Yes, we're now running our Black Friday Sale. All Access and Pro are 33% off until 2nd December, 2025:
Understanding DevSecOps
Last updated: February 6, 2024
1. Introduction
In this tutorial, we are going to discuss DevSecOps, its advantages, and how it’s different from DevOps.
The term “DevSecOps” is being used more frequently in the software industry as a result of the current rise in cybersecurity worries.
2. The Need for DevSecOps
DevSecOps is an acronym for development, security, and operations.
As an extension of the DevOps model for software development, it applies security measures throughout the software development life cycle (SDLC). According to DevSecOps, everyone participating in the development process needs to be aware of how important security is.
So, DevSecOps is a paradigm enhancing communication between the security/Cloud Security, development, and operations teams to increase the security of software:
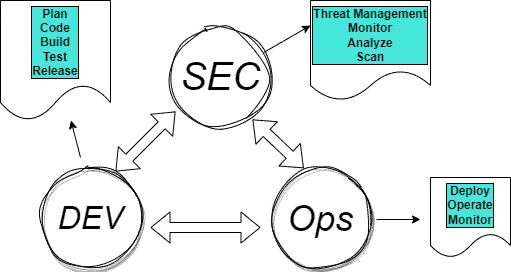
2.1. Challenges of Traditional Security Approaches
Before the emergence of DevSecOps, traditional security approaches faced several challenges that limited their effectiveness in securing software development and deployment. Some of these challenges are:
- Siloed Teams: In traditional approaches, security teams often worked in isolation from development and operations teams. This siloed structure led to limited communication, collaboration, and shared responsibility for security. As a result, security measures were typically implemented as an afterthought, leading to delayed detection and resolution of vulnerabilities
- Slow Security Processes: Earlier security processes were often time-consuming and manual, leading to bottlenecks in the development and deployment pipeline. Typically, we conducted security assessments, penetration testing, and compliance checks at the end of the development lifecycle, which caused delays and hindered our ability to respond quickly to emerging threats
- Lack of Continuous Monitoring: Traditional security approaches focused primarily on perimeter defense, relying on firewalls and intrusion detection systems to protect applications. However, this reactive approach left applications vulnerable to emerging threats. Continuous monitoring of applications and infrastructure for security vulnerabilities and potential breaches was often lacking
2.2. Benefits of Integrating Security Into the Development Process
By incorporating security into the development process, DevSecOps makes sure that security is not an afterthought but rather an essential part of the software development lifecycle.
It offers a variety of benefits, such as the early detection of security problems, reduced expenses, continuous security, greater collaboration, expedited time to market, compliance adherence, risk reduction, and increased customer and trustworthiness.
3. How to Implement DevSecOps?
Implementing DevSecOps has various advantages, including increased security, lower costs, and quicker turnaround times. However, putting DevSecOps into practice can be difficult, especially for businesses that are unfamiliar with the idea:
- Include security teams in the design process: By doing this, we ensure that we consider hazards right away. Therefore, security flaws will be less likely later on in the development process
- Train Developers to Write Secure Code: Preventing a vulnerability in the first place is the best method to deal with it. Teaching developers to write secure code can help to eliminate a lot of vulnerabilities, cut the price of new improvements, and speed up deployment
- Automate Security Processes: We leverage automation tools and technologies to streamline security processes. Automated vulnerability scanning, code analysis, and security testing enable faster identification and remediation of vulnerabilities, reducing the time between detection and resolution
- Integrate Security Testing: DevSecOps implements comprehensive security testing throughout the SDLC. This includes static application security testing (SAST), dynamic application security testing (DAST), software composition analysis (SCA), and penetration testing. Automate these tests as part of the CI/CD pipeline to identify and remediate vulnerabilities early in the development process:
4. Key Practices in DevSecOps
By putting these key practices into execution, organizations can build a reliable and secure DevSecOps methodology that integrates security into every stage of the software development lifecycle. This helps firms create and deliver safe software solutions quickly and nimbly.
4.1. Threat Modeling
Threat modeling involves identifying and evaluating potential threats and vulnerabilities in an application or system. Typically, in DevSecOps, we perform it early in the development process. It helps in understanding the application’s architecture, components, and potential attack vectors:
- Identify Assets: We need to identify the valuable assets that need protection, such as sensitive data, user credentials, or critical infrastructure components
- Identify Threats: This refers to the detection of potential threats that could exploit application or system weaknesses. Those are threats from the inside as well as the outside, like hacker assaults and privilege escalation
- Assess Vulnerabilities: We also should detect potential vulnerabilities within the application or system. This includes security weaknesses in the code, misconfigurations, or insecure integrations
- Prioritize and Mitigate: We categorize the identified threats and vulnerabilities based on their impact and likelihood. DevSecOps teams can then implement appropriate security controls, such as secure coding practices, input validation, access controls, or encryption, to mitigate the identified risks
4.2. Risk Assessment
Risk assessment helps prioritize risks and allocate resources effectively for risk mitigation efforts. In DevSecOps, we should regularly perform a risk assessment as an ongoing process throughout the software development lifecycle:
- Identify Risks: Based on the results of threat modeling and other security assessments, we identify specific risks and their potential impact on the application or system. This may include risks related to data breaches, unauthorized access, denial of service, or compliance violations
- Assess Likelihood: We consider factors such as the vulnerability’s exposure, the sophistication of potential attackers, historical data on similar attacks, and the effectiveness of existing security controls to estimate the probability of each security-breach event
- Assess Impact: Then, we evaluate the potential impact of each risk if it were to occur. This includes assessing potential financial losses, reputational damage, regulatory penalties, or harm to users or systems
- Prioritize and Mitigate: DevSecOps teams should focus on addressing high-priority risks first and implement appropriate risk mitigation measures, such as applying security patches, setting up access controls, or enhancing monitoring and detection capabilities
4.3. Security Code Review and Static Analysis
Security code review is a critical practice in DevSecOps that involves systematically analyzing the source code of an application to identify security vulnerabilities and weaknesses. It aims to detect and remediate security issues early in the software development lifecycle.
Static code analysis (SCA) automatically scans the source code without executing it. We examine the code structure, data flows, and dependencies to identify potential security issues.
SCA provides immediate feedback to developers regarding identified security vulnerabilities, coding errors, or potential performance issues. This enables developers to address issues early in the development process.
We can integrate SCA tools into the CI/CD pipeline to automatically scan the code during the build or commit phase. This allows for continuous monitoring of code quality and security.
4.4. Container Security and Orchestration
Container security and orchestration play crucial roles in the DevSecOps methodology. Containers provide a lightweight and portable solution for packaging software applications and their dependencies. However, they introduce unique security challenges. Here are some key considerations for container security.
- Image Security: we should ensure that we build container images from trusted sources and ensure they are free from vulnerabilities. We also need to regularly scan images for known vulnerabilities using tools like Clair, Anchore, or Trivy
- Image Hardening: this means applying best practices when building container images, such as minimizing the attack surface by removing unnecessary packages, using minimal base images, and following security guidelines specific to the container runtime
5. DevSecOps Challenges
While DevSecOps brings significant benefits to the software development process, it’s important to acknowledge its limitations and potential challenges:
- Implementation Complexity: Adopting DevSecOps practices requires significant planning, coordination, and investment in terms of time, resources, and infrastructure. Organizations must overcome the challenges of integrating security practices seamlessly into existing development and operations processes
- Skillset and Knowledge Gap: Building and maintaining a skilled DevSecOps team can be challenging. Organizations need professionals versed in development, security, and operations. So, they may require training or hiring individuals with expertise in both security and DevOps practices
- Legacy Systems and Technical Debt: Organizations with legacy systems or applications may face challenges in implementing DevSecOps practices. These systems often lack the necessary architectural flexibility and modern tooling required for the seamless integration of security practices
- Compliance and Regulatory Challenges: Meeting compliance requirements and navigating regulatory frameworks can be complex in a DevSecOps environment. Organizations must ensure that security practices align with relevant regulations, industry standards, and data protection laws
- Tooling and Automation Limitations: While automation is a key aspect of DevSecOps, it may have limitations. The availability and compatibility of security tools, integration with existing systems, and the complexity of automation workflows can pose challenges
6. DevSecOps Tools and Technologies
A variety of technological tools are available for organizations to use in their DevSecOps initiatives. Without hindering output, these methods aid in reducing risk in software development pipelines. Here are some popular tools and technologies used in DevSecOps:
Static Application Security Testing (SAST) Tools:
- SonarQube
- Veracode
- Checkmarx
- Fortify
Dynamic Application Security Testing (DAST) Tools:
- OWASP ZAP
- Burp Suite
- Acunetix
- WebInspect
Infrastructure as Code (IaC) Security Tools:
- Terraform
- AWS Config
- CloudFormation Guard
- kube-score (for Kubernetes configurations)
7. Conclusion
In this article, we learned about DevSecOps. Organizations can improve communication and cooperation between their security and development teams with the aid of DevSecOps.
With security acting as a cross-functional concern, DevSecOps combines distinct functions of development and operations and can assist in maintaining the security of an organization’s data in light of the rising frequency of data breaches.