Learn through the super-clean Baeldung Pro experience:
>> Membership and Baeldung Pro.
No ads, dark-mode and 6 months free of IntelliJ Idea Ultimate to start with.
Last updated: March 18, 2024
As business increases the use of digital information systems, new risks and threats arise. The information age brings newer opportunities and markets, lowered costs, and easier customer and vendor relationship improvements. However, it also presents new issues and menaces. That is why, in information security, one of the critical processes is incident and event management.
In this tutorial, we’ll check out the main concepts of this process. We’ll review the tools we may have to deal with this critical part of our information security toolset.
According to the NIST, in information security, an Information Security Incident is:
“An occurrence that actually or potentially jeopardizes the confidentiality, integrity, or availability of an information system or the information the system processes, stores, or transmits or that constitutes a violation or imminent threat of violation of security policies, security procedures, or acceptable use policies”.
Also, an Event is any occurrence or change in a set of circumstances. An event may or may not be related to incidents. Regardless, events must be made known and acknowledged.
So, Information Security Incident and Event Management (SIEM) is the process that will manage any incident or event. It seems simple enough, but it is far from it. This process, usually implemented with the help of SIEM-specialized software, encompasses at least:
Once again, we’ll refer to the NIST. This Institute proposed an Incident Handling Lifecycle that brings a good light on how we may respond to information security incidents:
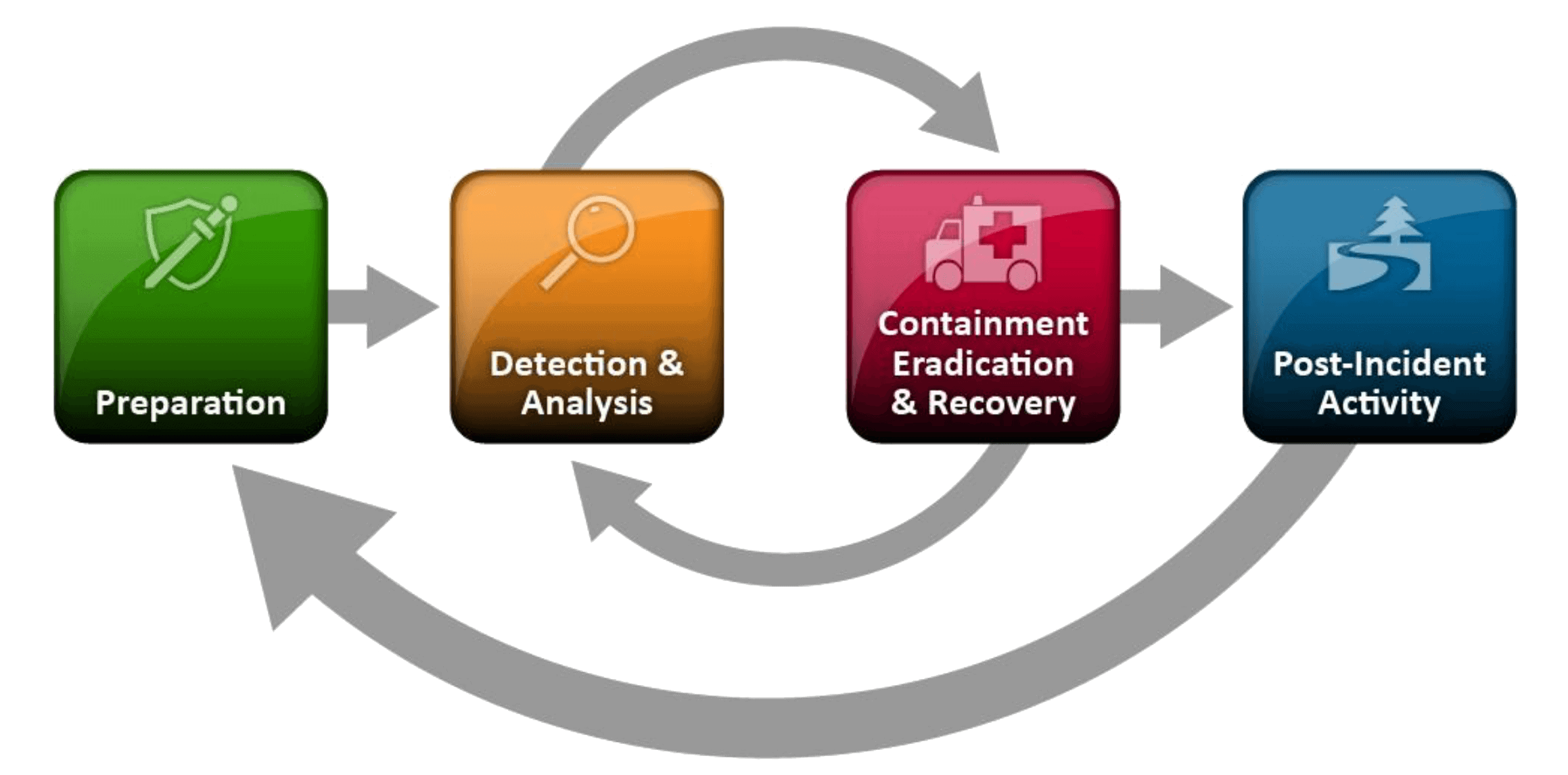
According to the NIST, a proper incident addressing may include
The term SIEM may refer to the incident management discipline and the software toolset to do that. A full SIEM software suite should be able to cover all incident lifecycle phases. And that is not an easy task.
Major corporations may have tens to hundreds of thousands of active elements in their information systems infrastructures. Their activities must be logged and analyzed to ensure that incidents are detected. In many cases, just some raw log lines are not enough to trigger attention. In those environments, we may see several millions of daily log entries.
In any case, SIEM software will have at least the following roles:
That set of functions differentiates it from IDS/IPS Software, also important tools in the security environment. They are, in fact, complementary since they must send their audit logs to the SIEM software.
There are a lot of software SIEM solutions, such as Splunk Enterprise Security, Alienvault OSSIM, Elastic SIEM, Wazuh, FortiNet FortiSiem, Exabeam, IBM QRadar SIEM, LogRhythm, RSA Netwitness. Selecting the best for our case, however, depends on several factors, to name a few:
As we can imagine, deploying a SIEM involves a lot of work. We must ensure that it receives the audit events of the majority or entirety of network elements and major business systems. Moreover, even though the tools come with a comprehensive set of rules, we must devise detection, correlation, and automation rules that make sense to our business.
For instance, we can use SIEM to alert odd behavior on any system to ensure that those transactions are promptly monitored and analyzed.
Finally, we must create the incident policies and design its handling workflow procedures. Assigning roles to everyone involved. That includes not only the information security analysts but also business management, and legal and compliance staff, for instance.
In this tutorial, we discussed one of the key components to manage Information Security. The SIEM is a critical part of any cyber-security initiative and one of the main tools for security team operations‘. SIEM Software can monitor events, help manage incidents, and prevent damage and liability.