Learn through the super-clean Baeldung Pro experience:
>> Membership and Baeldung Pro.
No ads, dark-mode and 6 months free of IntelliJ Idea Ultimate to start with.
Last updated: June 4, 2025
In this tutorial, we’ll discuss the various ways to check firewall status in Linux.
There are diverse firewall options available at our disposal and we can choose any according to our needs. We’ll look at ufw, firewalld, and iptables and learn how to check their status.
ufw is the default firewall configuration tool for most Linux distros including Ubuntu. It runs on top of iptables and it’s easier to manage.
For the distributions that lack it, we can simply install it:
$ sudo apt install ufwufw provides a user-friendly way to create an IPv4/IPv6 host-based firewall. To check the status of ufw we run:
$ sudo ufw status
Status: inactiveIf it’s the first time we’re running our system, then it should show inactive. Otherwise, if we’ve enabled it before, it should display active:
$ sudo ufw status
Status: active
To Action From
-- ------ ----
Nginx Full ALLOW Anywhere
OpenSSH ALLOW Anywhere
For a more detailed output, we append the verbose option:
$ ufw status verbose
Status: active
Logging: on (low)
Default: deny (incoming), allow (outgoing), disabled (routed)
New profiles: skip
To Action From
-- ------ ----
80,443/tcp (Nginx Full) ALLOW IN Anywhere
22/tcp (OpenSSH) ALLOW IN AnywhereWe can also show a numbered list of the active rules when we use the numbered option:
$ ufw status numbered
Status: active
To Action From
-- ------ ----
[ 1] Nginx Full ALLOW IN Anywhere
[ 2] OpenSSH ALLOW IN Anywhere
Further, we can also filter out the state of active services using deny or allow. They both show the firewall’s active:
$ sudo ufw status | grep -i deny
23 DENY Anywhere
23 (v6) DENY Anywhere (v6)
$ sudo ufw status | grep -i allow
Nginx Full ALLOW Anywhere
OpenSSH ALLOW Anywhere
Besides using ufw on the terminal, we can install gufw. gufw is a graphical application tool powered by ufw. We can also use it to manage our firewall including checking its status.
To install it, let’s run:
$ sudo apt install gufwAfterward, we can open the application either through the terminal or by clicking on the app itself. To open it from the terminal, we run:
$ sudo gufwThereafter, we check the status. By default it’s not enabled and the status switch is off:
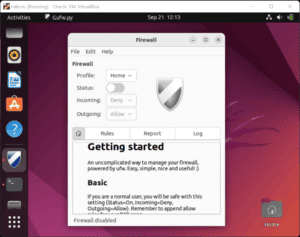
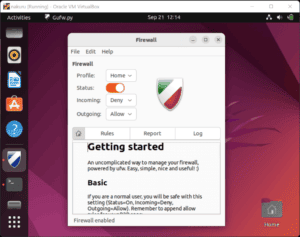
The status switch turns to orange when the firewall’s active:
Aside from ufw, we can also use firewalld to manage our firewall rules. firewalld provides a dynamically managed firewall. It supports network/firewall zones that define the trust level of network connections.
It doesn’t come preinstalled in some distros (for RedHat-based distros it’s the default). For those that lack it, we can install it:
$ sudo apt update
$ sudo apt install firewalldfirewalld can run alongside ufw. But we’ve to disable ufw if it’s enabled. This is solely to avoid any conflicts that may occur.
The firewall should run by default after the installation. Let’s check its status using:
$ sudo firewall-cmd --state
$ sudo firewall-cmd --list-allApart from the firewall-cmd command, we can use systemctl status firewalld to check if the firewalld service is running:
$ sudo systemctl status firewalld
● firewalld.service - firewalld - dynamic firewall daemon
Loaded: loaded (/lib/systemd/system/firewalld.service; enabled; vendor preset: enabled)
Active: active (running) since Fri 2022-09-23 13:47:20 UTC; 49s ago
Docs: man:firewalld(1)
Main PID: 2292374 (firewalld)
Tasks: 2 (limit: 1119)
Memory: 24.3M
CPU: 366ms
CGroup: /system.slice/firewalld.service
└─2292374 /usr/bin/python3 /usr/sbin/firewalld --nofork --nopidWe can also use iptable to check the status of our firewall.
iptables are used to set up, maintain, and inspect the tables of an IP packet filter rule in the Linux kernel. The tables contain in-built chains and may also have user-defined chains (a chain is a list of rules). To view the chains, we run:
For instance, when the firewall is running and the rules are set, the rules are listed:
$ sudo iptables -L -v
Chain INPUT (policy DROP 1899K packets, 119M bytes)
pkts bytes target prot opt in out source destination
13M 1737M ufw-before-logging-input all -- any any anywhere anywhere
Chain FORWARD (policy DROP 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
0 0 ufw-before-forward all -- any any anywhere anywhere
Chain OUTPUT (policy ACCEPT 5531 packets, 644K bytes)Otherwise, we get an empty table, showing three rows with no rules specified:
$ iptables -L -v
Chain INPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain FORWARD (policy DROP 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain OUTPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destinationIn this article, we’ve looked at three ways we can check if the firewall is up and running in Linux. Depending on our distribution, we’ll always find one of these three available by default.
We learned that it’s important we only activate one firewall at a time. For ufw, we saw that it also has a graphical interface gufw we can use.
Lastly, we discussed how we can check if the firewall’s status, i.e., whether it’s running on our machine.