Learn through the super-clean Baeldung Pro experience:
>> Membership and Baeldung Pro.
No ads, dark-mode and 6 months free of IntelliJ Idea Ultimate to start with.
Last updated: March 18, 2024
The evolution of networks and the Internet leads to the review of the communication protocols employed on it. It is a natural phenomenon since both the number of users and different technologies that rely on network communication have increased every year. Thus, the networks change according to these users and technologies requirements.
Examples of reviewed protocols are HTTP (V1.1 in 1999 and V2.0 in 2015), SMNP (V1 in 1990, v2 in 1999, and V3 in 2002), and IP (V4 in 1981 and V6 in 1995). Moreover, before these examples, a relevant change in how the networks communicate occurred in the ’70s: the splitting of TCP into TCP, IP, and other protocols.
However, there exist characteristics of current TCP inherited from legacy TCP. So, to tackle these legacy characteristics, TCP considers the existence of a pseudo-header.
In this article, we’ll explore the pseudo-header in the context of TCP. First, we’ll have a historical review of TCP. At this point, we’ll see relevant characteristics of both early to modern TCP. So, we’ll investigate the pseudo-header in TCP. Finally, we’ll discuss the relevance of the pseudo-header nowadays.
The very first version of TCP was proposed by Robert Elliot Kahn Vinton Gray Cerf in 1973. At this moment, TCP was the Transmission Control Program instead of Transmission Control Protocol, as it is known today. But, the goals of this early TCP were fully compatible with modern TCP goals:
However, at this point, TCP dealt with both network routing and transportation of network traffic. In summary, IP was not used in this context. Thus, information about a packet origin and destination, for example, was in charge of TCP.
The RFC 675 documented and presented in detail this early version of TCP. One of the most interesting points that show the difference between the early and modern TCP is their headers. The following image summarizes the early TCP header:
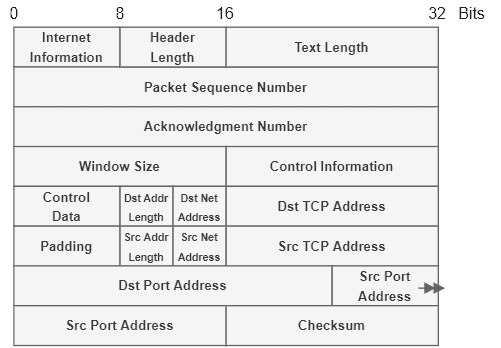
As time passed and the networks became more complex, the need for heterogeneous layers for network routing and transportation grew. In such a way, in 1976, the efforts to shift from early TCP to modern TCP/IP began. Finally, the RFC 791 and RFC 793 formally presented the modern TCP/IP in 1981.
With the network routing now handled by IP, TCP got simplified in terms of its required information. The following image depicts the modern TCP basic header:
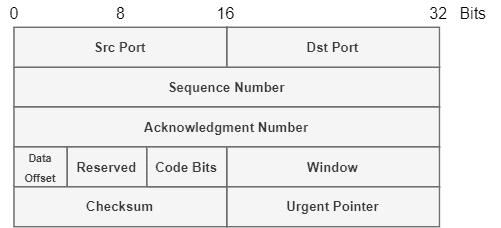
The transition from the early TCP to the modern TCP/IP led to some challenges. One relevant example is that TCP (both early and modern) is, by definition, an end-to-end protocol. In such a way, origin and destination addresses play a crucial role in sending and receiving messages over TCP.
For example, the TCP checksum must consider the endpoint addresses (as well as other information), ensuring that they were not corrupted in the transmission. However, in TCP/IP, relevant pieces of information are now located in the IP header instead of the TCP header. In this scenario, IP works as a wrapper for TCP in the network layer.
So, a pseudo-header emerged in TCP to keep the end-to-end feature of TCP and avoid replication of data available in the IP header. The pseudo-header consists of parts of the IP header. It covers relevant fields of the IP header that are static (do not change in the routing of packets).
The pseudo-header contains a total of 12 bytes with the following fields:
The following image shows the fields that compose the pseudo-header:
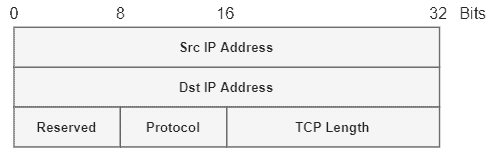
A specific application of the pseudo-header is to calculate the TCP checksum. In addition to the pseudo-header, the TCP checksum also employs the protocol header and body. After calculation, the TCP checksum value is allocated into the checksum field of the TCP header.
It is relevant to highlight that the pseudo-header is defined on-demand. It means that it is not explicitly sent within a packet. In the checksum case, first, the pseudo-header is created to calculate the checksum and then discarded. Thus, the receiver recreates the pseudo-header to evaluate the checksum when the packet arrives at the destination.
One historical reason to use the pseudo-headers was security. The idea was to employ encryption and authentication in TCP and the pseudo-header data. In this way, the designers aimed to mitigate attacks, such as man-in-the-middle, by protecting addressing information.
These security protocols did not advance for several reasons. But, as we studied in the last section, the checksum still uses the pseudo-header. Due to this, TCP keeps the pseudo-header so far.
However, there is a tense relation between IP and TCP because of the pseudo-header. It means that we’ll need to rethink TCP every time IP changes. For example, the transition from IPv4 to IPv6 will require modifications on the pseudo-header. As a consequence, the checksum calculation of TCP will change too.
Considering the described scenario, the designers will need to evaluate if keeping the pseudo-header is a good choice in the next generations of networks.
In this article, we learned about the pseudo-header in the context of modern TCP/IP. First, we studied the historical context from early TCP to TCP/IP. Then, we in-depth explored the concept of pseudo-header and saw applications of it. Finally, we discussed the challenges related to the pseudo-header nowadays.
Given that the projects regarding TCP security and authentication did not prevail, we can conclude that the pseudo-header of TCP/IP did not achieve its full potential. But, other applications, such as checksum, maintain the pseudo-header useful nowadays. So, it remains to know if it is sufficient to keep the pseudo-header used in future networks.