Yes, we're now running our Black Friday Sale. All Access and Pro are 33% off until 2nd December, 2025:
What Are Rings in Operating Systems?
Last updated: March 18, 2024
1. Overview
In this tutorial, we’ll explain what the protection rings in the operating system are and why we need them. We’ll also discuss different levels of protection rings and implementation details in different processor architectures.
2. What Are Rings in Operating Systems?
Operating systems have a number of different layers. Each of these layers has its own privileges. We use protection rings term while mentioning this system. Operating systems manage computer resources, like processing time on the CPU and accessing the memory. Since computers run more than one software process, this will bring some issues. Protection rings are one of the key solutions for sharing resources and hardware.
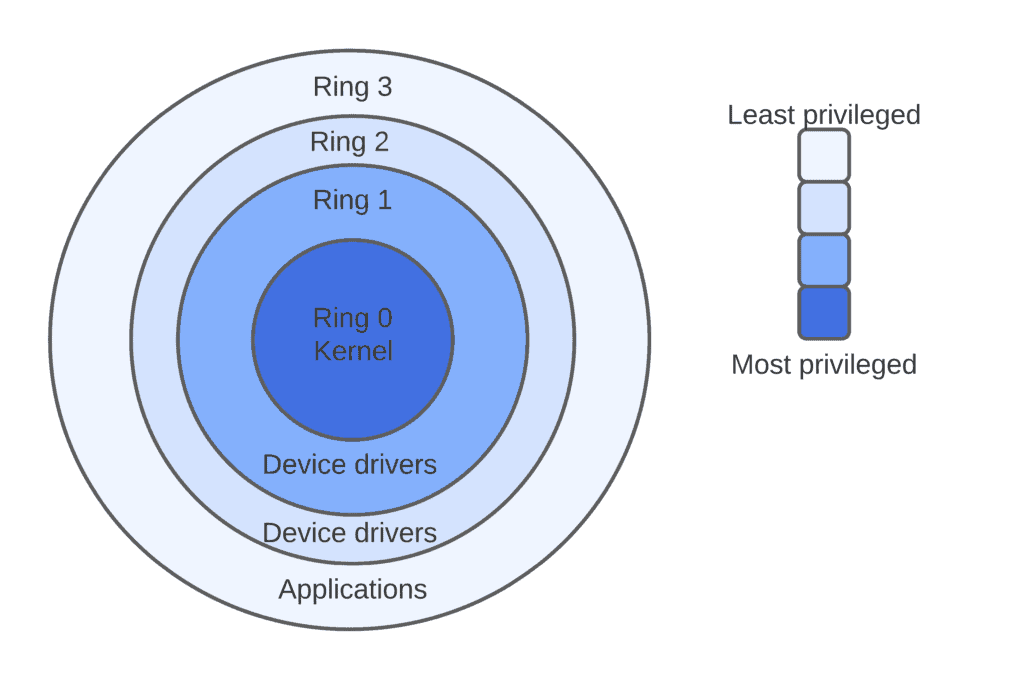
So, what happens is that processes are executed in these protection rings, where each ring has its own access rights to resources. The central ring has the highest privilege. The outer ones have fewer privileges than the inner ones. The figure below represents the protection rings for x86 processor architecture which is one of the common processor architectures.
As we’ve seen, it has four rings numbered from 0 to 3:
 a
a
3. Why Do We Need Them?
There are some advantages and benefits to implementing protection rings in the OS.
First and foremost, it protects the system against crashes. For example, an application that we use in our computers can freeze or crash, however, we can recover them by restarting the application. Errors like these in higher rings are recoverable.
Because these programs don’t have direct access to memory or CPU. Only ring 0, the kernel has direct access to hardware resources. In this way, we can restart an application without losing data or causing an error in the CPU.
Furthermore, protection rings offer increased security. For example, a process can require some instructions that require more CPU resources. In such a case, this process must request permission from the OS. The OS can decide whether grant the request or deny it. This process protects the system from malicious behavior.
4. Levels of Protection Rings
4.1. Ring 0
The kernel, which is at the heart of the operating system and has access to everything, can access Ring 0. The code that runs here is said to be in kernel mode. Kernel-mode processes have the potential to affect the entire system. If something goes wrong here, the system would most likely crash. Because this ring has direct access to both CPU and system memory.
4.2. Ring 3
User processes running in user mode have access to Ring 3. Therefore, this is the least privileged ring. This is where we’ll find the majority of our computer applications. Since this ring doesn’t have any access to the CPU or memory, any instructions involving these must be passed to ring 0.
4.3. Ring 1 and Ring 2
On the other hand, rings 1 and ring 2 offer unique advantages that ring 3 lacks. The OS uses ring 1 to interact with the computer’s hardware. This ring would need to run commands such as streaming a video through a camera on our monitor. Instructions that must interact with the system storage, loading, or saving files are stored in ring 2.
These rights are known as input and output permissions because they involve transferring data into and out of working memory, RAM.
In ring 2, for example, loading an Excel file document from storage. In such a case, ring 3 will be responsible for editing and saving the data.
5. How to Implement Protection Rings?
Most of the CPU architectures such as x86 include some form of protection rings. However, some of the operating systems such as Linux, macOS, and Windows doesn’t fully utilize these feature. While Linux and Windows use only ring 0 and ring 3, some other operating systems can utilize three different protection levels.
On the other hand, ARM 7 which is one of the other common processor architectures implements three privilege levels: application, operating system, and hypervisor. ARM 8 implements four protection levels. In addition to existing levels in ARM 7, it adds a secure monitor level.
As we’ve discussed, ring 0 and ring 3 are the essential levels, and ring 1 and ring 2 are optional protection levels.
6. Conclusion
In this tutorial, we’ve defined protection rings and the main purposes of such a system. And then, we’ve also discussed the different levels of protection rings and their responsibilities.
Finally, we’ve shared details about the implementation of protection rings in different processor architectures and operating systems.