1. Introduction
Deadlocks are one of the most difficult-to-debug problems in Computer Science. Particularly, these problems occur when two or more processes are waiting for each other to access the same resources, resulting in a deadlock situation where none of the processes can proceed.
Furthermore, deadlocks can occur in any system where resources are shared between multiple processes, such as operating systems, databases, and distributed systems.
One of the foremost used techniques to overcome deadlocks is the Ostrich algorithm. It is a widely used technique for ignoring deadlocks in computer systems and is commonly used by single end-users.
In this tutorial, we’ll discuss the Ostrich algorithm, how it works, and its advantages and disadvantages.
2. Deadlock Ignorance
Deadlock ignorance occurs when system designers and programmers don’t consider the possibility of a deadlock in their design or coding.
This can result in a system that is stuck, unresponsive, and unable to complete its intended tasks. Furthermore, deadlock ignorance can be caused by system complexity, lack of communication between teams, and assumptions that deadlocks are rare.
To address deadlock ignorance, it is essential to inform the system designers and programmers about the risks and techniques available to prevent them. This includes understanding the underlying causes of deadlocks and employing strategies such as resource ordering, timeout mechanisms, and deadlock detection and recovery.
In the same context, the Ostrich algorithm is a specific implementation of deadlock ignorance used in many operating systems and other computer systems.
3. How Does the Ostrich Algorithm Work?
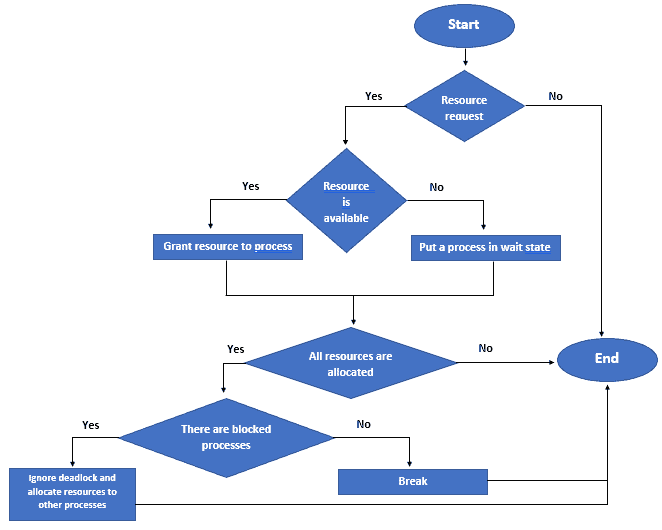
The Ostrich algorithm is based on the idea of preemptive resource allocation. This means that when a process requests a resource, the operating system checks to see if the resource is available.
If the resources are available, the operating system grants the resources to the process. If it isn’t available, the operating system puts the process in a wait state until the resources become available.
In addition, if a process requests a resource that isn’t available, the operating system simply ignores the deadlock and continues to allocate resources to other processes. This means that the system can continue to function even in the presence of deadlocks.
We should keep in mind that the Ostrich algorithm isn’t a perfect solution to the deadlock problem. A system can become completely deadlocked if all processes are waiting for resources that aren’t available. In practice, this situation is rare, and the algorithm effectively prevents most deadlock situations.
The following flowchart shows how the Ostrich algorithm works:
4. Advantages and Disadvantages of the Ostrich Algorithm
While the Ostrich algorithm can be useful for preventing deadlocks in certain situations, it has drawbacks.
The following table discusses the advantages and disadvantages of the Ostrich algorithm:
In summary, we should carefully consider the advantages and disadvantages of the Ostrich algorithm before deciding whether to use it in our systems.
5. Conclusion
Deadlocks are a complex problem that can occur in any system where resources are shared between multiple processes. Moreover, deadlock ignorance is a technique used to deal with deadlock situations by ignoring them completely, and the Ostrich algorithm is a widely used implementation of this technique.
While the Ostrich algorithm has several advantages, such as allowing the system to continue functioning and being easy to implement, it also has some disadvantages, such as potentially causing instability and making it difficult to diagnose problems in the system.
In conclusion, the Ostrich algorithm can effectively prevent deadlocks in systems where resources are frequently shared among multiple processes. However, it isn’t a perfect solution, and careful consideration must be taken when implementing it in complex systems.