Learn through the super-clean Baeldung Pro experience:
>> Membership and Baeldung Pro.
No ads, dark-mode and 6 months free of IntelliJ Idea Ultimate to start with.
Last updated: March 18, 2024
In this tutorial, we’ll explain the Medium Access with Collision Avoidance (MACA) protocol. First, we’ll show the need for this protocol. Then, we’ll explain how the protocol works. Finally, we’ll show how it solves the problem of access control in a shared medium.
Let’s imagine a family of five persons. The mother and father are Alice and Bob, but we’ll call them A and B for short. A and B have three children: Charlie, David, and Emma. We’ll call the children C, D, and E. One day, the family decides they should all listen to ten minutes of relaxing music in bed and before sleeping.
However, they want to do this as a family activity. So, in each family member’s room, they install a music player with a high-quality speaker whose sound can be heard in all other rooms. This way, if any family member plays music on their speaker, all other members will hear it. Now, they have to find an answer to two important questions. These are: who’s going to play the music? and when? The picture below depicts this setting:
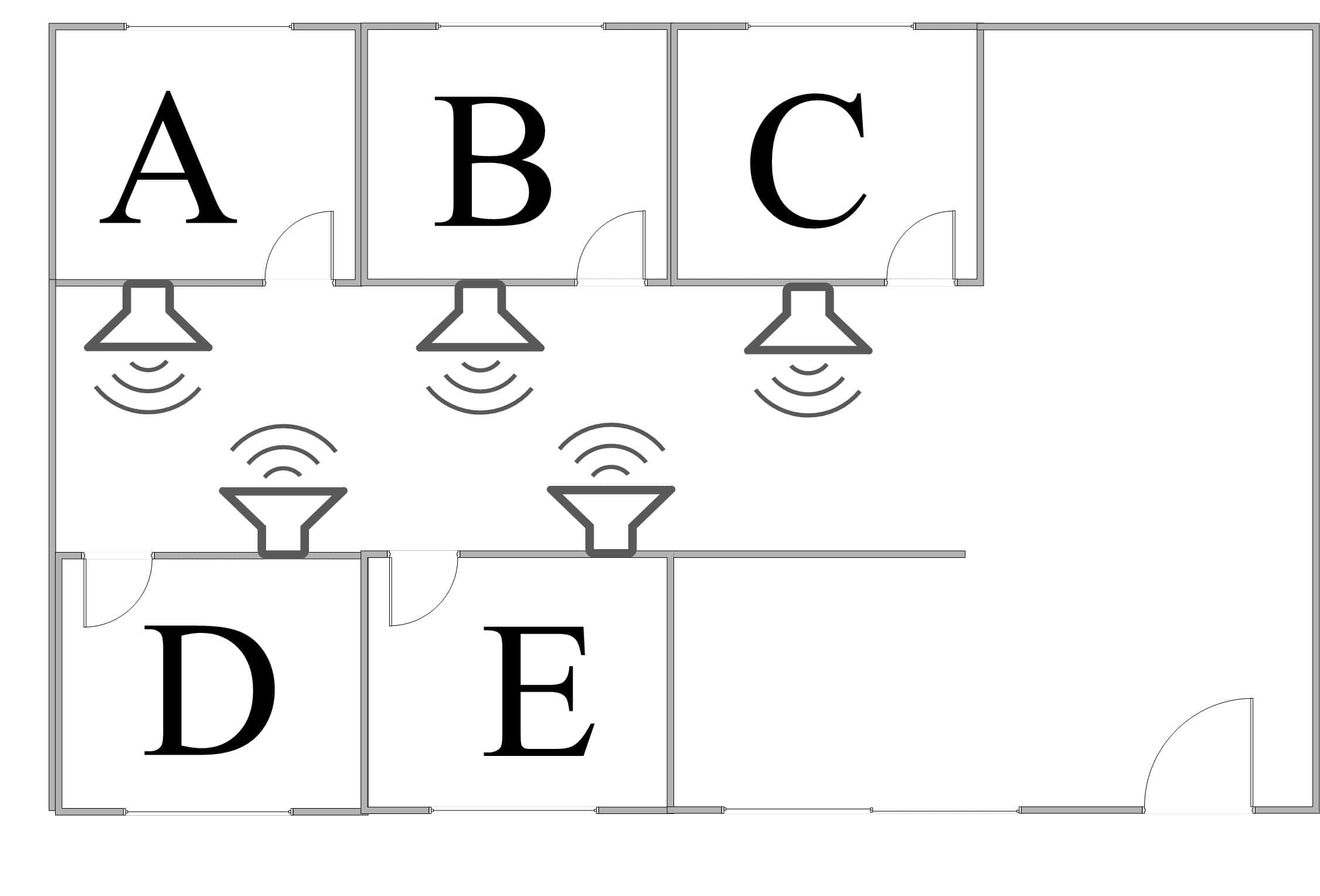
Considering the family’s situation, we can imagine why they are facing some challenges. First, to simplify the situation, we assume they all share the same taste in music. Now, we are left with a possible problem. Namely, if two or more speakers play music at the same time. In technical terms, this is called a collision.
Specifically, A collision may occur when multiple sources use the same medium to send a signal. Of course, in our case, the sources are the speakers, the signal is the music, and the medium is air. We deal with communication system collisions using a Medium Access Control (MAC) algorithm.
Let’s consider some methods that the family could follow as a solution to their MAC challenge:
Of course, the two methods above require coordination between family members. However, sometimes coordination is hard to achieve. This is especially the case when some members frequently ask to change their time slot or the part they play from a music piece.
So, we think of a simpler method, we’ll call it “ask-permit”. In this new method, a family member wanting to play music will announce this. For instance, C might shout, “Hey D, I would like to play the music today”. He then waits to hear, “OK, go ahead”. Only then will he turn on his music player. Consequently, other family members will abstain from playing music for that night.
Now, we’ll consider this situation in a technical setting. Instead of family members, we’ll have communicating devices, and we’ll dig into the details.
Let’s consider a number of communicating devices sharing the same medium. These, for instance, are computers with wireless communication capability, e.g., WiFi. We would like them to communicate while avoiding any collisions, i.e., two or more devices transmitting at the same time. Let’s first consider some practical aspects of device communication.
We assumed that, in our family’s home, when a family member plays music, all other members can hear it clearly. This is the case when the shared medium (air in the case of music) causes low losses in the transmitted signal. However, in some cases, like wireless communications, signals lose power as they propagate.
Each communicating device will thus have a transmission range expressed as a distance. Only the devices located within this distance will be able to receive the transmission.
Also, in the family’s case, music is a broadcast signal. In other words, it is intended for all family members. In device communication, we also have broadcast signals. However, device A may sometimes wish to send data to a specific device B. Other devices may also receive this data. But this is a side-effect due to the nature of the medium, e.g., wireless media.
Now, let’s consider this latter situation where device A device would like to send some data to device B. To eliminate collisions, we’ll follow our “ask-permit” method.
In Medium Access with Collision Avoidance (MACA), A first sends a signal to B, asking for permission to communicate. We’ll call this signal Request To Send (RTS). Then, if B is free to communicate, it will send a Clear To Send (CTS) signal to A. Any node other than A that receives this CTS will not start any new transmission. Now, A will have the medium for itself and can send the data to B. These steps are shown in the figure below:
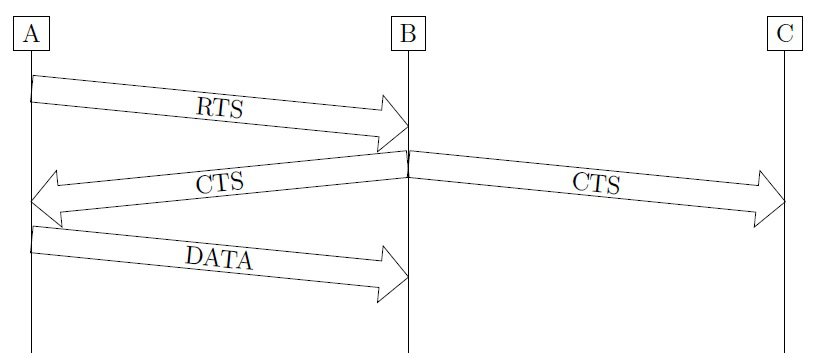
In the figure, we note that C is outside A’s range. That’s why it didn’t receive A’s RTS signal. Similarly, A is outside C’s range. In other words, they are “hidden terminals” with respect to one another. However, they are both in B’s range. But how about collisions? Let’s study MACA’s performance in this respect.
MACA aims at avoiding collisions. In order to judge its performance, we first need a closer look at the hidden terminal problem.
In the previous figure, we saw that A and C are hidden with respect to each other. This means that if both A and C start sending data to B, neither of them will know that the other is transmitting. However, the transmitted signals will collide at B.
MACA was basically designed to avoid this situation. In fact, when C hears the CTS signal that B sent to A, it will refrain from starting communication with B. There remains however some slight possibility of collision.
Before receiving the CTS signal, C is free to start transmission. Now, let’s imagine a situation where both A and C send an RTS signal to B at (almost) the same time. Both of these signals will collide at B.
Due to this collision, B will not send a CTS signal to either of them. After some delay, they may retry transmission by sending a new RTS. However, in order to prevent a new collision from happening, we need them to choose different delays. In fact, they choose this delay at random. This way, the delay will most likely be different.
In this tutorial, we talked about Medium Access with Collision Avoidance (MACA). We explained the motivation behind MACA. Finally, we analyzed its performance with respect to collisions.