1. Overview
In this tutorial, we’ll discuss the rail fence cryptography technique with an example.
Finally, we’ll present the core advantages and disadvantages of this technique.
2. Rail Fence Technique
The rail fence technique is a simple form of transposition cipher. It’s a type of cryptographic algorithm that rearranges the positions of the letters in a message to create a new, seemingly unrelated message. The technique gets its name from the way we write the message. Applying the rail fence technique in a given text results in a zigzag pattern, with each letter in a row written out before moving to the next row.
To encrypt a message using the rail fence technique, first, we need to write the message in the first row of a table. Furthermore, we have to write the second letter of the message in the second row. We need to continue this process until we’ve written all the letters in the message. Finally, in order to generate the encrypted message, we read the table row-wise.
Now let’s talk about how we can decrypt a message. To decrypt an encrypted message, the first step is to determine the number of rows in the table based on the length of the encrypted message. Furthermore, we need to write the first letter of the encrypted message in the first row, the second letter in the second row, and so on. We need to continue this process until we’ve written all the letters in the message.
Overall, the rail fence technique is a relatively simple form of encryption. However, it doesn’t provide strong security. Someone can easily break it with even a basic understanding of cryptography. Although, it can still be helpful for simple communication where a high level of security is not required.
3. Example
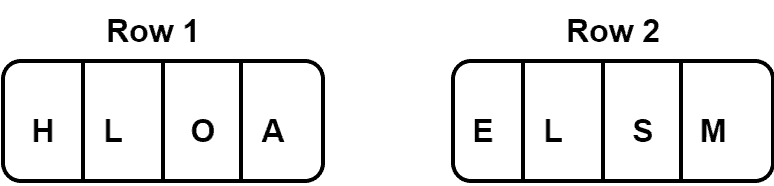
First, let’s look at an example of the encryption of a message using the rail fence technique. Here, we want to encrypt a message with two rows: HELLO SAM. First, we would write the message in rows:
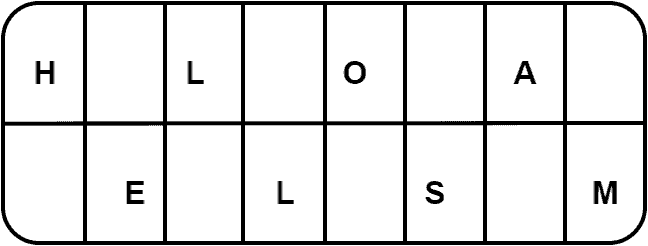
Now, in order to generate encrypted text, we need to write the first row, followed by the second row. Hence, our encrypted message is HLOAELSM.
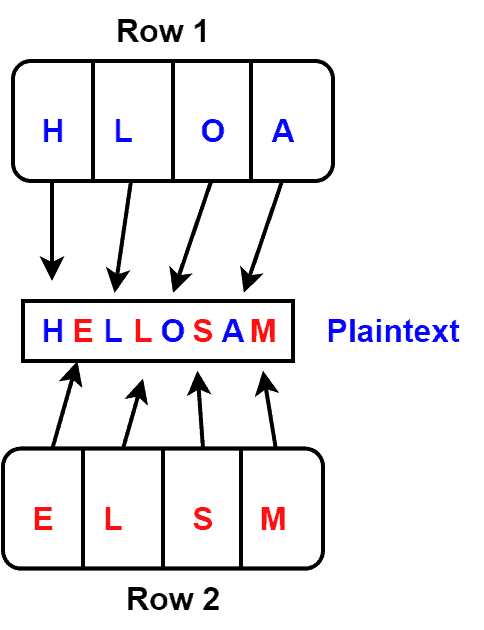
Now let’s start the decryption process. First, we must determine the number of rows needed to decrypt the message. We already know the number of rows is two here. The total length of the encrypted message is 8. Hence, each row will contain four letters:
The first letter of the plaintext would be the first letter of the first row of the table. Similarly, the second letter of the plaintext would be the first letter of the second row of the table. We need to continue this process until we cover all the letters in the encrypted message:
Therefore, we get our plaintext after applying the decryption process: HELLO SAM.
4. Advantages and Disadvantages
Now we know the basic idea behind the rail fence technique. Let’s talk about the advantages and disadvantages.
Some advantages of the rail fence technique include simplicity, ease of use, and flexibility.
The rail fence technique is relatively simple to understand and implement, making it a good choice for basic communication where a higher level of security is not required. We can manually perform the rail fence technique without requiring specialized equipment or software.
Finally, we can use the rail fence technique with any number of rows. It allows the user to choose a level of complexity appropriate to their needs.
The main disadvantages of this technique are lack of security, limited effectiveness, and vulnerability to attacks.
The rail fence technique is not a secure form of encryption, as someone can easily break it with even a basic understanding of cryptography. Additionally, this technique is not highly effective for longer messages.
Furthermore, the rail fence technique is vulnerable to certain types of attacks, such as known-plaintext attacks. Therefore, an attacker can easily break the encryption by launching attacks.
5. Complexity and Applications
The complexity of the rail fence technique depends on the number of rows used to write out the message. The more rows we use, the more complex the encryption will be. Additionally, increasing the number of rows can make it hard for an attacker to determine the original positions of the letters in the message.
However, even with many rows, the rail fence technique is still not a very secure form of encryption. It’s always vulnerable to certain types of attacks, and attackers can break them easily.
The rail fence technique is not commonly used in modern communication. It was part of some simple, low-security communication protocols. Although, there’re more secure options available today that are better suited for protecting sensitive information.
One possible application of the rail fence technique might be for use in children’s educational games or activities. We can use it as a simple and fun way to introduce the basic concepts of cryptography. However, it should not be relied upon for any serious security applications.
6. Conclusion
In this tutorial, we discussed the rail fence cryptography technique with an example. Finally, we presented the core advantages and disadvantages of this technique.