Yes, we're now running our Black Friday Sale. All Access and Pro are 33% off until 2nd December, 2025:
Authentication Protocols: PAP vs. CHAP
Last updated: January 16, 2024
1. Overview
In this tutorial, we discuss two authentication protocols developed for Point-to-Point Protocol (PPP), comparatively: the Password Authentication Protocol (PAP) and the Challenge Handshake Authentication Protocol (CHAP).
2. Authentication Protocols
Authentication is the process of checking and verifying the identity of a client. After the verification, the client is allowed access to the system and its facilities. An authentication protocol is designed to transfer authentication data between two entities. These protocols are used to verify the identity of a user, system, or device. The authentication protocols are in the family of computer communications protocols or cryptographic protocols. There are several types of authentication protocols. The following are some of them:
- Authentication protocols developed for PPP (Point-to-Point Protocol)
- AAA architecture protocols (Authentication, Authorization, Accounting)
- Kerberos protocol
Here, we concentrate only on the authentication protocols developed for PPP.
3. Point-to-Point Protocol (PPP)
Point-to-Point Protocol (PPP) is a data link layer protocol that uses authentication methods to identify and validate remote devices. PPP sessions use two authentication methods:
- Password Authentication Protocol (PAP)
- Challenge Handshake Authentication Protocol (CHAP)
PAP and CHAP can also be used with many VPNs.
4. Password Authentication Protocol (PAP)
In this section, we discuss the Password Authentication Protocol (PAP) and its advantages and drawbacks. PAP is a password-based authentication protocol. It is the easiest authentication method. The specialty of PAP is that it is simple and easy to implement. PAP works like a standard login procedure.
There is a two-step process to verify the identity of the client. The remote system uses a fixed pair of a username and a password for authentication. It is better to pass the password through an established encrypted tunnel to increase security.
The two-step process of PAP is as follows. First, the client sends the username and password to the server. Here, the client establishes a PPP session with the server by sending a username and a password to the server. This is performed through an authentication-request packet. Next, the server accepts the requests and verifies them. In this case, it accepts the username and password records and verifies them. If they match correctly, the server sends an authentication-ack response packet to the client and establishes the PPP session between them. Otherwise, the server does not establish a response based on the false credentials:
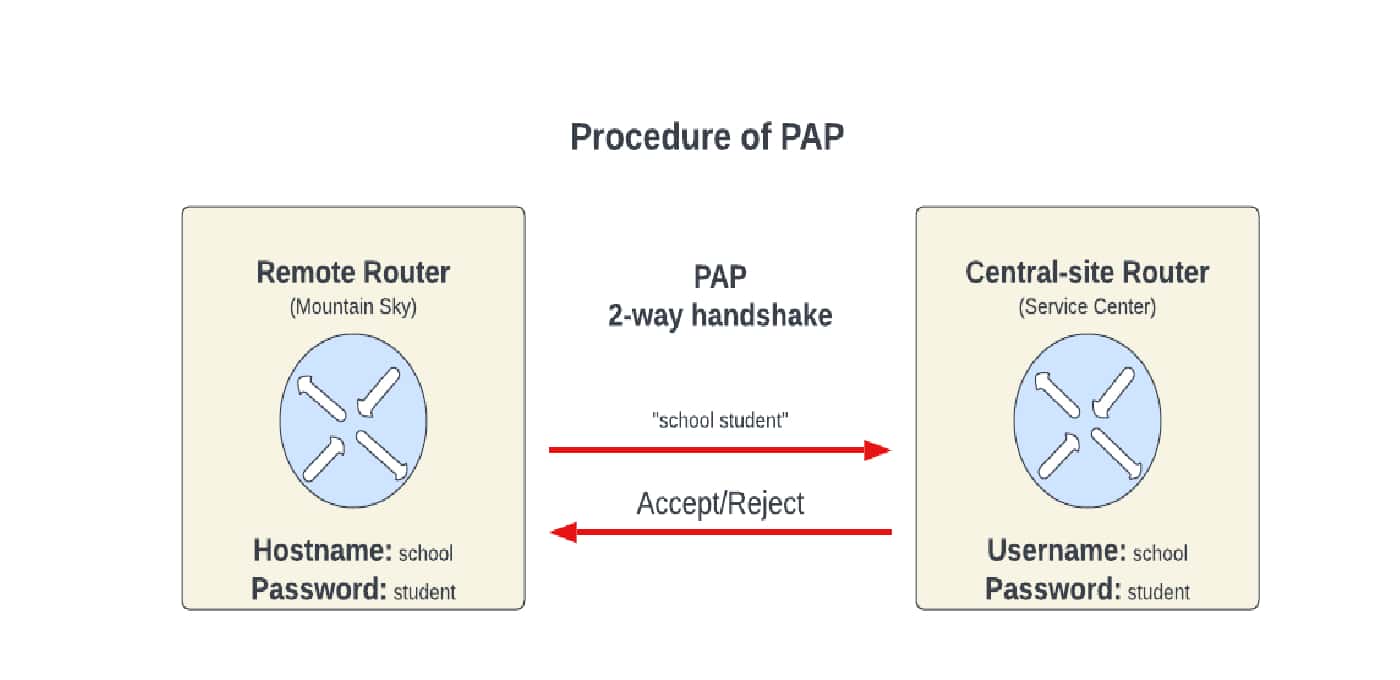
PAP is used at public FTP sites and other public areas. It is vulnerable to many attacks, such as password guessing and snooping. Using PAP, an adversary can find any information associated with PPP, such as a username and password.
4.1. Advantages and Drawbacks of PAP
The advantages and drawbacks of PAP are as follows:
| Advantages | Drawbacks |
| Simplicity | Less security |
| All network operating systems support the authentication process | Week authentication process |
| Non-interactivity | There is no mutual authentication |
| Supports One-Way authentication and Two-Way authentication | Does not encrypt the username and the password during the transmission |
5. Challenge Handshake Authentication Protocol (CHAP)
In this section, we discuss the Challenge Handshake Authentication Protocol (CHAP) and its advantages and drawbacks. CHAP is an encrypted authentication method. The authentication process in CHAP is sophisticated. It has high security. There is a three-step process of exchanging a shared secret to verify the client’s identity. Each authentication generates a random string and creates a unique challenge phrase. One-way hash functions are used to combine this challenge phrase with device hostnames. CHAP can authenticate so that static secret information is not sent over a network.
The three-step process of CHAP is as follows. First, the authenticator sends an authentication challenge and an ask-challenge to the remote user, including a randomly generated challenge string. Then, the client executes a hostname lookup. Here, the client creates an encrypted one-way hash based on the challenge string. In this case, the client uses the password that the client and the server both know. Finally, the server decrypts the hash and verifies it. Here, the server first decrypts the hash. Then, it verifies matching the initial challenge string. If the strings match correctly, it responds with an authentication-success packet. Otherwise, it responds with an authentication failure message and terminates:
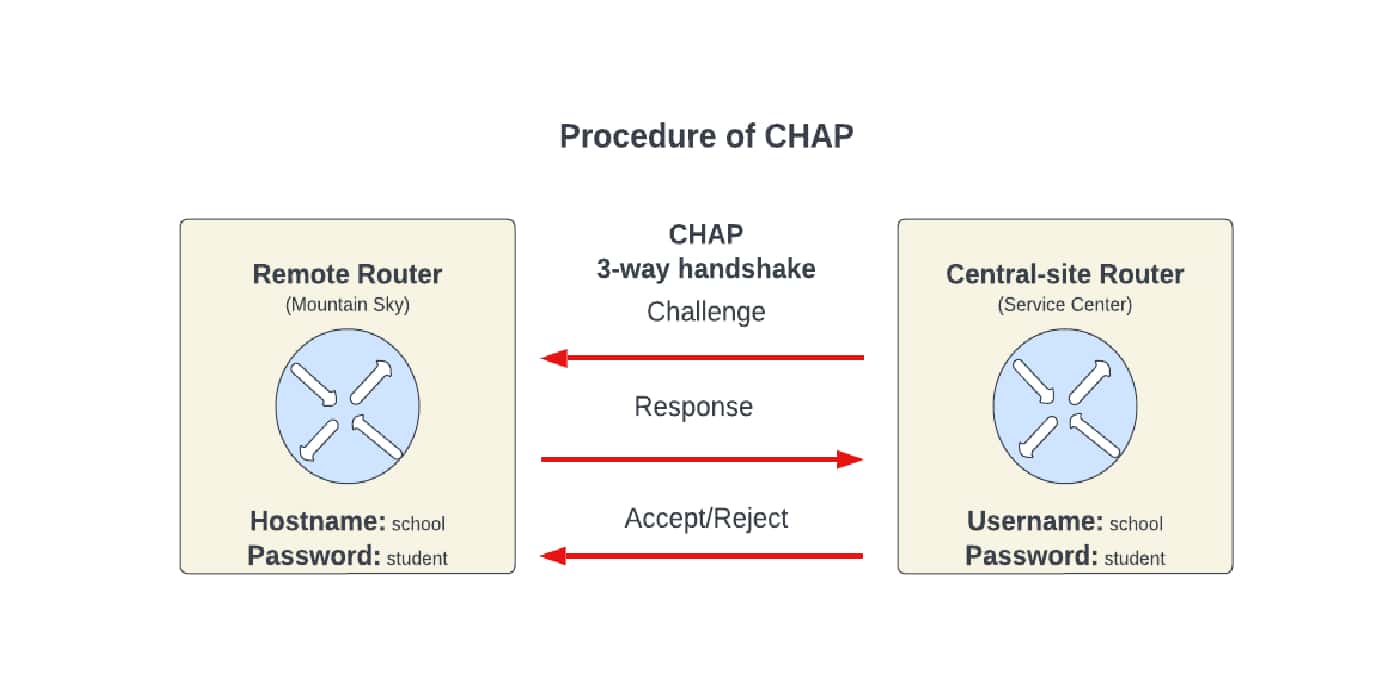
CHAP is widely used on the internet.
5.1. Advantages and Drawbacks of CHAP
The advantages and drawbacks of CHAP are as follows:
| Advantages | Drawbacks |
| More secure than PAP | The requirement of a pre-shared key |
| Flexibility in supporting different authentication methods | CHAP does not offer mutual authentication between the client and the server when only one-way authentication is selected |
| Better Scalability | Vulnerability to attacks such as On-Path Attacks and Dictionary Attacks |
6. Comparisons Between PAP and CHAP
Let’s summarize all the differences and similarities between PAP and CHAP:
| PAP | CHAP |
| Used to authenticate PPP sessions | Used to authenticate PPP sessions |
| Authentication is done only on the client side | Authentication is done on both the client side and the server side |
| The authentication process is common | The authentication process is common |
| It uses a two-way handshake | It uses a three-way handshake |
| It sends the password over a network (without encrypting) | It doesn’t send the password directly over a network |
| No midsession authentications | Sends authentication challenges at regular intervals to ensure the client has not been replaced with an adversary (midsession authentications) |
| Less secure | More secure than PAP |
| Compatible with all network operating systems | It doesn’t support very old systems |
7. Conclusion
In this tutorial, we discussed Point-to-Point Protocol (PPP), which can use either Password Authentication Protocol (PAP) or Challenge Handshake Authentication Protocol (CHAP) for authentication. PAP is simple and supported by all network operating systems. CHAP doesn’t support very old operating systems. It uses cryptographic hash functions to improve security. Considering the security of authentication, CHAP is more secure than PAP. Therefore, if someone uses PAP, it is recommended to use CHAP for other steps in the PPP sessions.