Learn through the super-clean Baeldung Pro experience:
>> Membership and Baeldung Pro.
No ads, dark-mode and 6 months free of IntelliJ Idea Ultimate to start with.
Last updated: January 3, 2022
In computer security and software development, a sandbox refers to an environment in which a program can run isolated from the rest of your system with limited access to resources. This is useful for testing out parts of a process that may be susceptible to triggering system failures or misbehaving.
When anything happens in a sandbox, it is not supposed to leak onto the rest of the machine. Typically, we can restrain the memory space that the process allocates, the network access that it has (if any), and the directories to which it can have access.
In this article, we explore the different concepts and architectures used to sandbox applications.
Each one of the following architectures will have benefits and flaws. These vary according to their deployment speed, their level of abstraction from hardware components, and the complexity of the system upon which the application needs to run. In general, approaches that segment hardware components at a low level will have better isolation.
In contrast, approaches that abstract the architecture through multiple software levels are more flexible and scalable:
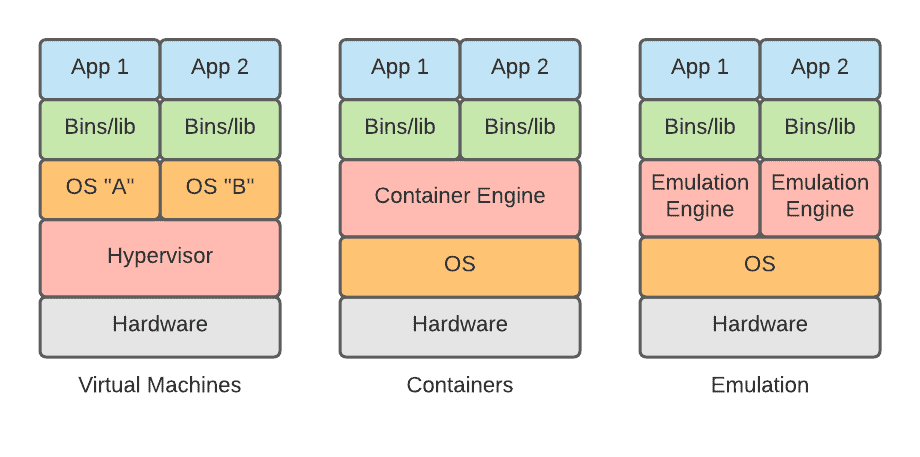
2.1. Virtual Machines & Hypervisors
Firstly, virtual machines (VMs) can be seen as “mini computers” inside the same machine hardware. These different combinations of independent operating systems with separate files, libraries, and applications can all run inside the same computer thanks to hypervisors. Hypervisors are pieces of software or firmware that can distribute the existing hardware resources to each of our different virtual machines.
This process is called “virtualization” and it is similar to setting virtual barriers between different environments on the same computer. Virtual machines take a few minutes to start and are usually slower than containers. However, they provide better isolation between applications.
Moving on from VMs, containers are another way of separating apps. Apps that run on the same OS can be containerized, deployed, and scaled automatically. Containers have grown in popularity recently with the advancement of tools like Docker and computer clustering tools like Kubernetes.
These different applications all run on the same hardware but have different limitations. Container engines are employed to manage network connections, memory, and other resources available to containers. These resources can even be scaled according to the needs of each container.
Because deploying this approach is faster than using virtual machines, containers provide a way to quickly assemble and take apart networks of applications communicating with each other as each one will run in its own little pre-fabricated environment. Containers take seconds to deploy as VMs take minutes.
For this approach, the sandbox will replicate an operating system, but will not emulate any physical hardware. The complete emulation of one operating system can be a heavy task for a computer.
Therefore, a lot of operating system emulation software will only emulate some of the most common system calls.
Advanced types of malware can use infrequent system calls to circumvent this type of sandbox by appearing inactive inside the sandbox.
2.4. Full System Emulation
In full system emulation, all of the resources on your machine will be simulated, in order to provide a look inside and see what the sandboxed process is doing.
Everything from the CPU to the display on the screen is simulated by software and then handed to the sandboxed program. This is similar to containers, only that emulation is not restrained by the operating system architecture of the underlying machine.
Emulation engines can simulate a wide variety of system architectures and are not restrained to personal computers or servers. They can replicate cellphone and video game console operating systems, for example. Because the entire system is emulated, it is possible to analyze the information being sent to the different parts of the computer.
This is used to deeply understand the behavior of the application running inside it.
Clever pieces of malware software will be able to detect the environment in which they are running. By using this skill, different malware can appear safe when running inside a simulated environment and suddenly become active when it detects an actual host.
The malware can then employ different techniques to mask its own tracks. One of the most popular techniques to do this is called process injection. This technique will run a payload code in the same address space as a running process. This will often make it harder to detect the specific process tied to the malware.
Although full system emulation can fix this problem, the quality of the emulation needs to be sufficient to appear as an actual system to the malware.
In this article, we discussed the different fundamental concepts in sandboxing.