1. Overview
In this tutorial, we’ll discuss trapdoors in cryptography.
Furthermore, we’ll explore how trapdoor works and discuss different types of trapdoors that exist in cryptography.
2. Trapdoors
In cryptography, a trapdoor is a secret backdoor hidden within an algorithm or individual piece of data. The idea is that people can’t find the backdoor without knowing about it in advance. It makes trapdoors extremely useful in cryptography, which keeps information secure by converting it into unbreakable codes.
Cryptography is based on a few fundamental principles. Given a piece of information or plaintext, we produce an encrypted version of the plaintext, known as the ciphertext, with the help of a secret key and an encryption algorithm. Similarly, in order to generate the plaintext back from the ciphertext, we apply a decryption algorithm with a secret key:
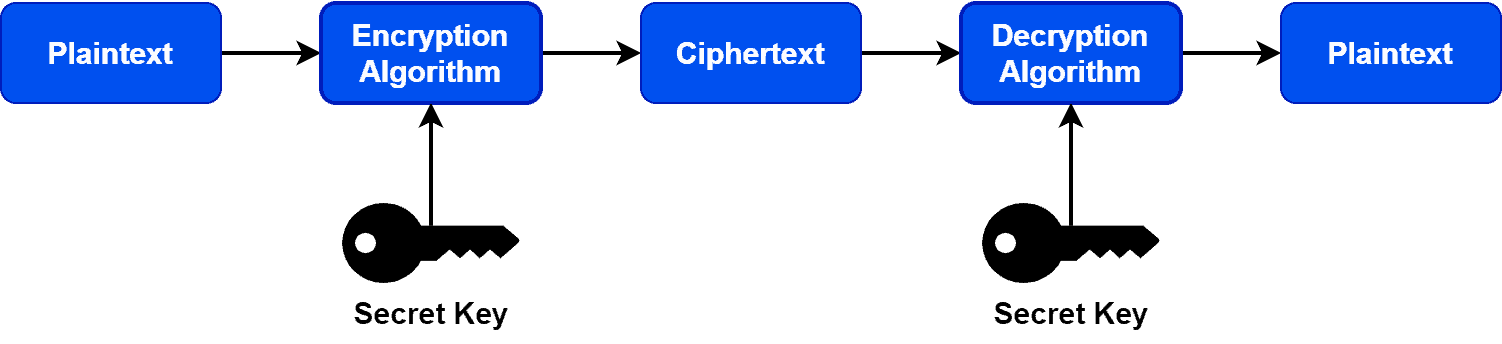
Therefore, it’s impossible to know if a piece of information is secure unless you have access to the encryption key and algorithm used in the encryption process. Additionally, there’re no easy solutions to reverse engineering cryptographic algorithms. However, trapdoors bypass this stage and make it easier to break into an encrypted system.
Trapdoors are a cornerstone of modern cryptography. We use them to protect bank account passwords and government secrets. A trapdoor operates by allowing a user or system with access to the trapdoor to quickly get in while making it impossible for others to find the backdoor. It makes trapdoors unbreakable as long as the developer keeps them secret.
3. Working Procedure
We can use trapdoors to create one-time pad encryption (OTP). OTP is an unbreakable form of encryption that uses a secret key to convert a given phrase into a long string of seemingly random letters. In a one-time pad, we can use the secret key only once to create a unique code that can be decrypted only with the same key. Hence, we can utilize one secret key only once in OTP.
We can often hide trapdoors inside algorithms to generate OTPs, making them almost impossible to find without knowing the exact sequence of steps. In cryptography, we can use trapdoors in four ways: a secret key, a special algorithm, a weak algorithm, and a back door.
A secret key is a piece of code that’s kept hidden from everyone. Only authorized and intended users have access to it. A special algorithm is another form of a trapdoor that includes a set of instructions used to solve a problem or accomplish a specific goal. A special algorithm in the form of a trapdoor provides access to the intended users to get inside a system quickly while making it impossible for other users.
Cryptographers often use algorithms that are flawed by design. It’s an example of a weak algorithm. They do this to keep their code unbreakable, even when other people figure out the algorithm. Finally, a back door is a secret way to get into a computer or system. It’s often used to install viruses or spyware so one can access the system without getting caught.
4. Different Types of Trapdoors
Let’s dive into the different types of trapdoors that exist. In general, there’re three types of trapdoors: one-way, two-way, and one-time trapdoors.
One-way trapdoors are the simplest type of trapdoor. We can use them in public key cryptography to create a secure connection between two users who don’t know each other. One-way trapdoors allow a user to send an encrypted message that only the intended user can read.
The second variant of the trapdoor, the two-way trapdoor, is a bit more complicated but more powerful. The famous RSA algorithm utilizes the two-way trapdoor concept. Usage of RSA algorithm includes eCommerce sites, banks, and web browsers to secure communication between users. Additionally, it ensures the integrity of data.
One-time trapdoors are the most complex type of trapdoor. We use one-time trapdoors in voting systems and anonymous communication networks.
Let’s look at an example:
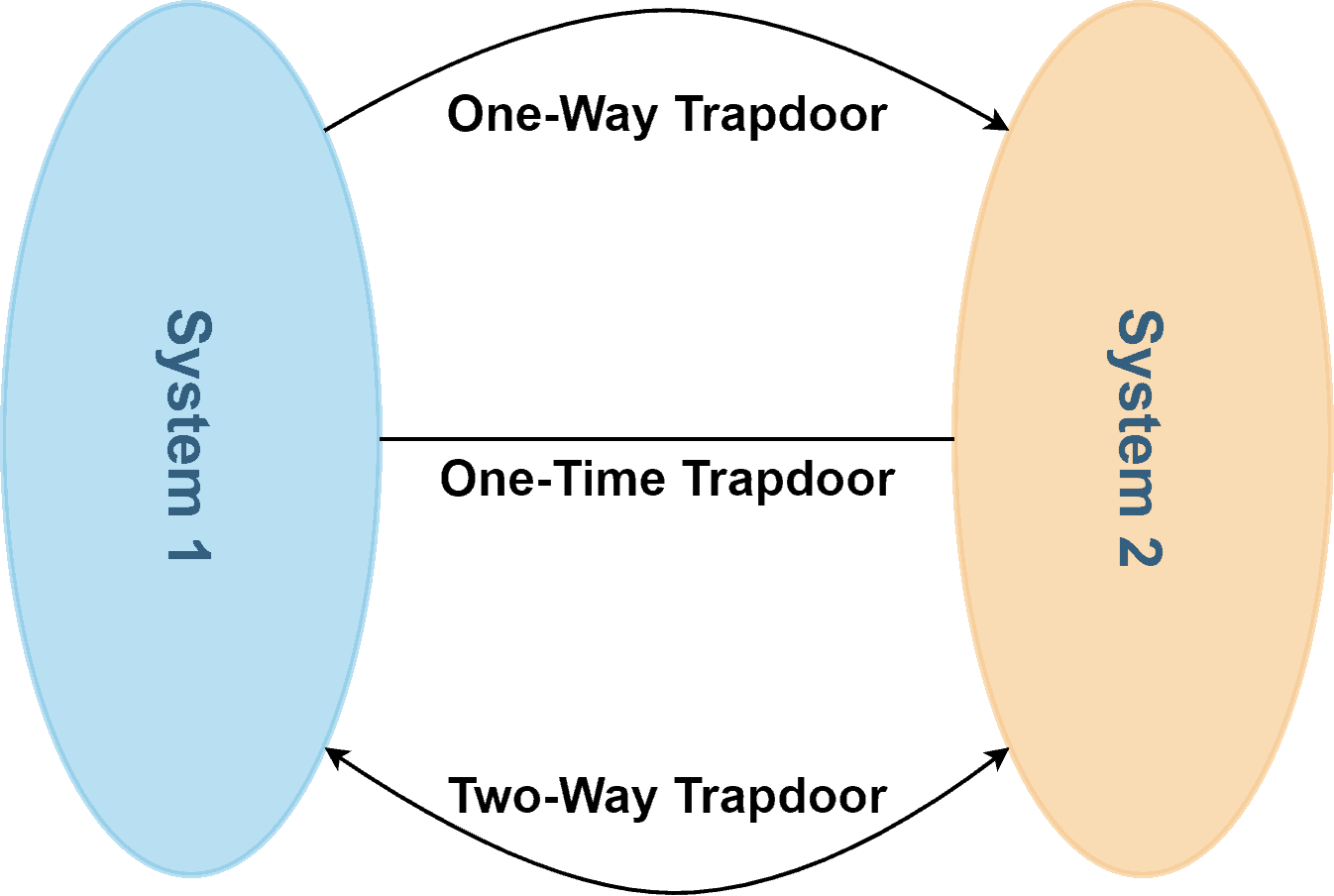
Using a one-way trapdoor, a user from system 1 can enter system 2. Users who don’t belong to system 1 are not allowed to enter system 2. However, a user from system 2 can’t enter system 1. One-time trapdoors are designed to be used only once. In the case of a two-way trapdoor, users from both systems can access each other.
5. Conclusion
In this tutorial, we discussed the trapdoor concept in cryptography.
Furthermore, we explained how trapdoors work and presented different types of trapdoors in cryptography.