Learn through the super-clean Baeldung Pro experience:
>> Membership and Baeldung Pro.
No ads, dark-mode and 6 months free of IntelliJ Idea Ultimate to start with.
Last updated: March 18, 2024
In this tutorial, we’ll look at what Wardriving is and how it works while also going through some of the ethical and privacy considerations it raises. Finally, we’ll discuss the purposes it serves and ways we can protect ourselves from it.
Connectivity has become a huge part of our everyday lives – as far as becoming from luxury to almost a certain basic need. With the nature of wireless networking, as it is today, it is no surprise that we can connect to the Internet from almost anywhere, homes, cafes, public places, and even some metro stations.
The abundance of wireless networks has also broadened the attacking surface of hackers. While not all networks can be easily breached, hackers can try to gather information on as many such networks as possible to enhance their chances of success.
The act of driving around in a vehicle equipped with a wireless-enabled device to detect and map Wi-Fi access points is called Wardriving.
The essential equipment needed for Wardriving is a laptop, a smartphone, or another portable electronic device (nowadays, a Raspberry Pie or an Arduino board may do) with a Wi-Fi adapter and a GPS device. The laptop or smartphone device is used to detect and identify Wi-Fi networks, while the GPS device is used to keep the location of each of them.
One popular software for Wardriving is Kismet, an open-source tool that can run on various operating systems. This software scans for Wi-Fi networks’ access points, identify the type of security used (if any), and displays the network’s signal strength. Kismet runs on all Windows, Linux, and MacOS. It can be used in combination with other software to log the network’s location or scan for some well-known vulnerabilities – for example, in the case of an administrator trying to make sure that their networks are up to date.
Another useful tool for Wardriving is a Wi-Fi scanner app for smartphones, such as Wi-Fi Analyzer for Android or Wi-Fi Finder for iOS. These apps scan for Wi-Fi networks, display their signal strength, and map their locations.
The main purpose of Wardriving is to identify the presence and location of Wi-Fi networks. This information can then be used to map the Wi-Fi network mesh in a specific area. This, in turn, can be useful for various reasons: from individuals looking to connect to a Wi-Fi network to businesses looking to improve their Wi-Fi coverage. The mapping of Wi-Fi access point locations in an area can also be used in some civil planning cases, for example, in building free Wi-Fi infrastructure in a city, where the responsible authorities would need to know the scale and type of coverage they are getting. In the following diagram, we see several network access points that a Wardriver can identify during a run:
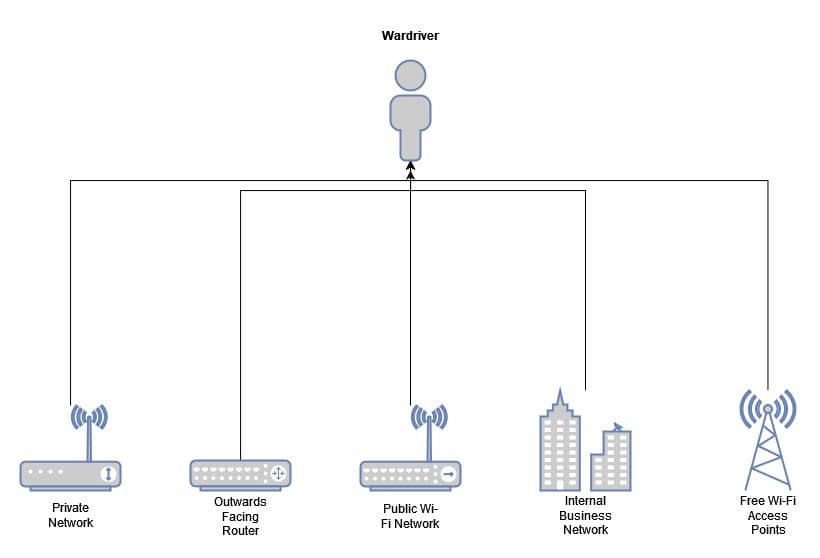
Another purpose of Wardriving is to assist in pinpointing security vulnerabilities in wireless networks. Wardrivers can use that information to determine if a network is properly secured – meaning there are weak points that could be exploited by malicious actors. This can be important for individuals concerned about their Wi-Fi network’s security and businesses who need to protect sensitive information.
Keep in mind that the act of identifying a network’s location, signal strength, and maybe also protection features does not by itself give away any vulnerabilities, nor does it imply security – extra specific research is to be carried out by experts to get to those conclusions.
It becomes clear from the above point that, as with most things concerning cybersecurity, Wardriving as a tool can be used by both attackers and defenders alike. Attackers use this as a reconnaissance tool to identify weaknesses in public and private Wi-Fi networks. In contrast, defenders use it to catch up to the latest bugs in their topologies – while also trying to anticipate the vulnerabilities in their networks.
Finally, Wardriving can also be used for competitive purposes. One such case is in Wardriving contests, where participants compete to see who can map the most Wi-Fi access points in a specific area. This is done on a hobby basis, usually well monitored in countries that allow the practice.
Wardriving can have security implications, depending on the actor performing it. By mapping Wi-Fi networks, Wardrivers can identify whole areas where the security of wireless networks is mediocre. In the case that this is used by malicious actors to gain unauthorized access to Wi-Fi networks and steal sensitive information, like financial data or personal information, the law has probably been broken. We should secure our Wi-Fi networks with strong passwords and encryption to protect ourselves, as we’ll see later in this article.
Even if their intent is non-malicious, Wardrivers can have legal implications depending on their country. While Wardriving is not illegal in most countries, there are some important legal considerations to keep in mind. For example, in some countries, accessing someone else’s Wi-Fi network is illegal without permission. Additionally, some countries have laws prohibiting the interception of Wi-Fi signals, even if they are unsecured or unencrypted. Wardrivers should be familiar with the laws in their jurisdiction and take appropriate steps to avoid breaking the law.
Protection against Wardrivers comes down to the same important measures of protecting your Wi-Fi networks. The major things we should keep in mind are:
These things can give most users up to an excellent level of security regarding wireless networks.
In this article, we took a closer look at the term Wardriving. We discussed what it is and how it is done, and we also looked into its ethical complications and protection methods. Stay safe!