Learn through the super-clean Baeldung Pro experience:
>> Membership and Baeldung Pro.
No ads, dark-mode and 6 months free of IntelliJ Idea Ultimate to start with.
Last updated: March 26, 2025
Computer networks enabled several devices to communicate with each other across the world. This communication, however, is not simple and relies on various technical resources, from physical to logical, to occur. Examples of these resources are cables, middleboxes, protocols, and addressing methods. In particular, addressing messages with the proper method is crucial to designing and developing communication systems. The adequate adoption of these methods may guarantee efficient communication among connected devices. However, the incorrect use of them can result in overloaded networks and security problems.
In this tutorial, we’ll study different message addressing methods. First, we’ll see the operational characteristics and real-world usage of available message addressing methods. Next, we’ll approach security remarks regarding attacks intrinsically related to some of these addressing methods. At last, we’ll review the methods in a systematic summary, putting them face to face and highlighting their similarities and differences.
Addressing a message means determining to which destination a source wants to communicate. Considering modern networks, we can describe several messages addressing methods by investigating the receivers of sent messages. The most relevant of these methods are unicast, broadcast, multicast, and anycast. Each addressing method has specific characteristics regarding, for example, the number of receivers, reserved addresses in network protocols, routing strategies, and final applications.
In the following subsections, we’ll in-depth explore multiple aspects of different message addressing methods.
The unicast addressing method indicates that communication through a network involves a unique sender (source) and a single receiver (destination). Making an analogy, we can see unicast communication as a particular conversation with a single person (unicast) at a party with many people (network). Thus, addressing messages with the unicast method supposes private communication. However, since other entities can intercept the messages, employing unicast addressing doesn’t guarantee private communication in the network. In the analogy of a party, similarly, just the fact of talking to a single person doesn’t imply that other people near you will not listen to the conversation.
The following image depicts an abstract communication using unicast addressed messages:
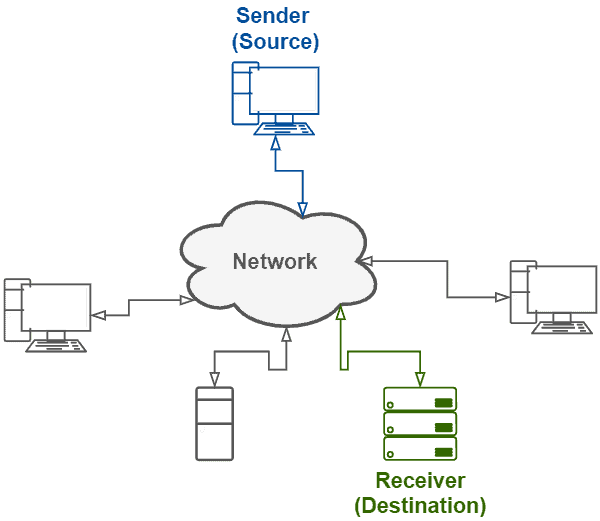
Technically, unicast communication requires the employment of particular addresses. For instance, considering IPv4 networks, addresses from classes A (1.0.0.1 to 126.255.255.254), B (128.1.0.1 to 191.255.255.254), and C (192.0.1.1 to 223.255.254.254) enable unicasting. In IPv6 networks, in turn, unicast addresses are subdivided into global unicast (200::/3), link-local (fe80::/10), loopback (::1/128), unspecified (fc00::/7), and embedded IPv4 (::/80).
Routing messages of a unicast communication in the network is quite simple. Note that the destination is explicitly defined in the unicast messages. Thus, the routers only look up the routing table to forward the message to the next routing node or the destination itself.
Several application protocols employ unicast as the default addressing method. Some examples of these protocols are HTTP, Telnet, FTP, and SMTP. In such a way, we can concretely see unicast communications occurring on everyday use of the network, such as when we browse sites or download files on the Internet.
The broadcast addressing method considers the communication through a network that involves a single sender (source) and multiple receivers (destinations). By default, the broadcast receivers are every device connected to the same network as the sender. So, using the same analogy as for unicast, we can comprehend the broadcast communication as some person (sender) in a party (network) standing up on a table and shouting a message to everyone (receivers) listening.
In our example scenario, probably, it is not expected that shouting a message at a party will result in an interaction with everyone on it. Similarly, broadcasting a message doesn’t imply receiving a response from every device connected to the network. It is relevant to notice that, sometimes, it can happen. However, usually, we receive response messages just from a subgroup of connected devices, a single device, or even receive no response.
The image presented next shows an abstract message broadcasting:
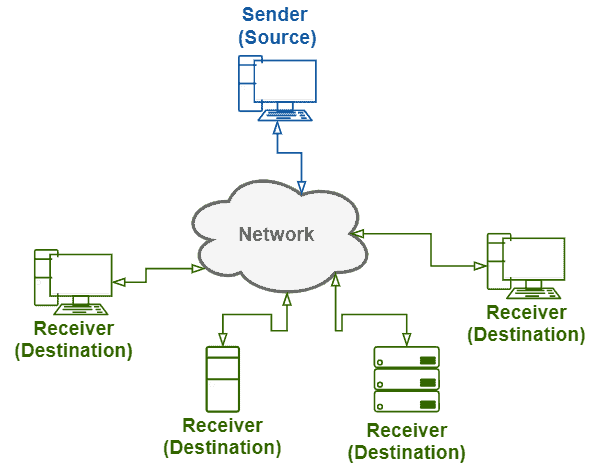
Communication protocols that support broadcasting typically provide reserved addresses to trigger it. So, the messages include these reserved addresses as their destination. For example, considering IPv4 protocol, we find the broadcast address of a specific IP address space (for instance, 192.168.122.0/24) by executing a bitwise complement with the netmask (255.255.255.0 -> 0.0.0.255) and a bitwise OR with the result and the base IP (192.168.122.0 OR 0.0.0.255 -> 192.168.122.255). Another example is ARP protocol, where the broadcast address is FF:FF:FF:FF:FF:FF. Finally, some communication protocols don’t support broadcast addressing, such as IPv6.
In most cases, broadcast messages aren’t routed, being restricted to a single logical network. However, sometimes broadcast domains may be necessary. So, in these scenarios, routers can forward broadcast messages to each host of a broadcast domain using several unicast messages. Alternatively, routers can also flood all their interfaces with broadcast messages.
Broadcast has multiple applications. One relevant example is ARP, which maps dynamic defined IP addresses to permanent physical addresses of devices. DHCP is another example that uses broadcast to enable a client to locate and receive IP offers from the DHCP server in a network. We can identify other examples in protocols of Microsoft’s machine browsing and NTP.
Multicasting addresses messages for a specific group of devices in a network. Note that, even if a group contains all the devices in a network, multicast is theoretically different from the broadcast. This difference consists that, in the multicast case, devices effectively subscribe to receive messages. In the broadcast case, however, devices receive messages regardless of whether or not they want to.
In our party (network) example, we can see multicasting communication as a group of people conversing. A member of the group can talk (sender) and listen (receiver) to other members. Moreover, people become members of the group by choice, and they can abandon the conversation if they are no longer enjoying it. At the party, other people have conversations in other groups, have private conversations, or are quiet in the bar. These people pay no attention to the first referred group.
The following image exemplifies a multicast communication:
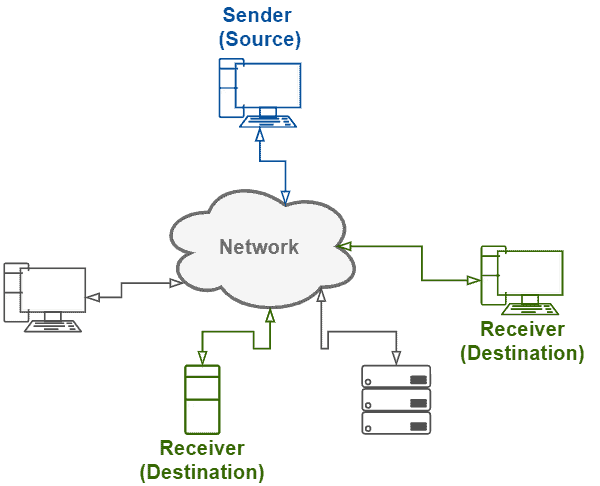
Some patterns in message addresses identify if they are multicast or not. For example, in IPv4, the most significant four bits determine if an address is a multicast one or not. In this case, multicast addresses must present the bit sequence of 1110. IPv6 is another protocol that supports multicast. In this protocol, multicast addresses use the prefix ff00::/8.
We can comprehend multicast routing as a particular case of broadcast routing. However, the challenge here is that routers must transmit the messages only for the hosts that want to receive them (members of a multicast group). Thus, strategies based on spanning trees create loop-free routes from a source to all destinations. With these routes, routers transmit a message concurrently to all the members of a multicast group.
Several systems employ multicast with different purposes. One relevant example is multimedia delivering systems. In this scenario, IPTV and video conference applications make frequent use of multicast to transmit data. Another example is the multicast transmission in Windows Deployment Services (WDS). Multicast in WDS enables the server to deploy multiple windows clients with a single data stream, efficiently using the available network.
The anycast addressing method forwards messages to a single device of a specific group of devices. Typically, considering the sender’s position, the topologically nearest device of the aimed anycast group will receive the message. In our party (network) example, we can comprehend anycast communication when a person (sender) will leave the party but first wants to say goodbye to the hosts (anycast group). As the party is going on and most of the hosts are occupied with several guests, it is okay to say goodbye to a single one. So, the person looks around and finds the closest party host (destination), thanks for the party, and goes away.
The image next shows an abstract example of an anycast communication:
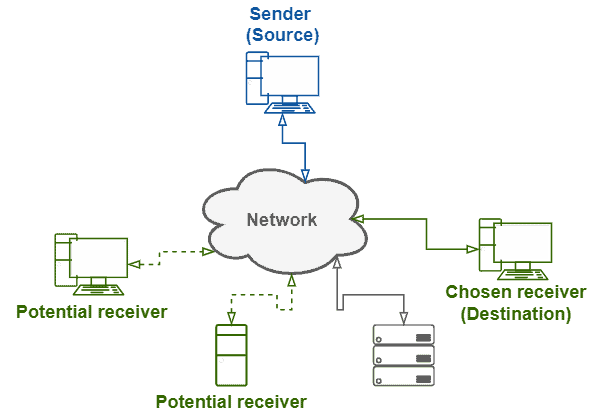
In practice, there is no exclusive address range for anycast. Thus, we form anycast groups by assigning the same unicast address to multiple devices in a network. Of course, we should configure the devices, thus making them aware of being members of an anycast group.
The anycast routing is, generally, the same as unicast routing. In this scenario, DNS servers along the way can help to define which device of an anycast group should receive the traffic. In official terms, IPv4 doesn’t support anycast. However, modifications on the BGP protocol can enable a kind of IPv4 anycast routing in the core network. IPv6, in turn, supports anycast natively. Generally, in such a case, routers don’t distinguish unicast addressing from anycast addressing. The exception is only the routers near the potential anycast destinations, which execute special handlings of anycast traffic.
Real-world applications of anycast addressing include DNS querying and efficient content delivery. Several DNS servers use anycast addresses to provide a redundant service with improved performance on querying addresses. Content delivery networks have similar purposes for using anycast. In this scenario, content servers are disposed of in strategic locations according to the client’s demand. So, anycasting requests permit the access of the most appropriate content server according to the clients’ current location.
Specific attacks use operational characteristics of addressing methods to achieve a malicious goal. In this section, we’ll see some of these attacks and how they exploit the addressing methods. Our scope, however, does not consider generic attacks, such as simple flooding denial of service or man in the middle, that are independent of the adopted addressing method. Our focus is on attacks variations that can explicitly benefit from characteristics of broadcast and multicast to operate:
At last, it is relevant to notice that there are countermeasures to avoid these attacks. These countermeasures should be observed while implementing networked systems and configuring networks.
Generally, the most prominent characteristic of different addressing methods is how a source relates to one or more destinations. Thus, we can classify the addressing methods regarding how many potential destinations are available to a specific message and how many destinations actually receive the message. The following table recaps the studied addressing methods through these characteristics:
| Message Addressing Methods | |||
|---|---|---|---|
| Method | Source-to- Destination | How many potential destinations? | How many destinations receive the message? |
| Unicast | One-to-One | One | One |
| Broadcast | One-to-All | Multiple | Multiple |
| Multicast | One-to-Many | Multiple | Multiple |
| Anycast | One-to-Any | Multiple | One |
In this article, we learned about message addressing methods. First, we studied the available message addressing methods, observing their characteristics regarding operational behavior, address formating, message routing, and examples of applications. Then, we investigated potential security issues related to attacks that exploit some of the addressing methods. Finally, we reviewed the addressing methods and briefly compared them through their main differentiating characteristic: the message destinations.
We can conclude that message addressing methods represent vast opportunities for developing networked systems. With the proper software engineering and correct practical use of addressing methods, systems can communicate in the network with improved efficiency, reliability, and security.