Yes, we're now running our Black Friday Sale. All Access and Pro are 33% off until 2nd December, 2025:
How MAC Flooding and Cloning Attacks Work?
Last updated: March 18, 2024
1. Introduction
In this tutorial, we’ll look into the MAC Flooding and MAC Cloning attacks, how they work, their goal, and how to protect our networks from them. We’ll follow a case where an attacker tries to flood the network and one where they try to clone a MAC address and see how they both are done step by step.
2. Switched LAN Network
Since these attacks target switched LAN networks, let’s quickly examine how such a network generally works.
In a switched network, each device (e.g., computer, server, printer) is connected to a switch. This switch is responsible for keeping track of which device is connected to each port by maintaining a table called the “MAC Address Table”, which maps each device’s MAC address to the corresponding switch port. The MAC address is globally unique for each component, and every entity inside the network has a different hardwired address given by its manufacturer.
When a device on the network wants to communicate with another, it sends an Ethernet frame containing, among other information, the source MAC address and the destination MAC address. The switch receives this frame and uses the destination MAC address to pinpoint the correct port in the MAC Address Table. It then forwards the frame out of that port, and the two devices communicate this way.
3. What Are MAC Flooding and MAC Cloning?
MAC flooding is a cyber attack targeting switches on a local area network (LAN). It involves sending many packets with fake MAC addresses to overflow the switch’s address table, causing it to become full and unable to process any legitimate traffic. Once the table becomes full, the switch will flood all packets to all ports, turning the switch into a hub and potentially causing a denial of service (DoS) condition.
An attacker that can send frames to any device on the network can take several damaging actions. Such an entity can intercept network traffic or even modify it and use this access they have to try to gain access to devices they otherwise wouldn’t have a way into.
On the other hand, MAC Cloning is the act of changing or impersonating the MAC address of a network interface card to match the MAC address of an authorized device on the network. This can allow an attacker to bypass access limitations and gain unauthorized access to the network. MAC cloning can be used with MAC flooding attacks. The attacker can use cloned MAC addresses to generate a flood of packets that appear to come from different authorized devices on the network, possibly bypassing security measures against MAC addresses coming from outside the network.
4. MAC Flooding and MAC Cloning Attack Example
Let’s cover the basic steps a MAC Flooding and MAC Cloning attack roughly goes through.
4.1. MAC Flooding Attack
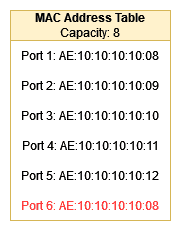
The attacker connects to a switch port and sends many fake Ethernet frames, each containing a different source MAC address but the same destination MAC address. The goal of this step is to flood the switch’s MAC address table with fake MAC addresses in order to fill up the table and force the switch into fail-open mode:
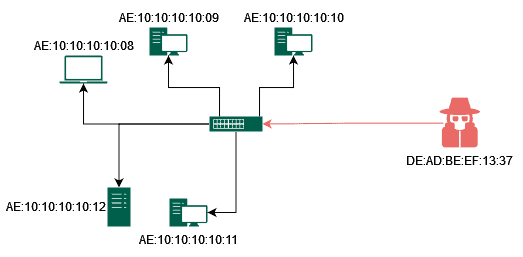
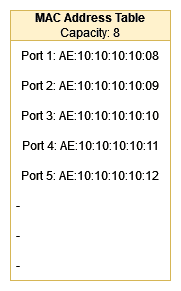
The switch learns the MAC addresses by adding them to its MAC Address Table, but since the attacker uses many different fake addresses, the table quickly fills up. This is why all the MAC addresses the attacker sends must be different for the attack to succeed because if only a set of addresses were used, the MAC Address Table might be able to hold them all without overflowing:
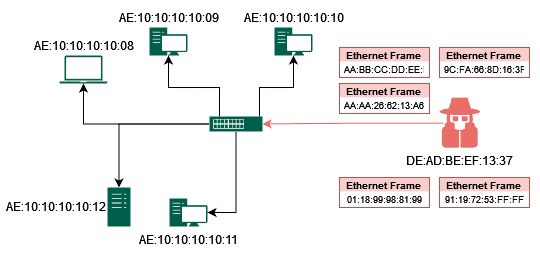

When the MAC address table is full, the switch enters a “fail-open” mode, where it starts forwarding frames to all ports instead of using the table to determine the correct port. Once the MAC address table is full, the switch can no longer use to determine the correct port to forward a frame to. Instead, it starts forwarding all frames to all ports, which causes network congestion and can disrupt network communication:
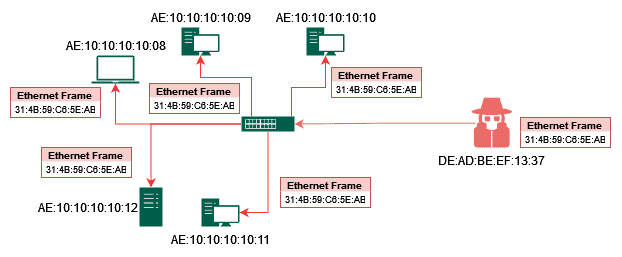
The attacker can now send information to any device on the network, disrupting network communications and even stealing information from outgoing or incoming frames. Now that the attacker has forced the switch into a fail-open mode, they can send frames to any device on the network. This can disrupt network communication and potentially allow the attacker to steal sensitive information, as they can intercept frames meant for other devices on the network. This, of course, depends on other security measures on the network, such as packet encryption.
4.2. MAC Cloning Attack
Now let’s take a look at a MAC Cloning attack to see how it works and try to figure out the differences it would have from a MAC Flooding one:
The attacker monitors network traffic to identify a legitimate device on the network. The attacker monitors network traffic to identify a legitimate device on the network that they want to impersonate. This could be a device with elevated privileges or access to sensitive information:

The attacker spoofs the MAC address of the legitimate device and connects to the network. This allows the attacker to impersonate the legitimate device and potentially gain access to its privileges or sensitive information:

The attacker can now intercept and modify network traffic sent to and from the legitimate device. Now that the attacker has successfully impersonated the legitimate network entity, they can intercept and modify network traffic for that device. This allows the attacker to read on-the-wire information or write their data in the frames:
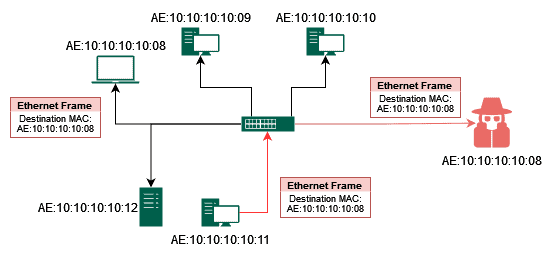
The attacker can also use this access to launch further attacks on other devices on the network. Finally, the attacker can use the access they gained by impersonating the legitimate device to launch further attacks on other devices on the network, be it injecting malicious code, performing man-in-the-middle attacks, trying to elevate their privileges, or gaining user access on servers or other machines and so on.
These two types of attacks, MAC Flooding and MAC Cloning, can come one after the other. Meaning that if one is successful, the attacker can use their elevated privileges to launch the other, depending on the purpose of their meddling with the network.
5. Countermeasures
Since these attacks have been around for some time now, several countermeasures exist.
Firstly, one obvious would be utilizing MAC Address Filtering. MAC address filtering can be used to allow authorized devices and prevent unauthorized devices from gaining access to the network. Network Access Control solutions to mandatory authenticate devices even before they join the network would be related to this.
Secondly, we have port security and virtual LANs (VLANs). These two measures have been proven very effective in mitigating MAC-related attacks. With port security, a network can limit the number of MAC addresses learned on a particular port. In conjunction with this, sensitive and critical traffic can be isolated inside a VLAN for safekeeping against unauthorized devices.
Lastly, the usual security measures apply to network-wide security in these scenarios. IDS and IPS (Intrusion Detection and Intrusion Prevention) systems are nowadays well equipped to deal with such attacks. Network administrators should also be aware of correctly configuring all switches inside their networks, as it can be life-saving.
6. Conclusion
In this tutorial, we looked over how a switched LAN network works, and we saw how a MAC Flooding and a MAC Spoofing attack works. We discussed what the attacker could achieve and how network administrators can mitigate these attacks.