Learn through the super-clean Baeldung Pro experience:
>> Membership and Baeldung Pro.
No ads, dark-mode and 6 months free of IntelliJ Idea Ultimate to start with.
Last updated: March 18, 2024
In this tutorial, we’ll discuss a technique used in conjunction with traditional TCP to monitor and analyze network traffic: snooping TCP. Furthermore, we’ll explain the steps involved in this technique with an example.
Finally, we’ll highlight some of the major advantages and disadvantages of this technique.
Mobile network operators employ a practice known as snooping TCP to boost the efficiency of data transmissions over mobile devices. In this method, the network operator keeps tabs on the TCP data exchanged between the mobile device and the internet in order to pinpoint bottlenecks in the connection. In this way, monitoring the data transmission can enhance network performance by fixing the problematic areas in the network.
When a mobile device connects to the internet, it uses TCP/IP to establish a connection with a remote server. Additionally, we can establish such a connection by sending a series of packets between the mobile device and the server. During this process, the network operator can monitor the packets and identify areas where the network performance can be optimized.
Network operators can use snooping TCP to improve traffic flow. For example, any packet loss or delay in the communication between the mobile device and the server can be optimized using snooping TCP. Furthermore, it may involve adjusting the network parameters, such as the size of the TCP window or the number of retransmissions. In addition, it helps reduce latency and improves the overall network performance.
However, it’s important to note that snooping TCP can raise privacy concerns, as it involves monitoring the data traffic of users. Therefore, before implementing this method, network operators must ensure they comply with relevant privacy regulations and obtain the necessary consent from users.
Now let’s discuss how snooping TCP works:
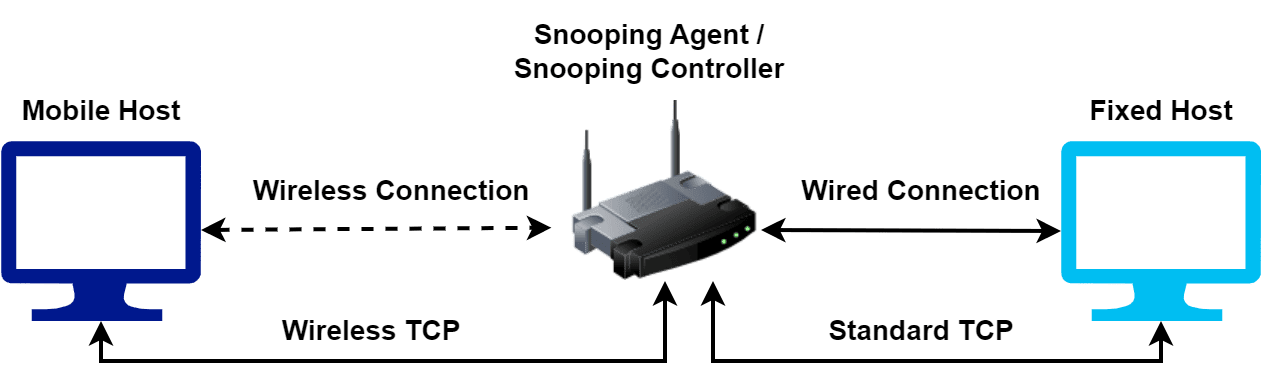
Snooping TCP works by monitoring the TCP traffic between a mobile device and the internet. Additionally, it makes adjustments to the network parameters in order to improve the performance of the network.
The first step is to intercept TCP packets passing through a network switch or router. We can do such an interception by configuring the switch or router to forward a copy of each TCP packet to the snooping process. Next, the snooping process inspects the intercepted packets and extracts information. Additionally, we can extract various information from TCP packets, such as the source and destination IP addresses, TCP port numbers, and sequence numbers.
Moving forward, the snooping process then analyzes this information to gain insights into network behavior. The main objective of this step is to identify potential security threats, troubleshoot network issues, optimize network performance, and prioritize network traffic.
The snooping process may take various actions depending on the specific use case. In some cases, we need to block specific packets and traffic flows. Additionally, we may need to modify packet headers.
Finally, the snooping process sends the analyzed information to the network administrator. The network administrator can use it to make informed decisions about network management and security.
It’s important to note that the exact implementation of TCP snooping can vary depending on the specific network hardware and software being used. Additionally, the implementation process also relies on the specific goals of the network administrator.
Snooping TCP is a method for observing and analyzing network TCP traffic. It can help with network diagnostics, security checks, QoS management, and overall efficiency enhancements. However, it can raise concerns about privacy and the ethical use of network monitoring tools. Let’s summarize the key advantages and disadvantages of snooping TCP:
| Advantages | Disadvantages |
|---|---|
| Can improve network performance, reducing latency and increasing data throughput | Can raise privacy concerns |
| Guarantees that programs have access to enough bandwidth and are resilient to interruptions caused by network congestion | Before implementing, network operators should seek the appropriate permission from end users |
| Leads to more efficient use of network resources | Complex to implement, requiring advanced monitoring and analysis tools |
| Can lead to a better user experience, with faster data transfer, fewer dropped calls, and fewer buffering issues. | May lead to increased network congestion if not implemented properly |
| Reduces the cost of network operation, maintenance, and upgrades | This technique can be abused by network operators to prioritize certain types of traffic |
| Leads to cost savings for network operators and potentially lower prices for users | May interfere with end-to-end encryption, which can compromise the security and privacy of user data |
It’s important to note that snooping on network traffic without proper authorization is generally illegal and unethical. However, there’re some legitimate use cases for snooping TCP.
We can use TCP snooping to diagnose and troubleshoot network issues by analyzing TCP traffic. Additionally, we can also utilize it as part of a security monitoring strategy to prevent unauthorized access, data exfiltration, or other malicious activity on a network.
Furthermore, TCP snooping can be used to prioritize and optimize network traffic based on application or user needs. Moreover, TCP snooping can be employed to analyze network traffic and identify bottlenecks impacting network performance.
Using snooping TCP method, we can also inspect and filter network traffic based on content, such as blocking access to certain websites or data types.
In this tutorial, we discussed a technique used to inspect and analyze TCP traffic on a network: snooping TCP. Furthermore, we explained the steps involved in this technique with an example. Finally, we highlighted some of the core advantages and disadvantages of this technique.