Learn through the super-clean Baeldung Pro experience:
>> Membership and Baeldung Pro.
No ads, dark-mode and 6 months free of IntelliJ Idea Ultimate to start with.
Last updated: March 18, 2024
In today’s digital environment, protecting the data we send online is critical. To achieve this, we use various protocols, including Transport Layer Security (TLS). Digital certificates play an important role in maintaining the confidentiality of information and authenticating the source of received data. Trusted Certificate Authorities (CA) sign these digital certificates, and these, in turn, are signed by root certificates. Root certificates are self-signed certificates but are trusted globally. Our operating systems and browsers keep a list of these root certificates for verification purposes.
Despite having robust communication protocols and using digital certificates, complete security remains elusive due to existing vulnerabilities. One of these vulnerabilities might enable attackers to create a fraudulent Certificate Authority (CA). This is why certificate pinning is essential. In this article, we’ll look at the concept of certificate pinning, its significance, how it’s implemented, and the impact it has on application security, as well as its drawbacks.
Certificate pinning is an important security practice, particularly prevalent in mobile applications. It aims to enhance the security of Secure Socket Layer (SSL) and Transport Layer Security (TLS) communications. We can pin certificates by associating a host with an X.509 certificate. The primary objective of certificate pinning is to mitigate the risk of man-in-the-middle attacks, where an attacker can intercept and manipulate communication between a client and a server.
Despite the widespread belief that SSL/TLS encryption protects network traffic from unauthorized access, several vulnerabilities exist within these protocols, such as BEAST, POODLE, and Heartbleed. These vulnerabilities could potentially expose encrypted data to unauthorized access.
To address these risks, certificate pinning adopts a proactive approach by binding a certificate to a host and validating it through a trusted Root Certificate Authority (CA). While relying solely on a certificate might seem secure, but there’s a potential vulnerability; an attacker with sufficient knowledge can manipulate a host to use counterfeit certificates by impersonating a trusted Root CA.
In the figure below, a client initiates communication with the server and requests the server’s certificate. However, an adversary eavesdrops between the client and server to manipulate the transmitted certificate sent by the server. Subsequently, the adversary forwards this fraudulent certificate to the client. The client unwittingly accepts the fraudulent CA and authenticates the attacker:
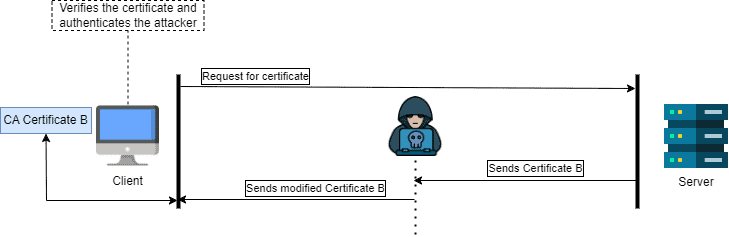
In essence, certificate pinning acts as a robust method, ensuring the integrity and authenticity of the communication channel by preventing the use of fraudulent or malicious certificates.
Certificate pinning is a process where a specific certificate is linked to a service or application. Instead of trusting any valid certificate, the application “pins” a specific certificate or public key, allowing it to recognize and trust only that one. In simpler terms, certificate pinning is like giving a specific identity card to a particular application server. There are two main ways to implement certificate pinning: static and dynamic.
First, let’s think of static pinning as giving a permanent ID card to the server. The server’s public key or its certificate is directly embedded into the application’s code or configuration. This means the application is set to trust only a specific set of certificates associated with a particular domain. Thus, if the certificate presented during a connection doesn’t match the pinned one, the application considers the connection untrusted and may terminate it.
While this method enhances security, it has some drawbacks. For example, if we need to update the pinned certificates, we’ll need to release a new version of the application, which can be a hassle. Also, if the pinned certificate needs to be revoked or replaced, all users will need a software update.
Second, let’s think of dynamic pinning as giving a temporary ID card to the server. It is also known as certificate pinning with HTTP Public Key Pinning Extension (HPKP). Here, the server tells the client which public keys to expect in the future. The server includes an HTTP header in its response, indicating the public keys or fingerprints of the certificates that the client should accept for future connections.
Dynamic pinning overcomes some of the limitations of static pinning. It offers more flexibility as administrators can update pinned certificates without needing a new software release. However, dynamic pinning has its own challenges, such as the risk of misconfigurations that could lead to potential service disruptions.
The certificates that can be pinned include the leaf, intermediate, and root certificates. However, the choice of which certificate to pin depends on the application’s specific security needs and maintenance capabilities.
The leaf certificate is the end certificate at the bottom of the hierarchy. It represents a specific domain or entity. Pinning the leaf certificate minimizes the attack surface, but it requires regular updates as these certificates change frequently.
The intermediate certificate is a bridge between the root certificate and the leaf certificate. If we pin the intermediate certificate, then it offers a balance between security and maintenance. It has a larger attack surface compared to the leaf certificate, but it doesn’t require updates as often because it doesn’t change regularly.
Unlike the leaf and intermediate certificates, the root certificate stands at the pinnacle of the hierarchy. It’s a self-signed entity. Pinning the root certificate presents the largest attack surface, but it requires the least frequent updates.
Implementing certificate pinning offers several security benefits for applications:
Firstly, certificate pinning adds an extra layer of defense against the compromise of CAs. Even if a malicious actor manages to use a fraudulent certificate trusted by the root CA, the application will reject it if it doesn’t match the pinned certificates.
Secondly, certificate pinning helps protect against MitM attacks, where an attacker intercepts and potentially alters communication between the user and the server. It ensures that only specific certificates are trusted, therefore it restricts attackers from eavesdropping.
Thirdly, by reducing reliance on external Certificate Authorities and explicitly specifying trusted certificates, applications employing certificate pinning achieve a more robust and controlled security posture.
Lastly, certificate pinning allows developers to use self-signed certificates, which reduces the costs associated with purchasing certificates from third parties.
While certificate pinning enhances security, its implementation comes with certain challenges that need to be carefully addressed:
Protecting private keys and managing public keys’ lifecycle needs careful planning and following best practices. If a private key is compromised, it puts the confidentiality and integrity of a cryptographic system at risk. Likewise, insecure distribution of public keys can enable attackers to perform man-in-the-middle attacks by posing as legitimate key holders.
Misconfigurations or errors in updating pinned certificates can lead to pinning violations. Subsequently, it has the potential to cause service disruptions for users. In order to minimize such risk, it’s essential to have proper testing and monitoring mechanisms. For instance, if a banking app expects a specific certificate but encounters a different certificate due to misconfiguration, users might face service disruptions.
Moreover, the need to update pinned certificates may necessitate the release of new app versions. This can impact operational flexibility, especially in scenarios where frequent updates are impractical for the organization.
When a mobile application has enabled certificate pinning, conducting a security assessment becomes quite challenging. This is because certificate pinning prevents the interception of the application’s traffic. To overcome this, the security analyst either has to unpin the certificate or seek assistance from the developer to disable the certificate pinning in the test environment. This introduces an extra layer of complexity in the testing process.
Certificate pinning stands as an important method in application security, providing a proactive approach to mitigate risks associated with compromised Certificate Authorities (CAs) and potential Man-in-the-Middle (MitM) attacks. As the landscape of cyber threats continues to evolve, securing the communication channel between users and servers becomes increasingly important.
In this article, we delved into the concept of certificate pinning, its necessity, its workings, what should be pinned, its benefits, and the challenges that arise post-implementation. In order to ensure our digital interactions remain safe from unauthorized access and manipulation, such security measures become essential. All in all, certificate pinning is one of several effective security practices that contribute to this goal.