1. Introduction
Random access protocols refer to communication protocols used in computer networks. Hence, each device has an equal privilege to access the network and transmit data. These protocols allow nodes to send and receive data without taking turns or waiting for permission.
In this tutorial, we’ll discuss the Pure ALOHA. We’ll start with the random access protocols and then focus on the Pure ALOHA.
2. Random Access Protocols
Random access protocols are communication protocols that allow multiple devices to access a shared communication channel or medium in random or arbitrary order. Devices access the medium by using a method called random access. Some common examples of random access protocols are as follows:
2.1. ALOHA
ALOHA is an early random access protocol used in computer networks. It was first used in the ALOHAnet network at the University of Hawaii in the 1970s. The basic operation of the ALOHA protocol is as follows:
- Devices can transmit data whenever they have a message to send
- If two or more devices transmit simultaneously, their messages will collide and be corrupted
- Devices that detect a collision will wait for a random amount of time before trying to transmit again
ALOHA has two variants:
- Pure ALOHA: In this version, devices can transmit at any time. There is no coordination between devices
- Slotted ALOHA: The slotted ALOHA divides time into slots and only allows devices to transmit at the beginning of a slot, which reduces the probability of collision
2.2. CSMA/CD
CSMA/CD stands for Carrier Sense Multiple Access with Collision Detection. It is a network access control method used in Ethernet networks. The purpose of CSMA/CD is to avoid collisions between network devices trying to transmit data at the same time.
The basic idea behind CSMA/CD is that before a network device transmits data, it listens to the network to check whether the network is busy. If the network is busy, the device waits until the network is free. If the network is idle, the device starts transmitting its data.
While transmitting, the device continues to listen to the network to detect collisions. If a collision is detected, the device stops transmitting and sends a jam signal to indicate to all other devices on the network that a collision has occurred. After sending the jam signal, the device waits for a random amount of time before retrying its transmission.
2.3. CSMA/CA
CSMA/CA stands for Carrier Sense Multiple Access with Collision Avoidance. It is a network access control method used in wireless networks such as Wi-Fi. The purpose of CSMA/CA is to avoid collisions between network devices trying to transmit data at the same time, as well as to manage the shared medium of the wireless network.
The basic idea behind CSMA/CA is similar to CSMA/CD, in that devices listen to the network to check whether the medium is busy before transmitting data. However, in wireless networks, collisions are more difficult to detect due to the nature of wireless communication. As a result, CSMA/CA also includes a collision avoidance mechanism.
Before transmitting data, a device using CSMA/CA sends a request to transmit called a Request to Send (RTS). If another device is currently transmitting, it will not respond to the RTS. If the medium is free, the device receiving the RTS will send a Clear to Send (CTS) message to indicate that it is ready to receive data. The original device then sends its data.
During the transmission, other devices on the network will not transmit data to avoid collisions. After the transmission is complete, the receiving device sends an acknowledgement (ACK) message to confirm that the data was received. If the transmitting device does not receive an ACK, it will assume that a collision has occurred and will retransmit the data after a random amount of time.
2.4. TDMA
TDMA stands for Time Division Multiple Access. It is a network access control method used in telecommunications networks, including cellular networks and satellite communication systems.
The purpose of TDMA is to allow multiple users to share the same frequency band by dividing it into time slots. In a TDMA system, each user is allocated a specific time slot during which they can transmit data. During their assigned time slots, users can transmit data without interference from other users.
2.5. FDMA
FDMA stands for Frequency Division Multiple Access. It is a network access control method used in telecommunications networks, including cellular networks and satellite communication systems.
The purpose of FDMA is to allow multiple users to share the same communication channel by dividing it into separate frequency bands. During communication, each user transmits data in their assigned frequency band, and the receiver uses a corresponding frequency band to receive the data.
2.6. 802.11
The 802.11 protocol is a set of standards for wireless local area networks (WLANs), commonly known as Wi-Fi. It is a protocol suite that defines the specifications for wireless communication between devices such as laptops, smartphones, and other mobile devices.
It defines the Wi-Fi network’s physical layer (PHY) and media access control (MAC) layer. The PHY layer defines the modulation scheme, transmission power, and other physical characteristics of the wireless transmission. The MAC layer defines the access method to the wireless medium, which enables multiple devices to share the same wireless channel.
3. Pure ALOHA
Pure ALOHA is a simple and early random access protocol.
In this protocol, any device can transmit data anytime without checking whether the channel is in use. This can lead to collisions, where two or more devices transmit simultaneously, resulting in data corruption and lost packets.
The following diagram illustrates how a Pure ALOHA operates:
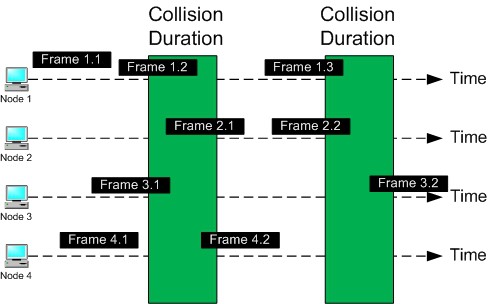
Pure ALOHA employs a “send and hope” mechanism to recover from these collisions. Devices send their data and hope it reaches its destination without colliding with other transmissions. If a collision occurs, the devices involved wait for a random amount before resending the data.
3.1. Working Principles of Pure ALOHA
Here are the steps involved in the Pure ALOHA protocol:
- The first step is for each node in the network to listen to the communication channel and wait for an idle period. If the channel is busy, the node waits for the current transmission to finish before proceeding
- Once the node detects an idle period, it transmits its data packet onto the communication channel
- After transmitting the packet, the node waits a random amount of time before checking if the transmission was successful
- The node waits for another random amount of time before retransmitting the packet when the node detects a collision
- If the transmission was successful (i.e., no collisions), the node can then listen for an acknowledgement (ACK) signal from the receiver to confirm that the packet was received successfully. If the node does not receive an ACK signal, it assumes the transmission failed. Then, it will retransmit the packet after waiting for another random amount of time
- The node will continue to retransmit the packet until a successful transmission is achieved or a maximum number of retries is reached
- Once the node has successfully transmitted its packet and received an ACK signal, it can then begin the process of listening for another idle period and transmitting another packet
3.2. The Throughput of Pure ALOHA
Following is the formula for calculating Pure ALOHA’s throughput:
where is the throughput,
is the offered load (i.e., the average number of transmission attempts per unit of time), and
is the mathematical constant approximately equal to 2.71828. The maximum throughput occurs when
= 0.5, which means that each user attempts to transmit, on average, once every two-time unit. In this case, the throughput is:
The following diagram shows the graph of the throughput for the Pure ALOHA:
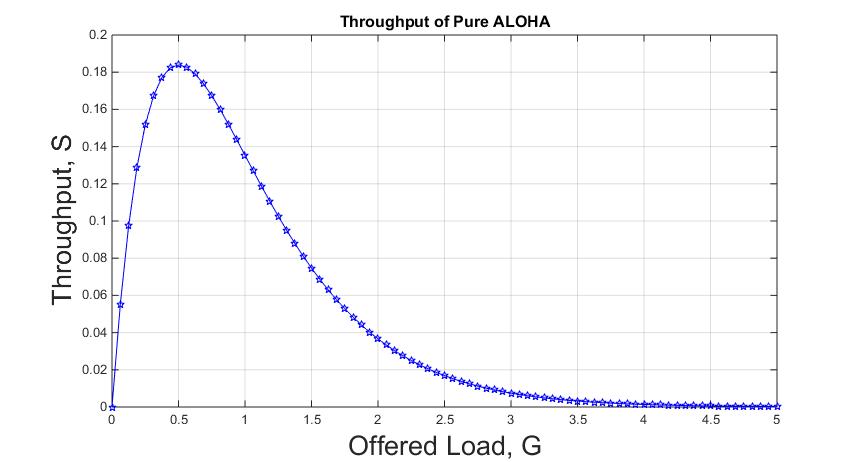
In summary, the maximum throughput of Pure ALOHA is approximately 18.4% of the channel capacity. However, in practice, the actual throughput will be lower due to collisions. Collisions occur when two or more users attempt to transmit simultaneously. This causes signals to interfere with each other and make the data unreadable.
4. Conclusions
In this article, we talked about Pure ALOHA, its working principles, and its efficiency.
Pure ALOHA is a simple protocol allowing multiple nodes to share a single communication channel. However, it is inefficient due to the high probability of collisions. Thus, it laid the foundation for developing more sophisticated random access protocols, such as Slotted ALOHA and CSMA/CD.