Learn through the super-clean Baeldung Pro experience:
>> Membership and Baeldung Pro.
No ads, dark-mode and 6 months free of IntelliJ Idea Ultimate to start with.
Last updated: July 31, 2024
Data transfer is a common task for anyone using a computer. During data transmission, we should be very cautious and ensure that we maintain data confidentiality and integrity. For data transfer, we have various tools and technologies that we can use.
For example, FTP used to be the standard means of transferring data and files between computers for a long time. With FTP, we could transfer and store files without encryption and in clear text, including the passwords. Unfortunately, this proved to be a colossal disaster, as cybercriminals would intercept and access data during transmission. As a result, better alternatives were developed to meet this and other shortcomings of FTP.
In this article, we’ll discuss the SFTP, SCP, and FISH protocols. We will also look at the differences these protocols have.
SFTP is a secure file transfer protocol that runs over the SSH protocol. It allows a user to access and transfer data over the internet securely. We can also refer to SFTP as the Secure File Transfer Protocol. It provides a secure file transfer service and implements some features offered by the Linux filesystem, such as creating files, listing files, and traversing directories. SFTP is a client-server protocol that we can launch either through a command line or by using a graphical interface.
SFTP does not support authentication. Instead, it relies on the underlying secure transport to authenticate users. During authentication, the protocol requires the communicating parties to authenticate themselves either through a user id and password or by validating the SSH key. To establish a session, we can run:
$ sftp username@your_server_ip_or_remote_hostname
$ sftp -oPort=custom_port username@your_server_ip_or_remote_hostnameSome of the benefits of SFTP are:
Note that the acronym “SFTP” might mislead us into thinking that it’s simply FTP over SSH, but it is not. These are two different protocols.
Secure Copy Protocol (SCP) is a protocol that ensures the secure transfer of data between a local host and a remote host or between two remote hosts. It’s based on the Berkeley Software Distribution (BSD) Remote Copy Protocol (RCP), which runs on port 22 using the SSH protocol. Thus, we can say that SCP combines both RCP and SSH, as it uses secure RCP to transfer data and uses SSH for authentication and encryption.
Secure copy refers to either the SCP protocol or the SCP program. SCP’s command-line functionality is much faster compared to versions with a graphical interface.
Before starting a transfer, it first establishes a connection through the SSH. It then prompts us to enter the SSH login information or authorize the SSH key for public authentication:
$ scp [OPTION] [user@]SRC_HOST:]file1 [user@]DEST_HOST:]file2
$ scp file.txt remote_username@ip_address_of_remote:/remote/directoryOnce the session is active between the two hosts, the SCP client will begin a secure copy process with two different modes available:
Unlike SFTP, SCP is non-interactive and can only transfer files securely between a local and remote host. It lacks the Linux filesystem management features of SFTP and, when used, all options and parameters have to be specified explicitly in the command line. We can easily use it in batch files and scripts to automate file transfer.
Some of the advantages of using SCP are:
FISH is a network protocol that uses a secure shell (SSH) or remote shell (RSH) to transfer files and manage remote files. It allows us to manipulate files in a remote machine as if they were local.
We rarely used the FISH protocol, though it comes in handy when we run into situations where we don’t have both SCP and SFTP installed on the remote host. It only requires SSH or RSH implementation on the remote host, a Linux shell, and a set of standard Linux utilities that it uses for file management.
Alternatively, FISH has a special server program called fish_server that we can install on the server-side/remote host. When this program is available, it replaces the Linux shell and is primarily used to execute FISH commands received from the local host. This increases the speed of operation. The Midnight Commander software tool is designed to use the FISH protocol.
FISH commands are well-defined, and they have more priority than their Linux shell equivalents. The Linux shell equivalents of the same commands vary depending on the system. We expect the server to execute a FISH command if it understands it during execution. Otherwise, it will execute the equivalent Linux shell command provided. When there is no special server program, the Linux shell treats the FISH command as a comment and executes the equivalent shell command.
To get a glimpse of the FISH protocol, we need to install the Midnight Commander tool and then run it:
$ sudo apt-get install mc
$ mcWe don’t need root privilege to launch the program unless we want to perform functions that might need root permissions. When we run mc, it launches a text-based user interface with menus and panels.
To start a connection, we can click on either the menu labeled left or right. These both open a window that gives us three options that we can use to connect to the remote host. These options are FTP, SSH, and SFTP. If the connection is successful, it opens the file structure of the remote system. Then, we can proceed with file manipulation:
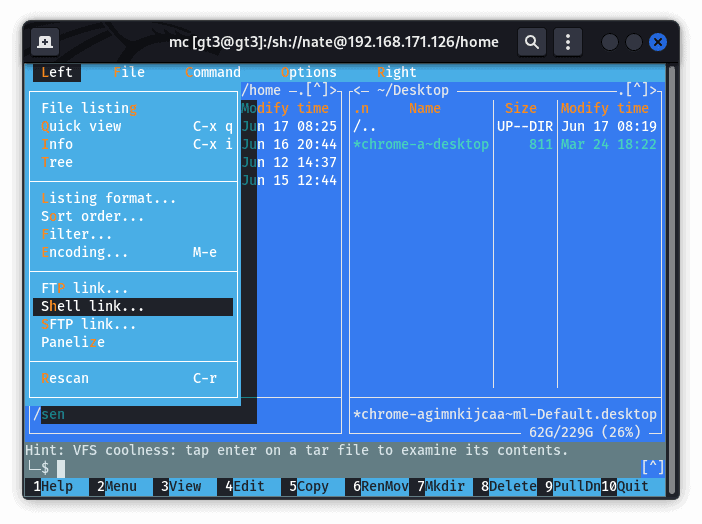
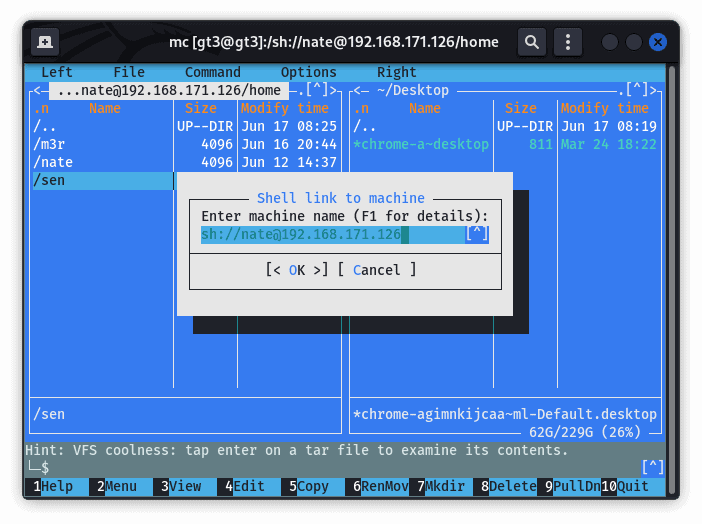
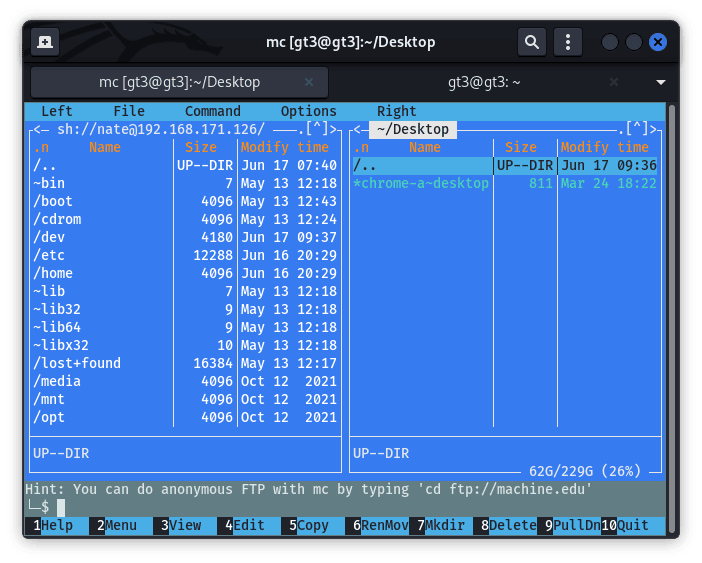
Some of the benefits are:
Let’s summarize the notable differences between these three protocols:
| SFTP | SCP | FISH |
|---|---|---|
| Has a graphical user interface (GUI) | Has a graphical user interface (GUI) | Has a text-based user interface (TUI) |
| Supports Linux file system features | Does not support Linux file system features | Supports Linux file system features |
| Both local and remote hosts require SFTP to be installed | Both local and remote hosts require SCP to be installed | Has to be installed in the local host. Can be installed in both local and remote to increase the speed of operation |
In this article, we’ve looked at SFTP, SCP, and FISH protocols. We mentioned some of the advantages of using each. In most instances, we’ll use SFTP, given that it has more advantages over the others. SFTP and SCP both have command line and graphical interface options, while FISH is a text-based user interface. Most graphical applications either use SFTP or SCP. Some have both options available.