Yes, we're now running our Black Friday Sale. All Access and Pro are 33% off until 2nd December, 2025:
Webhooks Explained
Last updated: March 18, 2024
1. Overview
There are two methods that an application can use to receive real-time information about specific events happening in another application: polling and webhooks.
In this tutorial, we’ll learn about the two methods and then go into more detail about webhooks.
2. Polling and Webhooks
First, let’s see what they are:
2.1. Polling
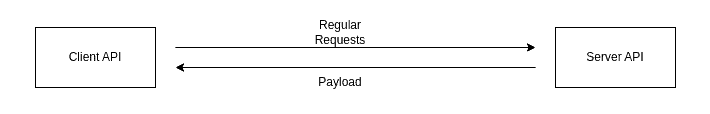
In this method, the client API sends HTTP requests regularly to the server API and asks if a specific event has happened. Once the event occurs, the server API responds with information indicating the event has happened. This information is also called payload and is sent to the client API:
2.2. Webhooks
Webhooks send a message (payload) to the client API when a specific event happens on the server application:

3. More About Webhooks
Now let’s go into more detail about webhooks:
3.1. Comparing Webhooks and Polls
Now let’s compare two methods:
| Polling | Webhooks |
|---|---|
| Slower and use more resources | Faster and more efficient for both sides |
| Require more work on the client’s end | Require less work on the client’s end |
| Data transfer is not automatic | Since they’re event-driven, data transfer is done automatically |
In general, webhooks provide more advantages than polling.
3.2. Use Cases of Webhooks
Any application that needs real-time information about specific events happening on another application can use webhooks:
- If we want to accept online payments in our web app, we can use webhooks to receive real-time data to see if the user has successfully finished the payment on another application, like PayPal
- Receiving notifications about specific events in real-time. For example, receiving notifications on Slack whenever specific events on another application occur
3.3. How Do Webhooks Work?
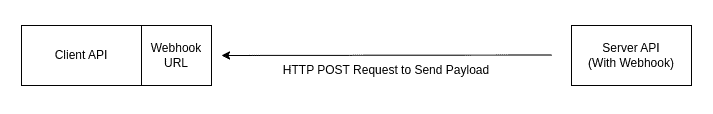
Webhooks need a webhook URL on the client side to be able to send HTTP requests to the client API. The HTTP requests are typically POST requests and need to be interpreted in the client’s backend:
3.4. How Can We Secure Webhooks?
Webhooks send data to the webhook URL in the client application. Further, the webhook URL is available to the public, which means that other than the webhook server, malicious users can also send fake data to the client application. To increase the security of the connection, we can:
- Force HTTPS connection between the server and the client.
- The server can only hash the message with a secret key held by the client and the server. This way, once the client receives the payload and the hash output, it can verify if the server actually sends the payload or not. To verify, the client uses the same hash function again with the same private key and checks if the output matches the one sent by the server.
4. Conclusion
In this article, we learned about different methods of sending information about real-time events between applications.