Yes, we're now running our Black Friday Sale. All Access and Pro are 33% off until 2nd December, 2025:
What is RFID and How Does It Work?
Last updated: March 18, 2024
1. Introduction
In this tutorial, we’ll explore the RFID’s origin, families, components, working principle and global frequency allocation.
2. Auto-ID Technologies
Since its establishment by MIT researchers in 1999, the realm of automatic identification technology, which we call auto-ID for short, has continuously expanded.
Auto-ID technologies form a diverse array that enables us to automatically and precisely capture, identify, and store data related to objects, items, or individuals, eliminating manual data entry. These technologies help us to optimize data capture, bolster accuracy, and heighten efficiency in various industries.
Key players within auto-ID are barcodes, contact memory, and RFID technologies. Additional auto-ID methods comprise QR codes, biometrics, magnetic stripes, optical character recognition (OCR), voice recognition, real-time location systems (RTLS), and other emerging technologies.
While we have established the barcode system as a reliable auto-ID technology, RFID is rising as its prominent successor.
This article focuses on the RFID system’s functionality and operation.
3. What Is RFID?
Radio Frequency Identification is known as RFID. It is a technology that helps us wirelessly identify and track items or persons using magnetic induction or radio waves.
We employ unique numbers that are stored on microchips and can be read automatically, as opposed to bar codes, which need to be manually scanned, to identify things, people, and information.
All RFID systems are composed of three main components:
- RFID tag, which we also call a transponder, is located on the object to be identified and is the data carrier in the RFID system.
- RFID reader or a transceiver. We use this component to read and write data to a transponder.
- RFID middleware. This is the data processing component, which we utilize in some useful manner to process the data we obtain from the transceiver.
We’ll discuss these components more extensively in subsequent sections of this article.
Next, let’s consider the families of the RFID.
3.1. Families of RFID
Within the realm of RFID technology, we encounter two key families:
- Near-field RFID
- Far-field RFID
For the near-field RFID family, we use Faraday’s magnetic induction principle, often referred to as magnetic coupling. In this family, both the reader and the tag incorporate coils. By activating the tag’s modifiable transponder chip, we facilitate exchanges over distances of a few centimeters.
We show a visual representation of a near-field RFID system in the figure provided:
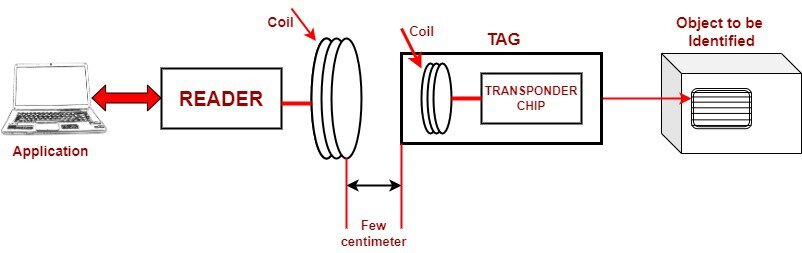
We use near-field RFID mainly for cards and access control. However, due to its confined range, we hardly use it to manage goods.
Conversely, we employ the use of electromagnetic waves for the far-field RFID families to propagate information through antennas situated in both the reader and the tag.
We show a basic schematic for a far-field RFID configuration in the figure below:
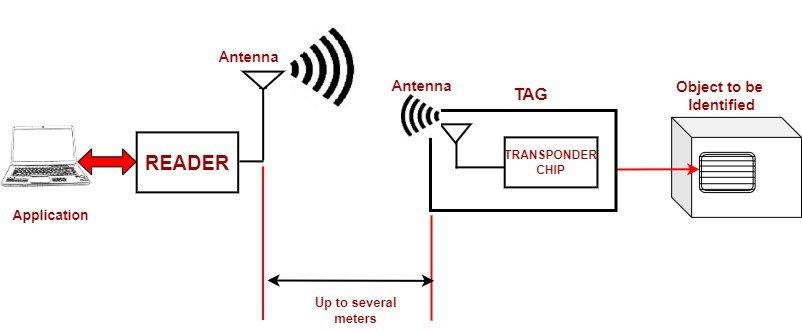
The far-field RFID has a broader range of communication than the near-field, as such, we use it for a wide variety of applications such as access controls, goods management, etc.
In this article, we’ll explore the capabilities and attributes of far-field RFID technology which we will be referring to as RFID in our ensuing discussion.
Now, let’s discuss the components of a typical RFID system
4. RFID System Component – the Tag
As stated earlier, RFID systems have three main components, namely, the tag, the reader, and the middleware.
In this section, we focus on the RFID tag.
RFID tags, called transponders or labels, are small electronic devices with a microchip and an antenna. We use them in RFID systems to uniquely identify and track objects or people wirelessly.
Because RFID tags can be used for automatic identification and data collection, we can use them to effectively manage stocks, trace the supply chain, control access, and for a variety of other applications across industries.
There are many classes of RFID tags, as shown in the RFID tag tree below:
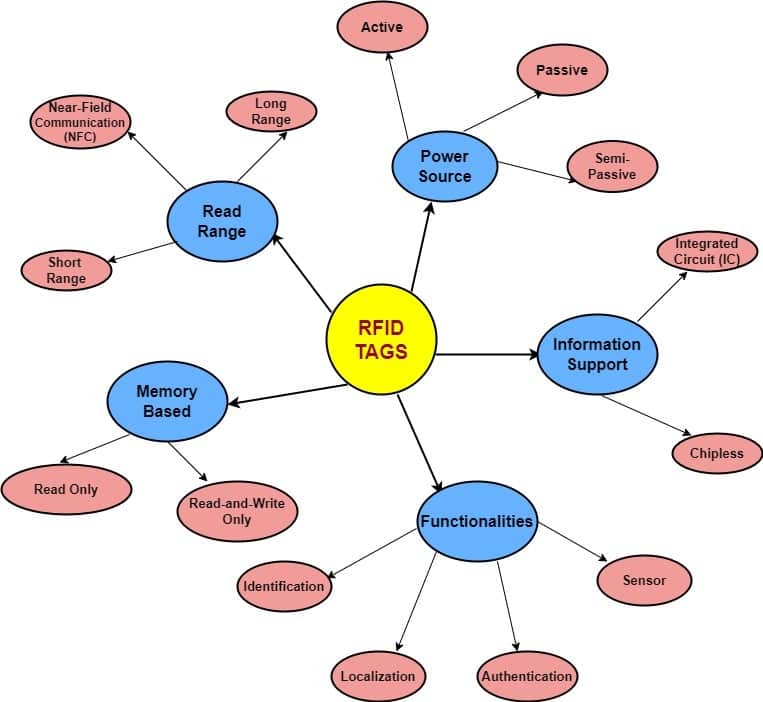
We will discuss two main classes of RFID tags, namely, tags based on power source and tags based on memory type.
Let’s describe each class.
4.1. Tags by Power Source
In this class, we have three types, namely, active tags, passive tags and semi-passive.
Active tags are so called because we provide separate power for them, thus giving them the autonomy to transmit signals independently. This inherent capability empowers us to seamlessly track and trace items across distances as far as 100 meters and more. This feature proves exceptionally advantageous for us when real-time monitoring takes precedence, like in the case of comprehensive inventory management systems.
Another huge benefit of the active tag is that we design them to have substantial memory space, which helps us meet the challenge posed in environments that demand the simultaneous reading of numerous tags.
However, it’s worth noting that these innovative advantages of the active tags come at a relatively higher cost compared to passive or semi-passive counterparts and necessitate periodic battery replacements to sustain their impressive performance.
In Passive tags, unlike active tags, we don’t supply power directly to passive tags. Instead, we design them to harness energy from the signals emitted by the reader itself to enable them to identify objects.
Passive tags are typically smaller, less expensive, and have a longer operational lifespan than active tags. We commonly use them in applications such as inventory management, asset tracking, supply chain logistics, and access control.
However, passive tags have a shorter read range than active tags and require closer proximity to the reader for successful communication.
Semi-passive tags, which we also call battery-assisted passive (BAP) tags, present a blend of features from both active and passive tags. In these tags, we integrate a power source, typically a battery, to power certain functions. However, unlike active tags, we don’t power the entire communication process with the battery.
This distinctive design allows us to strike a balance. We benefit from extended read ranges and faster response times, attributes akin to active tags, thanks to the supplementary power source. Meanwhile, the absence of full-scale battery-powered communication, similar to passive tags, ensures a cost-effective and efficient approach.
4.2. Tags by Memory Type
We divide the memory-based tags into two, namely, tags with read-and-write memory, and tags with read-only memory
The Read-and-Write memory tag enables us to not only retrieve information from the tag but also update and modify it. With this type of tag, we enjoy a bidirectional flow of data interaction. We can read the existing data stored within the tag, and at the same time, we can write new data onto it.
This versatile functionality allows us to adapt and refine information as needed, offering a dynamic approach to data management. Whether adjusting details in our inventory records or fine-tuning identification data, the Read-and-Write memory tag facilitates a seamless and interactive process. This tag proves invaluable in scenarios where data accuracy, real-time updates, and adaptable information storage are pivotal considerations.
The Read-only memory tag provides a one-way data flow. With this type of tag, we can access information stored within it, but we’re unable to modify or update the data. This read-only nature ensures data integrity and security.
In practical terms, we benefit from a reliable and unalterable information retrieval source. Whether for authentication purposes, accessing reference data, or ensuring data consistency, the Read-only memory tag is crucial in scenarios where maintaining the original data state is paramount. This tag provides a secure and dependable means of accessing vital information while preventing inadvertent changes.
5. RFID System Component – the Reader
RFID readers serve as vital components in the RFID system. These devices play an active role in managing communication with RFID tags. When we initiate commands, the readers generate an RF carrier wave, which we continuously monitor for modulation indications. Detecting such modulation alerts us to the presence of RFID tags.
The readers transmit this carrier signal through antennas, delivering it to the tags. As the signal reaches the tags, it triggers a series of actions. Once the tag gathers sufficient energy, it adjusts the carrier signal and returns a modulated signal. This signal contains essential data, and our readers actively capture it. We then proceed to decode and process the data, extracting meaningful information.
The versatility of RFID readers makes them invaluable across diverse applications. Whether managing inventory, enhancing security, or optimizing tracking, these devices facilitate seamless interactions with RFID tags, ensuring efficient and reliable data exchange.
We commonly encounter two types of RFID readers:
5.1. Fixed RFID Readers
These are the stationary readers that we often see in place at specific locations. We utilize them when items or individuals pass through designated points where their tags must be read. These readers offer consistent and dependable performance, seamlessly integrating with our existing setups. They serve various purposes, including access control, inventory management, and automated data collection.
5.2. Mobile RFID Readers
When we require mobility and adaptability, we turn to handheld mobile readers. These portable devices allow us to carry them around as we move from one location to another. This flexibility is valuable during inventory audits, asset tracking, or field operations. With these handheld readers, we can swiftly and effortlessly read tags in different environments, eliminating the need for fixed installations.
Our choice between these two types of RFID readers hinges on the specific demands of the task.
6. RFID System Component- the Middleware
Middleware is a crucial component within our RFID system. It plays an active role in managing and optimizing the data flow between RFID readers and our backend systems. With middleware, we can efficiently handle the information gathered from RFID tags.
We use middleware to bridge the gap between the raw data readers collect and the meaningful insights we seek to extract. As data flows in, middleware steps in to filter, process, and organize it according to our requirements. This ensures that the data reaching our backend systems is accurate, relevant, and structured in a way that facilitates effective analysis.
In essence, middleware is the dynamic link that transforms raw RFID data into actionable intelligence. It empowers us to make informed decisions, optimize processes, and maximize the value of our RFID implementation.
7. How Does the RFID System Work?
In this section, we provide a high-level description of the sequential process of how RFID works.
- We, as the host, manage the reader(s) and issue commands, after which the reader and the tag communicate via a radio frequency signal.
- We keep the reader continuously generating an RF carrier sine wave, always watching for modulation to occur. When we detect modulation of the field, it indicates the presence of a tag.
- We send out the carrier signal through the antennas.
- The carrier signal hits the tag(s).
- Once the tag has received sufficient energy to operate correctly, it divides down the carrier and begins clocking its data to an output transistor, which is normally connected across the coil inputs.
- The tag receives and modifies the carrier signal and sends back a modulated signal. The tag’s output transistor shunts the coil, sequentially corresponding to the data being clocked out of the memory array. Inductive coupling and load modulation are used at lower frequencies (for near-field RFIDs), unlike systems operating at 2.45 GHz and higher bands, where we use true RF communication links and backscatter principles (for far-field RFIDs).
- Shunting the coil causes a momentary fluctuation (dampening) of the carrier wave, which we see as a slight change in the amplitude of the carrier.
- Antennas receive the modulated signal and send it to us.
- We decode the data. We peak-detect the amplitude-modulated data and process the resulting bit stream according to the encoding and data modulation methods.
- Finally, we return the results to the host application.
8. RFID Frequency Band Allocation
Let’s dive into how RFID frequency allocation works all around the world.
RFID technology relies on specific radio frequency (RF) bands for effective communication between RFID tags and readers. These frequency bands are allocated differently in various parts of the world, and this allocation is overseen by international organizations like the International Telecommunication Union (ITU) and local regulatory bodies.
We provide a breakdown of the key frequency bands used for RFID worldwide in Table 1:
| Frequency Band Description | RFID Frequency Band Range | RFID Distance Range | Common Application |
|---|---|---|---|
| Low Frequency (LF) | 125 – 134 kHz and 140 – 148 kHz | up to 1/2 meter | We commonly use this for -access control, -pet identification and -livestock tracking. -It’s great for short read range and minimal interference. |
| Medium Frequency (MF) | 6.765 – 6.795 kHz | not specified | We use this frequencies for near-field RFID . |
| High Frequency (HF) | 13.553 – 13.567 MHz (often called the 13.56MHz) | up to 1meter | We commonly encounter this in -contactless payments, -identification cards, -access control, and -garment tracking devices. |
| Ultra High Frequency (UHF) | 433 MHz | We use this frequency with -backscatter coupling, for applications such as -remote car keys in Europe |
|
| Ultra High Frequency (UHF) | 858 – 960 MHz | 1 to 10 metres | We cannot access these RFID frequencies globally because of the significant restrictions on their use. When they are used, we use it for -asset management, -container tracking, -baggage tracking, -work-in-progress tracking, -and often in conjunction with Wi-Fi systems. We provided more information on this frequency range on Table 2. |
| Super High Frequency (SHF) | 2.446 – 2.454 GHz | 3 metres upwards | We use these frequency ranges with -active tags for long-range tracking, -for AVI (Automatic Vehicle Identification). We use backscatter coupling for communication |
The exact frequency allocations within these bands might vary slightly from country to country, and regulations can also differ. Various regions might earmark particular frequency bands for specific applications, while others might grant more flexibility.
8.1. The 860 – 960 MHz UHF RFID Frequencies
The 860 – 960 MHz is a portion of the UHF RFID frequencies that has restrictions for its use worldwide. It is important we point out these restrictions as they relate to different regions across the world. In Table 2, we show how this specific frequency is used worldwide:
| Country | Comments |
|---|---|
| North America | Here the UHF RFID band can be used unlicensed within the limits of 915 MHz ± 15MHz (i.e. 902 – 928 MHz). There are restrictions on transmission power. |
| Europe (with less exclusions) | In many part of Europe, the RFID frequencies specifies ETSI standardizations such as EN 300 220, EN 302 208, and ERO recommendation 70 03. These allow RFID operation within the band 865-868 MHz, but with some involved restrictions. |
| France | The North American standard is not used within France as it interferes with frequencies allocated to the military. |
| China and Japan | License free RFID bands or frequencies are not available However you can request a license for UHF RFID which is granted in a site basis. |
| Australia and New Zealand | In this region, the RFID band exists between 918-926 MHz. These frequencies are unlicensed. However, there are restrictions on the transmission power. |
In general, for the seamless operation of RFID technology and to prevent interference with other communication systems, adherence to these frequency allocations is critical. So, for effective use of RFID, we must stay well-versed in local regulations and frequency allocations to ensure our RFID systems operate smoothly, efficiently, and without disruptions.
9. Conclusion
In conclusion, we have seen that RFID technology stands as a transformative force within the realm of automatic identification. In this article, we have explored its principles, components, and global frequency allocation. International and local standardization bodies provide standards and recommendations to facilitate and fastrack its smooth use in every sector of the world economy.
It has become evident that RFID’s pervasive impact shapes modern processes, enhancing accuracy, transparency, and operational effectiveness across diverse sectors.