Learn through the super-clean Baeldung Pro experience:
>> Membership and Baeldung Pro.
No ads, dark-mode and 6 months free of IntelliJ Idea Ultimate to start with.
Last updated: March 18, 2024
In this tutorial, we’ll study what is rolling code and how it works. We’ll start with a brief description of its concept and operation. Then, we’ll look at an example to further clarify. Finally, we’ll examine the reasons for rolling code to prevent attacks.
Rolling code, also known as hopping code, is a security technique commonly used in remote keyless entry systems. Actually, many current systems employ this technique, including vehicle locking systems, garage door openers, and other wireless remote control systems.
In such systems, we’ve two devices: a transmitter and a receiver. The transmitter device sends a digital code to the receiver. The receiver, in turn, performs an action (for instance, opening the door) if it confirms that the code is valid.
Therefore, the primary purpose of a rolling code is to prevent unauthorized access to the system. The basic idea is to make it difficult for an attacker to intercept and replicate any code exchanged between the transmitter and receiver.
Thus, a remote control that uses the rolling code feature generates a new code every time we press a button. Both the transmitting and receiving devices use a strategy that allows the receiver to check whether each code is valid.
In addition, after receiving a valid code, the receiving device will only respond again to the next valid code. It makes stolen codes useless for intruders, as a code is only valid once.
Next, let’s look at an example of using the rolling code technique to understand how it works.
In this example, we depict how the rolling code works when applied to a car’s remote locking system. In the case described, the remote control device is a car key fob, and the receiving device is the car’s central locking system.
The figure below illustrates such a case. The full procedure contains four steps: (1) initial synchronization, (2) code generation, (3) counter increment, and (4) receiver verification:
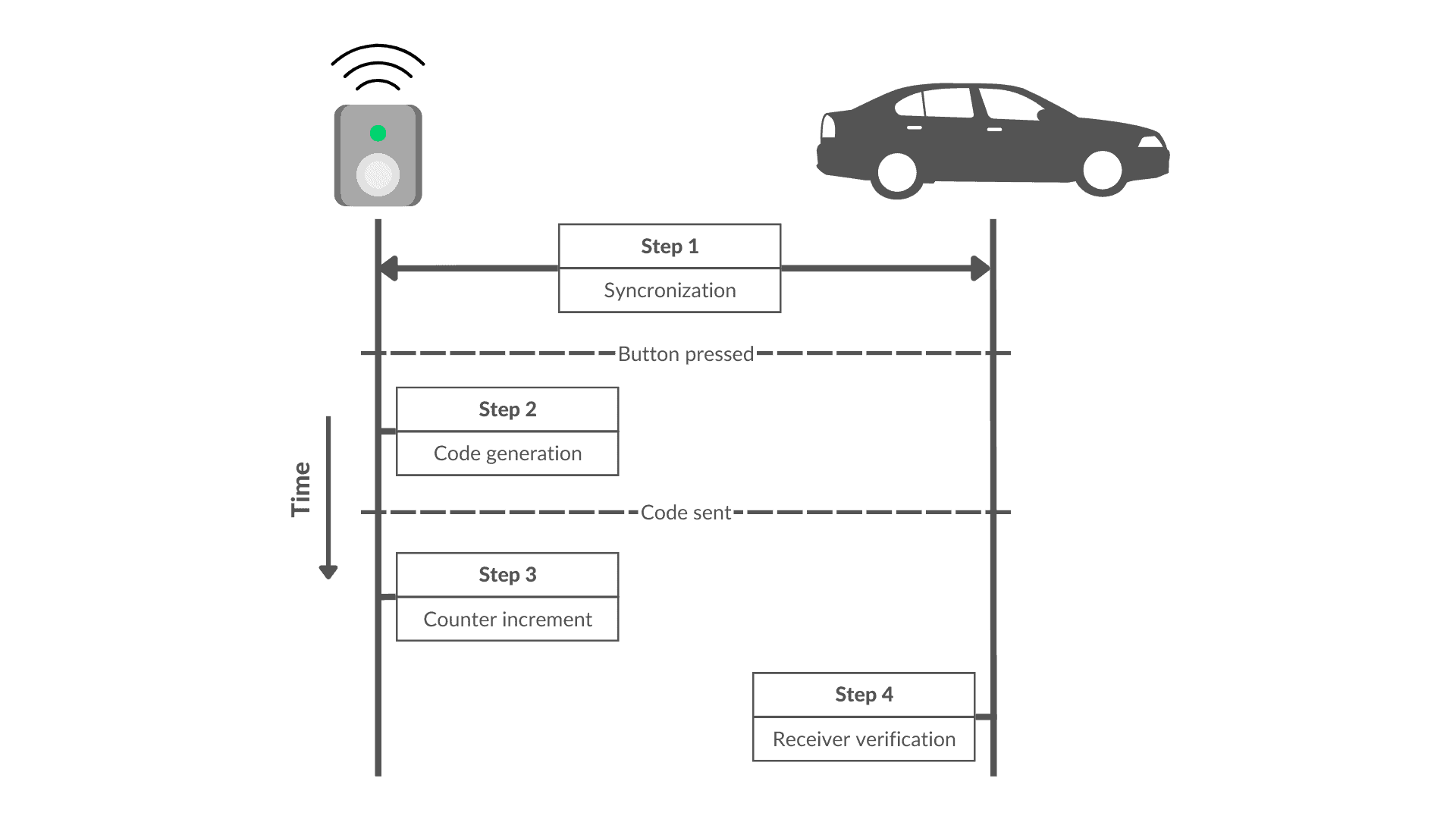
In the initial step, we need to pair the car key fob with the car’s central locking system. In this way, both devices establish a synchronized start code and counter.
From that moment on, every time we press a button on the remote control, it generates and sends a unique code to the receiving device (step 2). In this step, an algorithm generates the unique code, taking into account the synchronized code and the counter.
After each transmission, the transmitting device increments its counter (step 3). This ensures that the next code sent will be different from the previous one.
The receiving device performs a validation check on each code received (step 4). A common approach to performing this validation is to check whether the received code is present in a window of the next valid codes.
To be more precise, let’s say that is the counter used to generate the previous valid code. Therefore, the receiving device will only accept the received code if it confirms that the transmitter generated the code using a counter in the range
. Otherwise, the receiving device will reject the code.
Also, in step 4, after successfully validating a code and performing the intended action, the receiving device updates its local counter. In other words, it assigns to its counter the value in the range that was found during the validation of the most recently received code.
An important benefit is that the rolling code technique eliminates vulnerabilities that exist in the fixed code technique. This prevents, for example, replay attacks, in which the attacker deliberately repeats or even delays code.
What provides security in the rolling code feature is the fact that a code is only valid once. That is, even if an attacker intercepts a transmitted code, that code will become obsolete after it has been used, as the counter is incremented for the next transmission.
In addition, without knowledge of the synchronized code and the counter value, it’s extremely challenging for an attacker to predict or replicate future codes. The devices only exchange code during the synchronization stage.
For this reason, it’s essential to synchronize devices only in secure environments, away from possible intruders. Otherwise, an intruder could compromise the system during the synchronization phase.
In this article, we studied the concept of rolling code. As we’ve learned, rolling code is a security technique that significantly reduces the risk of unauthorized access to keyless entry systems. Its operation is based on the idea that one device sends commands to another via codes that are generated from a previously established counter.
Given the widespread use of this technique in keyless entry systems, we can conclude that rolling code potentially makes it more challenging for intruders to gain access to vehicles, garage doors, or other secure areas.