by a different amount.
In the Caeser cipher, we shift every letter in our plaintext by the same amount. For example, if we shift every letter by three places, then the string “BAELDUNG” will become “EDHOGXQJ”:
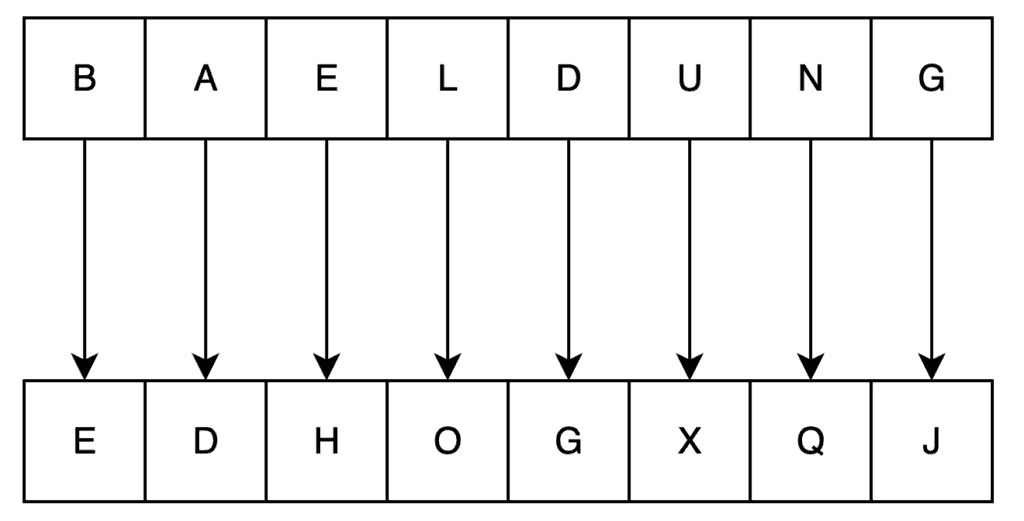
Reversing this cipher is then just a case of shifting the letters by the same amount in the opposite direction.
The Vigenère cipher is exactly the same, only we shift each letter by a different amount. This means that we need a way to represent the cipher key – the amount that each letter is shifted by. This is normally represented by another string of letters, with each letter corresponding to the amount to shift according to its position in the alphabet.
For example, the key “HELLO” would mean shifting the first letter by eight characters, the second by five characters, and so on. So, using this key, the string “BAELDUNG” would now become “JFQXSCSS”:
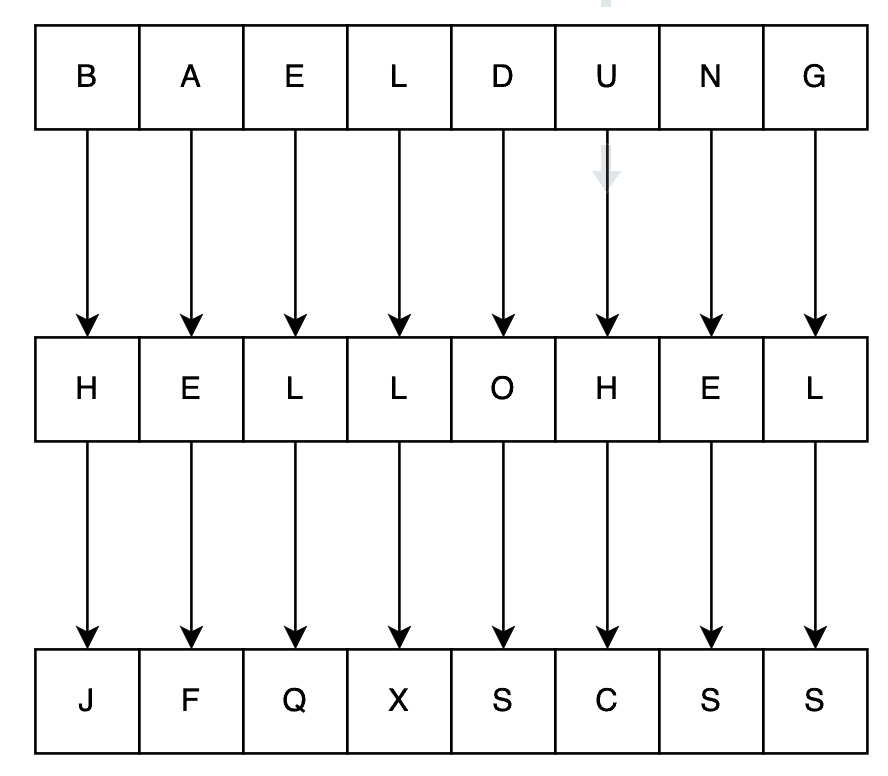
3. Implementing Vigenère Cipher
Now that we know how the Vigenère cipher works, let’s look at implementing it in Java.
We’ll start with the method that’s going to be our cipher:
public String encode(String input, String key) {
String result = "";
for (char c : input.toCharArray()) {
result += c;
}
return result;
}As written, this method isn’t very useful. It just builds an output string that’s identical to the input string.
The next thing we want to do is get the character from our key to use for each input character. We’re going to have a counter for the key position that we’re using next, and then increment that on each pass:
int keyPosition = 0;
for (char c : input.toCharArray()) {
char k = key.charAt(keyPosition % key.length());
keyPosition++;
.....
}
This looks a bit scary, so let’s work through it. First, we apply the modulo of our key position with the overall key length, which simply means that it’ll wrap around when it reaches the end of the string. We then take the character at this position, which is our key character for this position of the input string.
Finally, we need to adjust our input character based on the key character:
String characters = "ABCDEFGHIJKLMNOPQRSTUVWXYZ";
.....
int charIndex = characters.indexOf(c);
int keyIndex = characters.indexOf(k);
int newCharIndex = (charIndex + keyIndex + 1) % characters.length();
c = characters.charAt(newCharIndex);
Here, we have a string containing all the characters we can support. We then find the index in this string of both our input character and our key character. We can then simply add these together to get our new character position.
Note that we’re adding one to this as well since we want our key letters to be one-indexed instead of zero-indexed. That is, an “A” in the key should act as shifting by one letter, instead of shifting by zero letters. We’re also doing another modulo by the number of possible characters so that it all wraps around again.
However, this doesn’t quite work. In particular, this will only work correctly if every character in both the input string and the key is in our supported list. To fix this, we need to only increment the key position if our input character is a supported one, and to only generate a new character if both the input and key characters are supported:
if (charIndex >= 0) {
if (keyIndex >= 0) {
int newCharIndex = (charIndex + keyIndex + 1) % characters.length();
c = characters.charAt(newCharIndex);
}
keyPosition++;
}
At this point, our cipher is complete and works.
3.1. Worked Demonstration
Now that we’ve got a working implementation of the cipher, let’s see it in action. We’re going to encode the string “VIGENERE CIPHER IN JAVA” with the key “BAELDUNG”.
We start with a keyPosition of 0. Our first iteration then gives us:
- c = “V”
- k = “B”
- charIndex = 21
- keyIndex = 1
- newCharIndex = 23
This gives us the resulting character of “X”.
Our second iteration would then be:
- keyPosition = 1
- c = “I”
- k = “A”
- charIndex = 8
- keyIndex = 0
- newCharIndex = 9
Which gives us a resulting character of “J“.
Let’s jump ahead. Looking at character nine:
- keyPosition = 9
- c = ” “
- k = “B”.
- charIndex = -1
- keyIndex = 1
There are two interesting things here. Firstly, we note that our key position has exceeded the length of the key, so we’re wrapping around to the start again. Secondly, our input character isn’t a supported one, so we’re going to skip encoding this one.
If we keep going until the end, we’ll end up with “XJLQRZFL EJUTIM WU LBAM”.
4. Decoding Vigenère Cipher
Now that we can encode things with the Vigenère cipher, we need to be able to decode them as well.
Perhaps unsurprisingly, the vast majority of the decoding algorithm is identical to encoding. After all, we’re just shifting the characters around by an amount based on the correct key position.
The part that differs is the direction that we need to shift in. Our newCharIndex needs to be calculated using subtraction instead of addition. However, we’ll also need to do the modulo calculation by hand, since it doesn’t work correctly in this direction:
int newCharIndex = charIndex - keyIndex - 1;
if (newCharIndex < 0) {
newCharIndex = characters.length() + newCharIndex;
}
With this algorithm version, we can now successfully reverse the cipher. For example, let’s try to decode our previous string “XJLQRZFL EJUTIM WU LBAM” with the key “BAELDUNG”.
As before, our key position starts at 0. Our first input character is “X” – which is character index 23, and our first key character is “B” – which is character index 1.
Our new character index is then 23 – 1 – 1, which is 21. This is then a “V” when converted back.
If we continue for the entire string, we’ll get a result of “VIGENERE CIPHER IN JAVA”.
5. Vigenère Cipher Adjustments
Now that we’ve seen how to implement the Vigenère cipher in Java, let’s look at some adjustments that we can make. We’re not going to actually implement them here – this is left as an exercise to the reader.
Any changes made to the cipher need to be done equally on both the encoding and decoding sides, otherwise, the encoded messages won’t be readable. This also means that any attacker who doesn’t know the changes we’ve made will have a much harder time attacking any encoded messages.
The first and most obvious change that can be made is to the set of used characters. We can add more supported characters – those having accents, whitespace, and others. This will then allow a wider set of characters to be used in the input string, and it’ll adjust how all characters are represented in the output string. For example, if we simply add a space as an allowed character, then encoding “VIGENERE CIPHER IN JAVA” with the key “BAELDUNG” results in “XJLQRZELBDNALZEGKOEVEPO” instead.
We can also change the order of the characters in our mapping string. If they’re not in strict alphabetical order, everything will still work, but the results will be different. For example, if we change our characters string to “JQFVHPWORZSLNMKYCGBUXIEDTA”, then encoding the string “BAELDUNG” with the key “HELLO” now produces “DERDPTZV” instead of “JFQXSCSS”.
We can make plenty of other alterations, but these will tend to shift us further away from a real Vigenère cipher. For example, we could swap the encoding and decoding algorithms – encoding by shifting backwards in the alphabet and decoding by shifting forward. This is commonly known as Variant Beaufort.
6. Conclusion
Here, we’ve seen an introduction to the Vigenère cipher and how it works. We’ve also seen how we can implement this ourselves in Java to encode and decode messages. Finally, we’ve seen a few adjustments that we can make to the algorithm to improve its security. Why not try implementing some of this yourself?
The code backing this article is available on GitHub. Once you're logged in as a Baeldung Pro Member, start learning and coding on the project.

















