1. Overview
In this tutorial, we’ll discuss the bit stuffing technique in networking with an example.
2. Introduction to Bit Stuffing
Bit stuffing is a process of inserting non-information bits into the data to be transferred. It breaks the data sequence and helps in synchronization.
In the OSI model, the data link layer divides the data received from the physical layer into data frames. A data frame is classified into two categories: fixed-length or variable-length data frame. In variable-length frames, the size of the data frames may vary. In such cases, it’s very difficult to detect the end and beginning of a frame.
Hence bit stuffing is used to mark the end and beginning of the frames during variable-length data frame transfer.
3. Data Frame
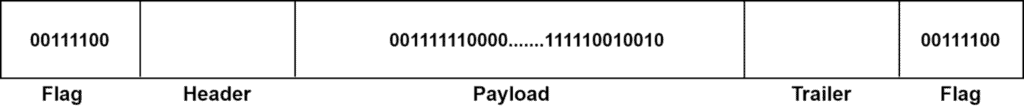
Data frames in a bit-oriented protocol containing a sequence of bits. A data frame has several parts: header, payload, trailer, flag. The header field contains information regarding the source and destination. The payload contains the actual message as a sequence of bits. The trailer field carries error detection and correction bits. The flags hold a bit pattern that makes the end and beginning bits in a data frame.
Let’s look at a data frame:
4. Bit Stuffing Example
Bit stuffing is used for frame management purposes. In variable-length frames, we can define a rule which adds some extra bits in the payload of a frame. These extra added bits don’t carry any information and solely used to mark the end of a bitstream.
For example, we can define a rule that whenever we encounter five consecutive s, an extra
bit is added at the end of the five
s in the bitstream of the payload field.
When the receiver computer receives this message, it detects the extra added bits after each five consecutive 1s in the bitstream and removes them. The unstuffed data is sent in the upper layers for further operations.
Let’s look at an example of bit stuffing:
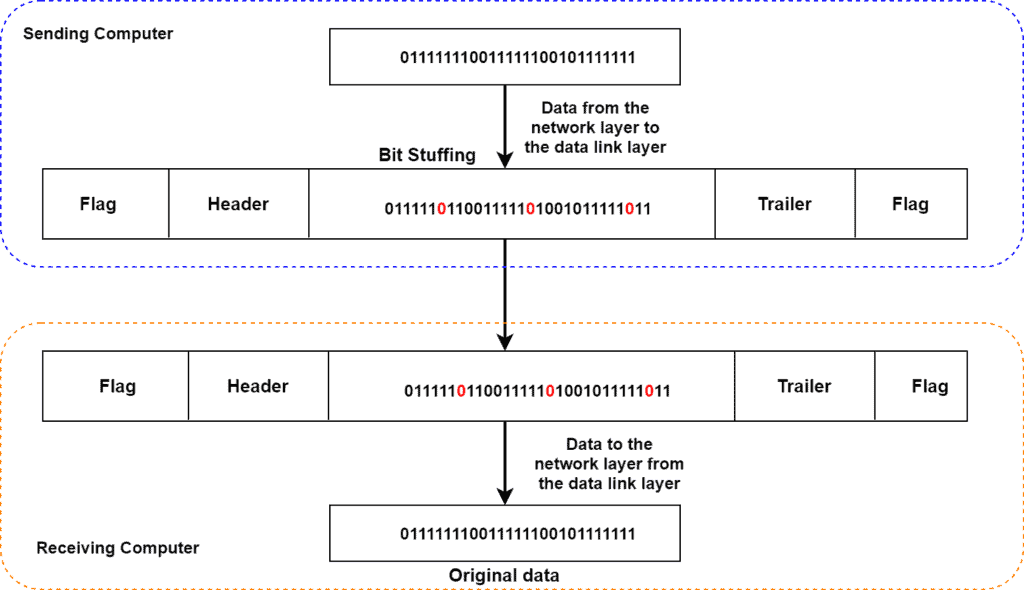
Here the sending computer transmit data to the data link layer which forms a frame from the data received. Using the bit stuffing technique, we added extra bits and send the frame to the receiver computer. When the receiver computer receives the frame, it deletes the extra added bits from the payload and processes further.
5. Advantages and Disadvantages
Bit stuffing helps in the synchronization process and can synchronize multiple channels before multiplexing. It is also useful in run-length limited (RLL) coding.
The disadvantage of bit stuffing is the number of stuffed bits that are not predictable and is fully dependent on the data being received.
5. Conclusion
In this tutorial, we learned bit stuffing in detail. We also presented an example to give the reader a practical essence of the bit stuffing technique.