Learn through the super-clean Baeldung Pro experience:
>> Membership and Baeldung Pro.
No ads, dark-mode and 6 months free of IntelliJ Idea Ultimate to start with.
Last updated: June 21, 2023
Risk management, risk assessment, and risk analysis are all different concepts. They are, nevertheless, frequently used interchangeably. Risk assessment is essentially information, risk analysis is processing, and risk management is the plan of action.
In this tutorial, we’ll learn about the difference between these concepts. But, before doing this, let’s start with the definition of the risk.
Risk is the likelihood that the result will be different from what is anticipated. It is uncertainty’s impact on or presence inside information and technology.
Cybersecurity risks are related to the loss of information, data, or information (or control) systems’ confidentiality, integrity, or availability and reflect the potential for negative effects on an organization’s operations (i.e., mission, functions, image, or reputation), assets, people, and other organizations.
Examples of cybersecurity risks are:
Cybersecurity risk has the potential to negatively impact online transactions involving money or sensitive information. Cyber risks are frequently associated with circumstances that could result in data breaches. It is measured as follows:
Cyber risk = Threat Vulnerability
Information Value
Threat is any situation or event that may have the potential to negatively affect an organization’s operations (including its mission, functions, image, or reputation), assets, or people through the use of an information system, whether through unauthorized access, information destruction, disclosure, modification, or denial of service. A threat source’s capability to successfully exploit a certain information system vulnerability is another consideration.
Vulnerability is a weakness that could be exploited or activated by a threat source in a system’s internal controls, security protocols, or implementation. Deficit is the same thing as weakness. Security and/or privacy problems could be caused by weaknesses.
Information value is a qualitative measurement of the importance of information based on variables such as the level of robustness of information assurance (IA) controls assigned to information protection based on factors such as mission criticality, sensitivity (e.g., classification and compartmentalization), releasability to other countries, perishability/longevity of the information (e.g., short life data versus long life intelligence source data).
Risk analysis comprises evaluating each risk to the data, devices, and information security of our company and ranking the potential dangers. One step in the whole risk management and risk assessment process is a risk analysis.
Once the analysis is completed, we’ll know how to allocate our resources to protect against cyberattacks and which systems to prioritize in the event of a data breach to ensure minimal or no disruption to our business operations.
Many regulatory bodies and cybersecurity frameworks require cybersecurity risk assessments. Organizations that perform studies on a regular basis as part of their IT security strategy get a variety of benefits. These are long-term cost reduction, organizational awareness and prevention of data loss or breach.
The core evaluation step in the larger risk management and assessment processes is risk analysis. The relevance of the risk variables found throughout the risk assessment process is determined by a preliminary factor analysis of information risk.
Additionally, risk analysis defines risk by calculating the likelihood of dangers happening and tolerances for specific occurrences. One illustration is when an auditor determines the likelihood and size of a prospective loss.
The likelihood of occurrence and the projected magnitude of potential consequences are taken into account when scoring the identified risks. Together, these factors make it easy to rank risks and establish a plan for reducing them.
The qualitative risk analysis approach prioritizes the risk on the project by assigning a likelihood and impact number to each risk. The relevance of the outcomes of a risk event is defined as its impact, whereas the possibility that a risk event will occur is defined as its probability.
The purpose of qualitative risk analysis is to evaluate and score the characteristics of each newly identified risk before prioritizing them based on those characteristics. Each risk is evaluated individually, taking into account its potential of occurrence as well as its influence on the project’s goals.
Dangers will be weeded out more effectively if they are classified. The project’s risk exposure is calculated through qualitative analysis by dividing the chance by the impact.
Quantitative risk analysis is used to statistically assess the overall impact of risk on the project’s goals. It is used to assess the likelihood that the project’s objectives will be met and to generate a contingency reserve, which is normally relevant for both time and money.
Quantitative analysis is not required, especially for smaller projects. The main problem, calculating estimates of the overall project risk, is made easier by quantitative risk analysis.
A risk assessment evaluates a company’s capacity to safeguard its data and IT infrastructure against online dangers. Identification, evaluation, and prioritization of risks to information and information systems are the objectives of a cybersecurity risk assessment.
Organizations can identify and prioritize areas for improvement in their cybersecurity program with the use of a cybersecurity risk assessment. Additionally, it enables organizations to effectively communicate their risks to key constituencies and allocate resources in a way that minimizes those risks.
Briefly, risk assessment is an investigation using methods and tools to find, assess, and document any risk-related issues.
The identification and analysis phases of risk management are the main emphasis of risk assessment, which is a “key component” of the process.
A cybersecurity risk assessment is crucial because it can reveal threats to the data, networks, and systems of our company. We can take action to mitigate or reduce these hazards by being aware of them.
A risk analysis can assist our business in creating a strategy for countering and recovering from a cyberattack. To keep their risk profiles up-to-date organizations should regularly carry out cybersecurity risk assessments. A new risk assessment should be carried out if an organization’s computer networks or systems are modified.
A cybersecurity risk assessment examines a company’s vulnerabilities and threats to evaluate the risks it faces. It also makes recommendations for mitigating such risks. Typically, a risk calculation and appraisal are performed, and then controls are selected to handle the risks detected.
Continuous monitoring and assessment of the risk environment is critical for identifying changes in the organization’s context and keeping track of the entire risk management process. We can recognize and classify hazards with the use of risk assessment. Additionally, it offers a summary of possible outcomes.
Let’s use an example of a cyber-security risk assessment and assume that a SQL injection attack might be categorized as “Likely” or “Highly Likely” if the possibility of the attack is “Likely” or “Highly Likely.”
A risk assessment matrix, also known as a probability and severity risk matrix, is a visual tool that depicts different risks that could impact a company:
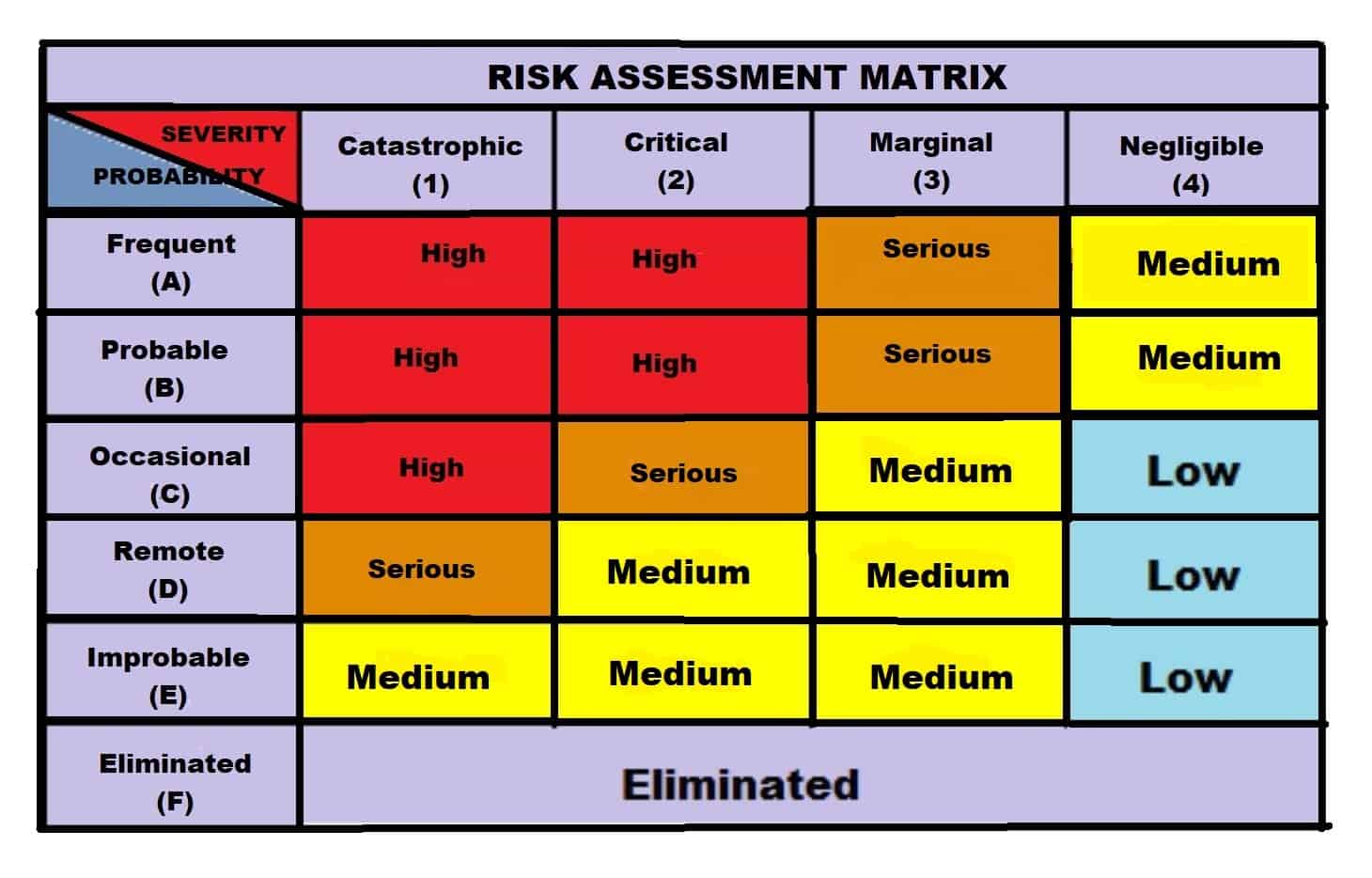
Severity is a measure of the impact of a risk or the possible consequences of a hazard.
The frequency of harm associated with a risk is proportional to its probability. Probability is also known as “Likelihood”, “Rate of Occurrence”, or “Frequency” of occurrence of the risk.
The risk event’s likelihood and the potential impact on the business are two intersecting components that constitute the foundation of the risk matrix. In other words, it’s a tool that shows us how likely a risk is in relation to how significant it is.
Risk management is the process of identifying, assessing, evaluating, and responding to the threats. Employees and business unit leaders usually view risk management through the lens of their own business function. Unfortunately, they lack the broad perspective needed to address risk in a thorough and consistent manner.
Risk management includes the identification, analysis, assessment, and prioritizing of current and potential hazards. This allows us to manage risk and financial resources while addressing loss exposures to mitigate any potential negative consequences.
Furthermore, having effective risk management strategies built into our business plan allows us to fully capitalize on risk avoidance opportunities.
Organizations typically follow a four-step procedure for managing risk, starting with risk identification. The possibility of threats exploiting vulnerabilities and the possible impact are used to assess risk next.
Organizations choose from a variety of risk mitigation measures after prioritizing risks. The fourth phase, monitoring, is designed to keep controls and risk responses up to date despite a constantly changing environment.
When it comes to risk, cybersecurity risk management is the comprehensive umbrella. There is risk analysis as well as risk assessment. Another example of risk management is the fact that risk management is an essential component of the medical device product development lifecycle.
It assists medical device developers in ensuring that their product is dependable, performs as planned, and poses no risk to patients, operators, or the environment. In other words, the risk management cycle’s primary goal is to limit or lessen the likelihood of product failure.
It might be tough to navigate through the different risk-related words, such as risk analysis, risk management, and risk assessment. The most significant distinction is in the extent of these concepts. The relationship between risk analysis, risk assessment and risk management are shown in the following figure:
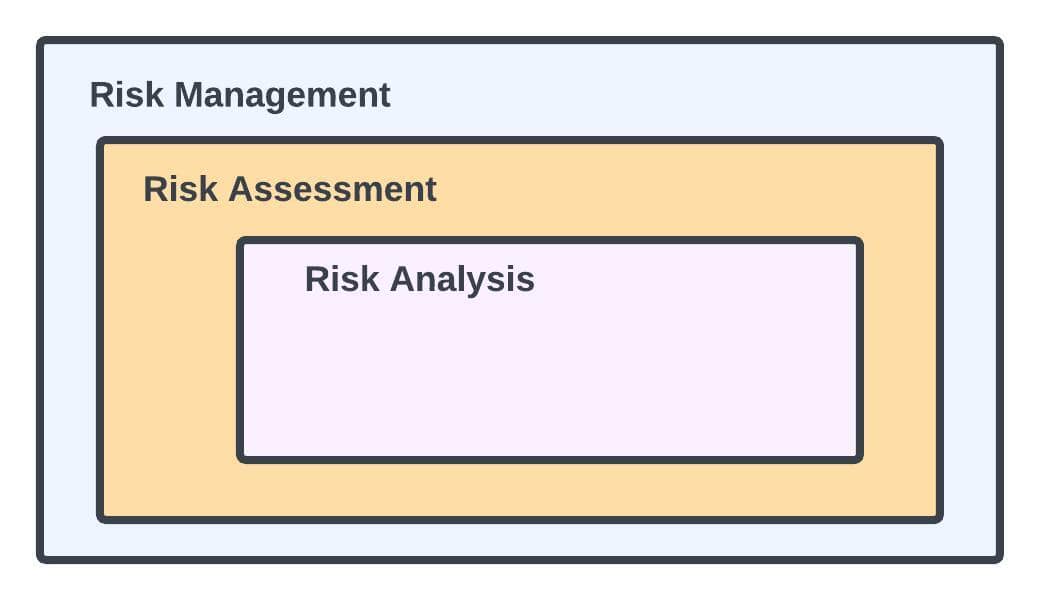
The macro-level process of evaluating, analyzing, prioritizing, and developing a plan for reducing risks and managing risk to an organization’s assets and revenues is known as risk management.
A mid-level procedure in risk management is risk assessment. It seeks to categorize hazards into manageable groups and outline every probable effect of each risk.
The micro-level process of analyzing risks and the consequences of such risks is known as risk analysis.
The concepts of risk, risk assessment, and risk analysis apply to several components of the risk management process.
Although some of the definitions of those terms overlap, risk management generally refers to the entire procedure from risk identification to risk monitoring.
Risk analysis quantifies risk, whereas risk assessment focuses on finding and assessing risk.
If we understand the differences between these expressions, we may find it easier to guarantee that expectations regarding the risk assessment process are explicit and that the task is done correctly.
In this tutorial, we learned about risk, risk analysis, risk assessment and risk management. Then we realized that, while these terms are used interchangeably, they are not interchangeable. In a nutshell, risk management entails risk assessment and risk analysis. The risk assessment process includes risk analysis. Risk analysis and risk assessment, in other words, are components of risk management.