Learn through the super-clean Baeldung Pro experience:
>> Membership and Baeldung Pro.
No ads, dark-mode and 6 months free of IntelliJ Idea Ultimate to start with.
Last updated: March 18, 2024
In this tutorial, we’ll look at what a rogue access point (AP) is and how it can damage our networks. We’ll see what evil twin access points are and how the evil twin attack works while also discussing how we can protect our networks from these threats.
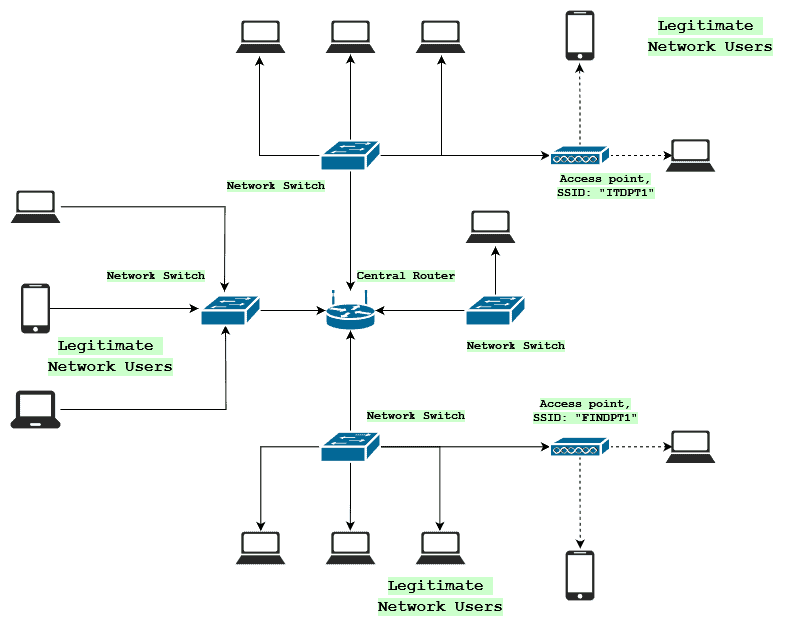
Today, we will talk about rogue and evil twin access points. These two different types of APs have a lot of features in common but also some specific differences. For the rest of this tutorial, we use the following topology to demonstrate how these APs affect a network:
Rogue access points refer to unauthorized or malicious wireless access points on a network. These are deployed without proper authorization or prior oversight. Rogue access points can pose significant security risks to both wired and wireless networks. A rogue access point can take the form of physical devices, such as routers or physical access points, or a software-based virtual access point running off a device already connected to the network.
When inserted into a network, these access points can pose serious threats. These APs are installed without the guidance of network administrators. Given that, it is usually the case that these APs are not correctly configured. Among the misconfigurations are weak passwords, weak authentication protocols, or a complete lack of them.
Rogue access points are not always malicious. Despite the term’s connotation, unauthorized access points can emerge from non-malicious sources. These instances often result from users or employees innocently setting up access points to enhance connectivity. These unintentional rogue access points can lead to security gaps and network disruptions. We should not assume malicious intent in all cases.
A rogue access point within a network would look like so:
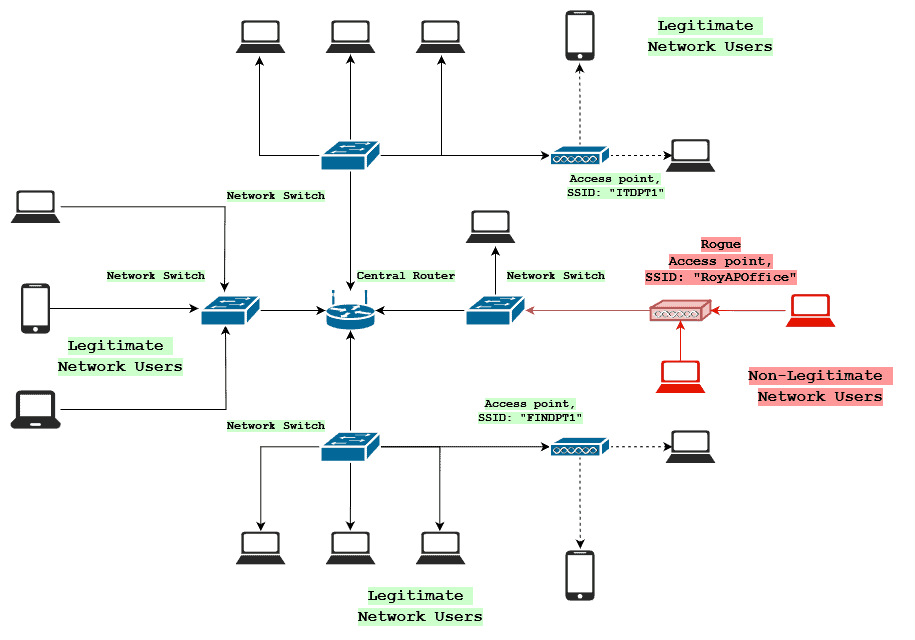
Notice that the AP’s name (SSID) is a useful name, pointing to the fact that this rogue access point was probably set up by a non-malicious network user.
An evil twin is a rogue wireless access point that impersonates a legitimate network bearing a name similar to a trusted AP. Attackers install such APs to trick users into connecting to them instead of the legitimate ones. Once connected, the user’s data traffic becomes vulnerable to interception and manipulation by the attacker. This form of attack is particularly effective in public spaces.
The mechanics of an evil twin attack are deceptively simple. When users search for available Wi-Fi networks, their devices broadcast signals to inquire about nearby APs. The attacker’s rogue access point responds by mimicking the target network’s name (SSID) and often duplicating its security features to avoid detection. Users, assuming they are connecting to a familiar and secure network, connect to the evil twin without realizing it.
Once connected, the attacker gains the ability to eavesdrop on sensitive data transmitted between the user’s device and the internet. This can include login credentials, personal information, and even payment details.
Apart from damage to the users, evil twin APs can also damage the network’s security. Attackers gather data that are supposed to be delivered deeper into the network from the evil twin. This may include sensitive network data – such as passwords, IPs, and MAC addresses – that can be used to further advance an attack to the network. Therefore, evil twins can be used as footholds from where attacks targeting other network devices start.
Contrary to a rogue AP inside a network, an evil twin access point would look like so:
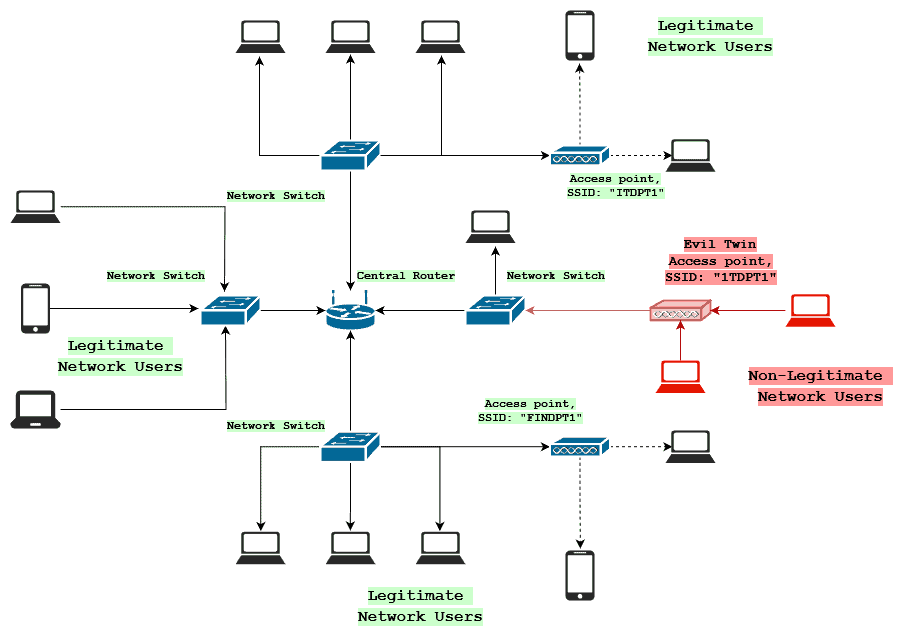
Notice the SSID “1TDPT1”. This is deliberately named very closely to the existing AP “ITDPT1” by replacing an “I” with a “1”. The malicious actor is trying to trick users into connecting to this AP instead of the legitimate one to gain access to the transmitted information.
The main difference we can use to distinguish between rogue access points and evil twin access points is their SSID. This stems from the different motives behind each type. We talked about how rogue APs are not always malicious and are usually set up for convenience. The danger they pose comes from the ignorance of the users setting it up. On the other hand, evil twins are deliberately set up to mimic a legitimate access point and are actively trying to trick users.
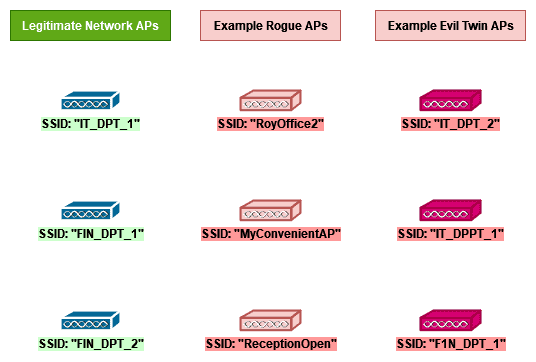
In the following picture, we can see how the SSIDs of each type usually differ to have a more complete understanding:
Having rogue access points within a network introduces specific risks that jeopardize its security and functionality. These unauthorized entry points act as potential gateways for cybercriminals, allowing them to infiltrate the network undetected.
This infiltration can lead to data breaches, where sensitive information is stolen or manipulated. Moreover, rogue access points pave the way for man-in-the-middle attacks. In these attacks, hackers intercept and manipulate data between users and legitimate network resources. Such attacks enable eavesdropping, credential theft, and the injection of malicious content.
Additionally, these unauthorized access points often lack the same security measures as official ones, leaving the network vulnerable to malware infection, unauthorized access, and data manipulation. In essence, the presence of rogue access points creates weak points in the network’s armor, offering cybercriminals ways to exploit vulnerabilities and compromise the security of the system.
Similarly, evil twin access points pose distinct risks that can undermine network security. Unlike rogue access points that discreetly create unauthorized entryways, evil twins use deceit to lure users into connecting to them.
This tactic opens the door to data interception, as attackers can easily eavesdrop on user communications without their knowledge. Furthermore, evil twins can escalate the risks of phishing attacks by crafting convincing fake networks. These fake networks trick users into revealing sensitive information like passwords and personal data. Compared to rogue access points, evil twins exploit user trust and reliance on recognizable network names.
While both rogue and evil twin access points share the potential for unauthorized access and data compromise, evil twins distinctly exploit human psychology, posing an even greater threat to unsuspecting network users.
There are several countermeasures to deploy to protect both against rogue access points as well as evil twins. Some apply to both categories, while others target only one of them.
Protecting our networks against the threats posed by rogue access points requires both awareness and robustness. Regular network monitoring and scanning are essential to identify any unauthorized devices or access points that may have infiltrated the system. Implementing strong security protocols, such as robust encryption methods and secure authentication procedures, helps fortify network entry points against unauthorized access.
Employing network segmentation can isolate critical resources from potential breaches, limiting the impact of rogue access points. In addition, intrusion detection systems provide real-time alerts about any unusual network activities, allowing administrators to quickly respond to potential threats.
However, no approach is complete without raising user awareness. Educating network users about the risks of connecting to unknown networks and emphasizing the importance of verifying network authenticity before connecting is crucial. Users should also understand the dangers of setting up arbitrary APs that may be useful but also harmful to the network’s security. By combining technological defenses, user education, and vigilant oversight, organizations can establish a resilient shield against the stealthy incursions of rogue access points.
Defending from evil twins involves a strategic blend of technical measures and user education. First, we should use strong security codes to protect the information traveling through the network. Similarly, employing state-of-the-art and strong encryption protocols enhances the safety of data on the network.
A more active approach includes existing monitoring tools that can watch out for suspicious activity in the network and alert us if something is wrong. Employing network monitoring tools capable of detecting irregularities in signal strength and network behavior serves as an effective preemptive defense.
It’s imperative to educate network users about the significance of verifying authentic network identifiers from trusted sources. Encouraging the usage of virtual private networks (VPNs) can provide an added security layer by encrypting data traffic. Users who are aware of the existence of evil twins are much more likely to spot a suspicious SSID.
By combining these proactive strategies and creating a culture of cybersecurity awareness among users, network administrators can significantly fortify their networks against the potential exploits of cunning evil twin access points.
In this article, we talked about rogue access points and evil twin access points. We showed what these two categories of access points are.
First, we discussed how rogue access points are APs that are set up arbitrarily inside a network and are not always malicious. Then we got into how evil twins are tricking users into connecting to them instead of legitimate APs by using similar SSIDs to real access points.
We also saw what we can do to protect our networks and devices from both of these types of APs. We talked about how crucial user education is, as well as how monitoring and strong protocols are imperative for a network to work securely.