Yes, we're now running our Black Friday Sale. All Access and Pro are 33% off until 2nd December, 2025:
ICMP Redirect Messages
Last updated: March 18, 2024
1. Overview
ICMP messages are very popular for diagnosing network connectivity problems. In addition to the common ICMP request and reply messages, there are some other ICMP out-of-band messages related to network operation. For example, ICMP redirect messages are among such control messages.
In this tutorial, we’ll discuss ICMP redirect messages and whether we should disable them.
2. Example Network
We have the following subnet 192.192.192.0/24:
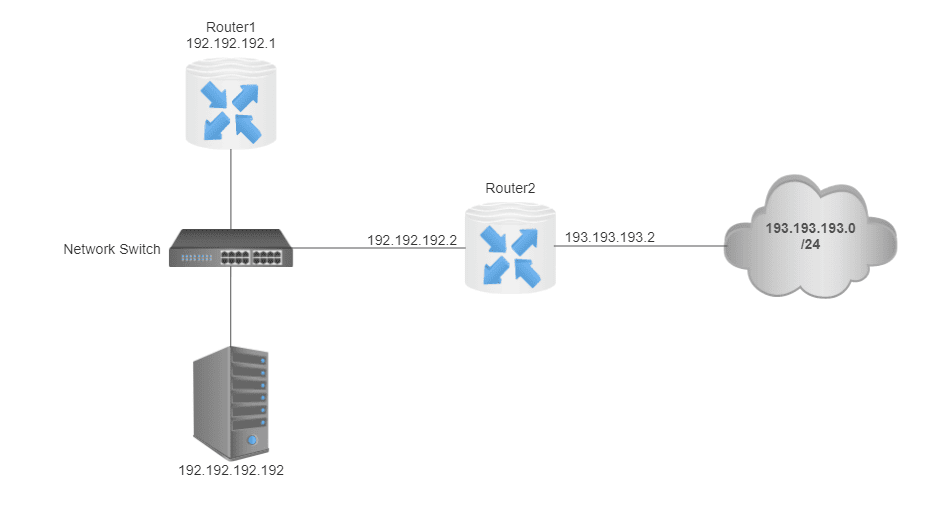
Our host has an IP address 192.192.192.192. There are two routers in the same subnet, Router1 and Router2. Their IP addresses are 192.192.192.1 and 192.192.192.2, respectively. Router1 is the default gateway for our host 192.192.192.192. However, Router1 has Router2 as the next hop to the network 193.193.193.0/24 in its configuration. The IP address of Router2 in the 193.193.193.0/24 subnet is 193.193.193.2.
3. ICMP Redirect Messages
In this section, we’ll discuss ICMP redirect messages and whether we should disable them.
3.1. What Are ICMP Redirect Messages?
ICMP redirect messages are for having more efficient routing of network packets.
Whenever our host sends a packet to a host in the 193.193.193.0/24 network, the packet is first sent to the default gateway, namely Router1. Since the destination address is in the 193.193.193.0/24 subnet, Router1 forwards the packet to Router2.
Instead of sending packets having a destination address in the 193.193.193.0/24 network to Router1, it would be better to send them directly to Router2. We can achieve it using ICMP redirect messages.
In this case, Router1 sends an ICMP redirect message to our host 192.192.192.192 informing that it’s better to send the packets destined for 193.193.193.0/24 subnet directly to Router2. Our host must satisfy a few conditions to send the packets directly to Router2.
We must configure the kernel in the host to accept ICMP redirect messages. This is the first condition. We can check the configuration using the sysctl command:
$ sysctl -a | grep accept_redirects
net.ipv4.conf.all.accept_redirects = 1
net.ipv4.conf.default.accept_redirects = 1
net.ipv4.conf.enp0s3.accept_redirects = 1
net.ipv4.conf.lo.accept_redirects = 1
net.ipv6.conf.all.accept_redirects = 1
net.ipv6.conf.default.accept_redirects = 1
net.ipv6.conf.enp0s3.accept_redirects = 1
net.ipv6.conf.lo.accept_redirects = 1Our host is enabled to accept ICMP redirect messages since the value of accept_redirects is equal to 1 for several kernel parameters, both for IPv4 and IPv6. enp0s3 and lo are the network interfaces of our host. lo corresponds to the loopback interface. We must set the values of these kernel parameters to 0 to disable ICMP redirection.
Additionally, the router to which the packets will be redirected must be in the same subnet. In our example, Router2 is in the same subnet as the host.
If the destination address is in the same subnet as the host, then ICMP redirection will also be ignored since there is no need for routing in this case.
3.2. Should We Disable ICMP Redirect Messages?
According to the discussion in the previous section, ICMP redirect messages have several advantages. For example, they may shorten the number of hops to the destination address. As a result of this, the traffic on the network and the CPU load of routers may become less.
However, enabling ICMP redirect messages may have a serious negative impact. They might be used for ICMP redirect attacks, which may let an attacker modify the routing tables of victim hosts. As a result of this, the victim host may direct the traffic to the attacker’s host thinking that the attacker’s host is a more suitable router for the destination address. Because of this reason, ICMP redirect messages are generally disabled by default from all public interfaces.
4. Conclusion
In this article, we discussed ICMP redirect messages. We learned enabling ICMP redirect messages has some advantages such as shortening the path to the destination address and lowering the CPU processing of routers. However, they may lead to ICMP redirect attacks. Therefore, we generally disable ICMP redirect messages from all public interfaces.