1. Introduction
In this tutorial, we’ll explore the fundamental concept of encryption, emphasizing its pivotal role in securing digital communication. Our main focus will be on the digital signature algorithm, which plays a significant role in this process.
2. Understanding Asymmetric Encryption
2.1. What Is Encryption?
Encryption generally safeguards information by transforming it into a secure code, preventing unauthorized access. It is a crucial defense in protecting sensitive data during digital communication and transactions.
2.2. Asymmetric Encryption Basics
Public-key cryptography, alternatively referred to as asymmetric encryption, stands as a pivotal principle within the realm of cybersecurity. In contrast to symmetric encryption, where a single key serves for both encryption and decryption, asymmetric encryption utilizes a dual-key system: a public key, openly available to everyone, and a private key, safeguarded exclusively by the key owner.
To illustrate, imagine Alex wants to send a confidential message to Joe. Joe shares his public key with Alice. Using Bob’s public key, Alice encrypts the message before sending it. Upon receiving the encrypted message, Joe uses his private key to decrypt and access the original content.
This two-key system secures communication by preventing the decryption of the message using the intercepted public key without the corresponding private key. Asymmetric encryption, which underlies secure communication channels, finds extensive use in digital signatures, secure email communication, and online transactions.
3. Digital Signatures
A cryptographic technique, the digital signature, verifies the authenticity and integrity of digital messages, documents, or software.
It acts as a digital counterpart to a handwritten signature or stamped seal, guaranteeing the sender’s claimed identity and preserving the message’s unaltered state throughout transmission.
3.1. Key Pair and Signing Process
Digital signatures rely on a key pair system consisting of a private key, securely held by the signer, and a corresponding public key, openly shared.
Furthermore, the signing process involves using the private key to generate a unique digital fingerprint through complex mathematical algorithms.
3.2. Verification Process and Data Integrity
Recipients use the sender’s public key to verify the signature’s authenticity, confirming the document’s integrity by ensuring it hasn’t changed since the signature was applied.
The significance of digital signatures lies in their crucial role in upholding data integrity. Even slight modifications lead to an entirely distinct signature upon re-signing with the private key.
3.3. Authentication and Non-repudiation
Digital signatures provide robust authentication, linking the public key to the signer’s identity through the private key. Additionally, non-repudiation ensures accountability, preventing signers from denying their involvement in creating the digital signature.
3.4. Applications and Standards
In secure email communication, document authentication, e-commerce transactions, and legal contracts, digital signatures establish trust in electronic communication. Various cryptographic algorithms, such as RSA, DSA, and ECDSA, are used, with the choice based on factors like security requirements and performance considerations.
4. What Is a Digital Signature Algorithm?
DSA is a prevalent method in cryptography for confirming the authenticity and integrity of digital messages or documents. Picture it as a virtual imprimatur. By employing DSA, we not only assert our identity as the sender but also fortify the transmitted message, shielding it against any potential tampering as it traverses the complex pathways of the digital domain.
Digital signatures are essential in electronic communication and transactions as they enable parties to trust the origin and content of the information exchanged. DSA is widely employed for ensuring the security of digital communications and validating the identity of participants in online transactions.
4.1. How DSA Works?
DSA functions using the principles of public-key cryptography, utilizing a pair of cryptographic keys. The private key is held securely by the signer, while the public key is made available to others. The process begins with the creation of a unique digital signature for a specific message using the signer’s private key. This signature is then attached to the message:
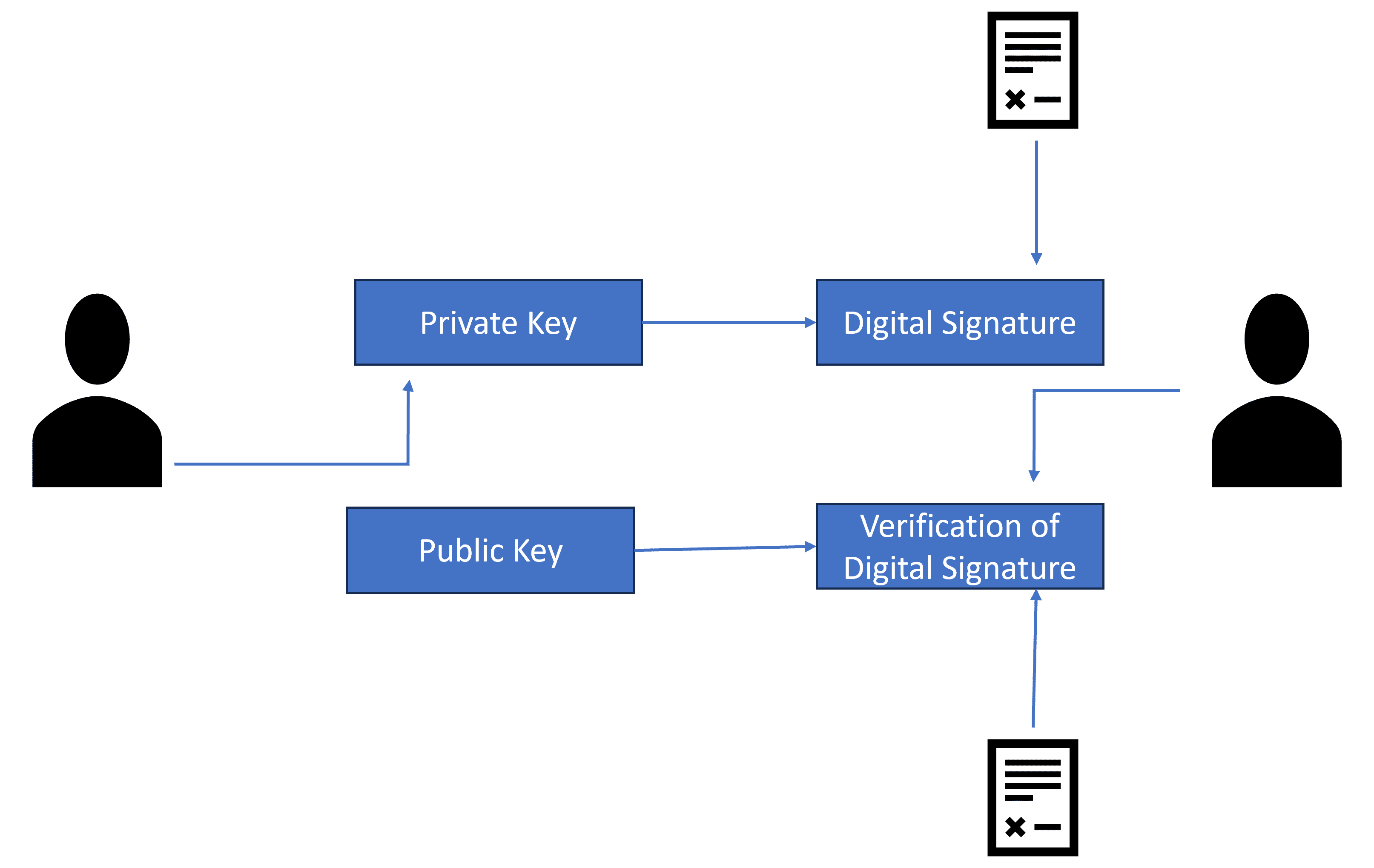
To verify the signature, the recipient can use the public key associated with the sender to authenticate the message. If the signature is valid, it confirms both the message’s origin and its integrity.
5. Navigating DSA Steps
Navigating the Digital Signature Algorithm (DSA) involves several key steps to ensure the secure exchange of digital messages. These steps include key generation, signature generation, and signature verification.
Understanding each step is crucial for implementing DSA effectively and maintaining the integrity and authenticity of digital communications.
5.1. Key Generation
In the initial stage of the DSA process, key generation takes precedence. This entails creating a private key and its corresponding public key. The entity generating the keys maintains confidentiality of the private key, whereas the public key is openly shared.
The strength of DSA lies in the complexity of these keys and their unique relationship, forming the foundation for secure digital signatures.
5.2. Signature Generation
After generating the key pair, the subsequent step involves signature generation. When a sender endeavors to authenticate a message, they engage their private key in a precise mathematical operation upon the message. This systematic process yields a distinct digital signature, scientifically ensuring both the sender’s identity and the unaltered nature of the transmitted message:
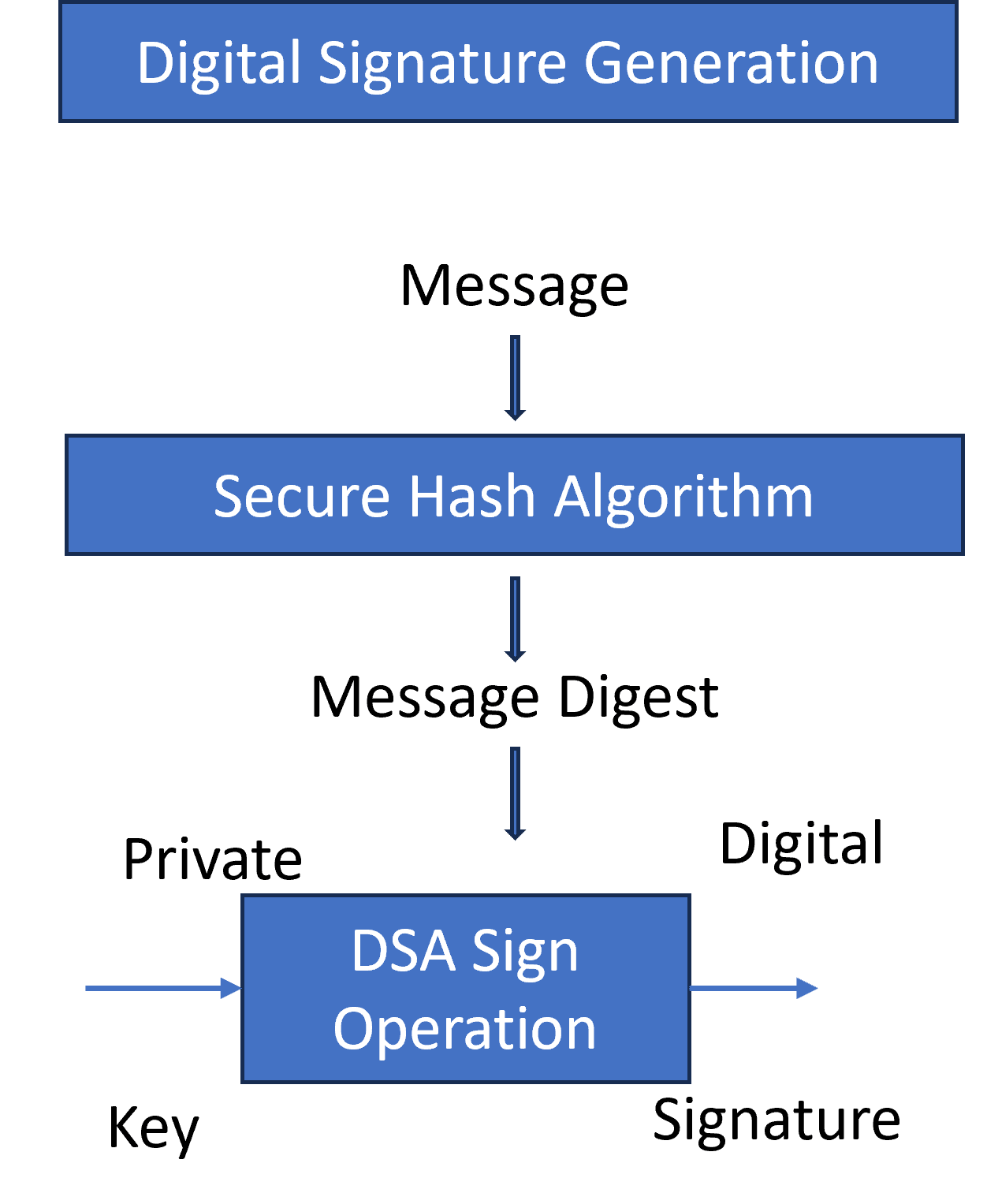
This signature is then attached to the message before transmission. The complexity of the DSA algorithm ensures that even a slight change in the message would result in a completely different signature.
5.3. Signature Verification
On the recipient’s end, the third step is signature verification. The recipient can apply a mathematical process to the received message and the attached signature using the sender’s public key. If the result matches the original signature, it confirms the authenticity and integrity of the message.
The verification step holds crucial importance in ensuring that the message remains unaltered during transmission and genuinely originates from the asserted sender.
Understanding and successfully navigating through these DSA steps are essential for establishing trust in digital communication and maintaining the security of online transactions.
6. Advantages of DSA
The Digital Signature Algorithm (DSA) brings significant advantages to the field of digital security, playing a crucial role in guaranteeing the integrity and authenticity of digital communications:
| Advantage | Description |
|---|---|
| Enhanced Security | DSA provides a robust mechanism for securing digital transactions and safeguarding data from unauthorized access and tampering. |
| Non-Repudiation | DSA ensures non-repudiation, meaning parties involved cannot deny their involvement in a transaction or the authenticity of their digital signature. |
| Efficiency and Simplicity | Implementing DSA is efficient and straightforward, offering a streamlined approach to cryptographic processes compared to other methods. |
Organizations and individuals can benefit from heightened security, indisputable accountability, and a user-friendly cryptographic solution by leveraging the Digital Signature Algorithm’s strengths.
7. Conclusion
In this article, we examined the Digital Signature Algorithm (DSA), highlighting its components and steps in ensuring secure digital communication. Additionally, we explored signature generation, where the private key produces a unique digital signature attached to the message, ensuring its authenticity. The subsequent step involves signature verification, using the sender’s public key to confirm both message integrity and origin.
DSA plays a crucial role in securing digital communication by offering a robust framework against tampering. Its foundation in intricate mathematical processes and the interplay between private and public keys establishes trust in online transactions. The implementation of DSA actively contributes to fostering a secure digital environment.